filmov
tv
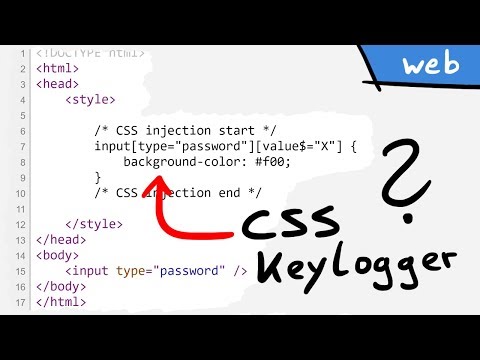
CSS Keylogger - old is new again

Показать описание
This is "well known" research that resurfaces every other year. Let me tell you a story how I have heard about this in 2012 and putting it into perspective.
Research "Scriptless Attacks –
Stealing the Pie Without Touching the Sill" (2012):
Twitter:
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#SecurityResearch
Research "Scriptless Attacks –
Stealing the Pie Without Touching the Sill" (2012):
Twitter:
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#SecurityResearch
CSS Keylogger - old is new again
CSS Keylogger Demo
#Hacktivity2021 // CSS Keylogger in 2021 - The Hubris of the Security Community
NEVER buy from the Dark Web.. #shorts
Hello World in different programming languages #programming #memes
When you first time install Kali linux for hacking 😄😄 #hacker #shorts
Unknown Keylogger 1.3 [FullHD 1080p]
Free Hacking Classes | Best Hacking Guruji #hacking #cybersecurity #hacker #ethicalhacking
How to Use Vencord and Plugins (Like Better Discord but Pretty Legit)
They have been keylogging you for YEARS
13 yr old Heckur 😂 #shorts #ytshorts #trending #viral #fade #verified #hacker #anonymous
How to Create a Key Logger in the Backdoor shell
Keylogger li Site
CSS || Clear Wallhacking EXPLOIT **NEW 2011**
JavaScript Keylogger
Free INIURIA CS:S Hack [CRACKED] [FREE DOWNLOADLINK]
everything is open source if you can reverse engineer (try it RIGHT NOW!)
1345
Xenotix XSS reflected DVWA - Exploitation - Keylogger
How to study source codes: Adding a keylogger to the Bash
Keylogger 2018
Python 🔐 Keylogger | Bypass Windows Defender & Antivirus | #keylogger #hacking #kalilinux
Keylogger , Fake Login
Program/Develop/Code a Keylogger in Python
Комментарии
 0:11:29
0:11:29
 0:00:57
0:00:57
 0:24:22
0:24:22
 0:00:46
0:00:46
 0:00:32
0:00:32
 0:00:32
0:00:32
 0:11:12
0:11:12
 0:00:16
0:00:16
 0:03:08
0:03:08
 0:06:02
0:06:02
 0:00:14
0:00:14
 0:06:55
0:06:55
 0:00:53
0:00:53
 0:01:35
0:01:35
 0:01:26
0:01:26
 0:00:30
0:00:30
 0:13:56
0:13:56
 0:00:11
0:00:11
 0:00:57
0:00:57
 0:37:16
0:37:16
 0:08:20
0:08:20
 0:00:31
0:00:31
 0:06:44
0:06:44
 0:29:56
0:29:56