filmov
tv
OWASP Top 10 - 2021 | Try Hack Me Full Walkthrough

Показать описание
Welcome to our in-depth walkthrough of the OWASP Top 10 room on Try Hack Me! 🛡️ Cybersecurity enthusiasts and ethical hackers, this is your chance to dive into the world of web application security and learn how to protect against the most critical vulnerabilities identified by the Open Web Application Security Project (OWASP).
In this comprehensive video tutorial, we'll cover the following key topics:
Introduction to OWASP Top 10: We'll begin by explaining what the OWASP Top 10 is and why it's crucial for web developers, security professionals, and anyone interested in safeguarding web applications.
Injection Attacks: Dive into the world of injection attacks like SQL injection and learn how to prevent malicious input from compromising your web applications.
Broken Authentication: Understand the importance of secure user authentication and explore common flaws in authentication systems.
Sensitive Data Exposure: Learn how to protect sensitive data from unauthorized access, including best practices for encryption and data storage.
XML External Entity (XXE) Attacks: Delve into XML-related vulnerabilities and discover how to prevent XXE attacks from exploiting your web services.
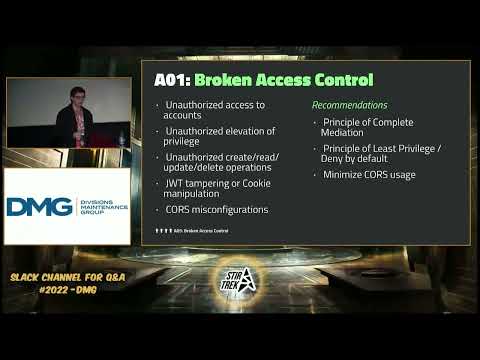
Broken Access Control: Explore the significance of proper access control mechanisms and how to implement them effectively to prevent unauthorized access.
Security Misconfigurations: Identify and address common security misconfigurations that can leave your web applications vulnerable to attacks.
Cross-Site Scripting (XSS): Learn about XSS vulnerabilities, their impact, and mitigation techniques to prevent malicious script injections.
Insecure Deserialization: Understand the risks associated with insecure deserialization and discover how to secure your applications against these threats.
Using Components with Known Vulnerabilities: Explore strategies for managing third-party components and libraries with known vulnerabilities to maintain a secure application.
Throughout this walkthrough, we'll provide practical demonstrations, hands-on examples, and expert tips to help you grasp each OWASP Top 10 vulnerability concept. By the end of this video, you'll have a strong foundation in web application security and be better equipped to defend against cyber threats.
Video Chapters
0:00 - Intro
0:20 - Task 1, 2 & 3
0:52 - Task 4
1:57 - Task 5
2:07 - Task 6 & 7
2:36 - Task 8
5:22 - Task 9 & 10
7:35 - Task 11
9:02 - Task 12
10:32 - Task 13 & 14
11:09 - Task 15
12:33 - Task 16
12:57 - Task 17
14:23 - Task 18
14:49 - Task 19
15:37 - Task 20
17:50 - Task 21
18:25 - Task 22
20:33 - Task 23 & Outro
In this comprehensive video tutorial, we'll cover the following key topics:
Introduction to OWASP Top 10: We'll begin by explaining what the OWASP Top 10 is and why it's crucial for web developers, security professionals, and anyone interested in safeguarding web applications.
Injection Attacks: Dive into the world of injection attacks like SQL injection and learn how to prevent malicious input from compromising your web applications.
Broken Authentication: Understand the importance of secure user authentication and explore common flaws in authentication systems.
Sensitive Data Exposure: Learn how to protect sensitive data from unauthorized access, including best practices for encryption and data storage.
XML External Entity (XXE) Attacks: Delve into XML-related vulnerabilities and discover how to prevent XXE attacks from exploiting your web services.
Broken Access Control: Explore the significance of proper access control mechanisms and how to implement them effectively to prevent unauthorized access.
Security Misconfigurations: Identify and address common security misconfigurations that can leave your web applications vulnerable to attacks.
Cross-Site Scripting (XSS): Learn about XSS vulnerabilities, their impact, and mitigation techniques to prevent malicious script injections.
Insecure Deserialization: Understand the risks associated with insecure deserialization and discover how to secure your applications against these threats.
Using Components with Known Vulnerabilities: Explore strategies for managing third-party components and libraries with known vulnerabilities to maintain a secure application.
Throughout this walkthrough, we'll provide practical demonstrations, hands-on examples, and expert tips to help you grasp each OWASP Top 10 vulnerability concept. By the end of this video, you'll have a strong foundation in web application security and be better equipped to defend against cyber threats.
Video Chapters
0:00 - Intro
0:20 - Task 1, 2 & 3
0:52 - Task 4
1:57 - Task 5
2:07 - Task 6 & 7
2:36 - Task 8
5:22 - Task 9 & 10
7:35 - Task 11
9:02 - Task 12
10:32 - Task 13 & 14
11:09 - Task 15
12:33 - Task 16
12:57 - Task 17
14:23 - Task 18
14:49 - Task 19
15:37 - Task 20
17:50 - Task 21
18:25 - Task 22
20:33 - Task 23 & Outro
Комментарии
 0:08:51
0:08:51
 1:40:30
1:40:30
 0:08:57
0:08:57
 0:33:36
0:33:36
 0:14:21
0:14:21
 0:20:40
0:20:40
 1:00:59
1:00:59
 0:13:33
0:13:33
 0:14:58
0:14:58
 0:06:22
0:06:22
 1:12:16
1:12:16
 0:41:26
0:41:26
 0:15:32
0:15:32
 0:10:35
0:10:35
 0:15:55
0:15:55
 0:18:47
0:18:47
 1:42:39
1:42:39
 0:02:14
0:02:14
 0:11:48
0:11:48
 0:23:26
0:23:26
 0:19:41
0:19:41
 0:54:40
0:54:40
 0:01:24
0:01:24
 0:01:33
0:01:33