filmov
tv
Identity and Access Management | Cyber Security Training | Edureka | Cyber security Live - 1

Показать описание
This Edureka "Identity and Access Management" video will give you an understanding of the fundamentals of Identity, Authentication & Authorization.
------------------------------------Edureka Online Training and Certification---------------------------------
-----------------------------------------Edureka Masters Programs---------------------------------------------------
-----------------------------------------Edureka PGP Courses---------------------------------------------------
-----------------------------------------------------------------------------------------------------------
#edureka #CyberSecurityEdureka #TypesofCyberThreats #CybersecurityThreats #Cybersecurity #learnCybersecurity #withMe
------------------------------------------------
About Edureka Cyber Security Training
Cybersecurity is the combination of processes, practices, and technologies designed to protect networks, computers, programs, data and information from attack, damage or unauthorized access.
Edureka’s Cybersecurity Certification Course will help you in learning about the basic concepts of Cybersecurity along with the methodologies that must be practiced ensuring information security of an organization. Starting from the Ground level Security Essentials, this course will lead you through Cryptography, Computer Networks & Security, Application Security, Data & Endpoint Security, idAM (Identity & Access Management), Cloud Security, Cyber-Attacks and various security practices for businesses.
------------------------------------------------
Why Learn Cyber Security?
Cybersecurity is the gathering of advances that procedures and practices expected to ensure systems, PCs, projects and information from assault, harm or unapproved get to. In a processing setting, security incorporates both cybersecurity and physical security, it is imperative since cyberattackers can without much of a stretch take and obliterate the profoundly grouped data of governments, defense offices and banks for which the results are huge so it is essential to have an appropriate innovation which an avoid digital wrongdoings.
--------------------------------------
Who Should go for this Training?
Anyone having the zeal to learn innovative technologies can take up this course. Especially, students and professionals aspiring to make a career in Cybersecurity technology. However, Cybersecurity Certification Course is best suited for the below-mentioned profiles:-
Networking Professionals
Linux Administrators
-----------------------------------------------
------------------------------------Edureka Online Training and Certification---------------------------------
-----------------------------------------Edureka Masters Programs---------------------------------------------------
-----------------------------------------Edureka PGP Courses---------------------------------------------------
-----------------------------------------------------------------------------------------------------------
#edureka #CyberSecurityEdureka #TypesofCyberThreats #CybersecurityThreats #Cybersecurity #learnCybersecurity #withMe
------------------------------------------------
About Edureka Cyber Security Training
Cybersecurity is the combination of processes, practices, and technologies designed to protect networks, computers, programs, data and information from attack, damage or unauthorized access.
Edureka’s Cybersecurity Certification Course will help you in learning about the basic concepts of Cybersecurity along with the methodologies that must be practiced ensuring information security of an organization. Starting from the Ground level Security Essentials, this course will lead you through Cryptography, Computer Networks & Security, Application Security, Data & Endpoint Security, idAM (Identity & Access Management), Cloud Security, Cyber-Attacks and various security practices for businesses.
------------------------------------------------
Why Learn Cyber Security?
Cybersecurity is the gathering of advances that procedures and practices expected to ensure systems, PCs, projects and information from assault, harm or unapproved get to. In a processing setting, security incorporates both cybersecurity and physical security, it is imperative since cyberattackers can without much of a stretch take and obliterate the profoundly grouped data of governments, defense offices and banks for which the results are huge so it is essential to have an appropriate innovation which an avoid digital wrongdoings.
--------------------------------------
Who Should go for this Training?
Anyone having the zeal to learn innovative technologies can take up this course. Especially, students and professionals aspiring to make a career in Cybersecurity technology. However, Cybersecurity Certification Course is best suited for the below-mentioned profiles:-
Networking Professionals
Linux Administrators
-----------------------------------------------
Комментарии
 0:09:11
0:09:11
 0:31:15
0:31:15
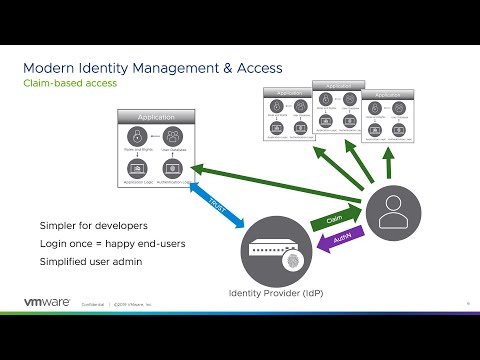 0:17:53
0:17:53
 0:03:37
0:03:37
 0:12:46
0:12:46
 0:01:18
0:01:18
 1:15:22
1:15:22
 0:07:28
0:07:28
 0:55:03
0:55:03
 0:03:00
0:03:00
 0:15:38
0:15:38
 1:31:08
1:31:08
 0:19:13
0:19:13
 0:40:11
0:40:11
 0:56:45
0:56:45
 0:27:47
0:27:47
 0:06:39
0:06:39
 0:05:41
0:05:41
 0:30:57
0:30:57
 0:06:13
0:06:13
 0:45:27
0:45:27
 0:05:27
0:05:27
 2:43:29
2:43:29
 0:24:36
0:24:36