filmov
tv
Token-based Authentication for Web APIs: Access Tokens and Refresh Tokens
Показать описание
Welcome to our comprehensive guide on Token-based Authentication for Web APIs, focusing on Access Tokens and Refresh Tokens! In today's digital landscape, securing APIs is paramount, and Token-based Authentication offers an effective solution. This video aims to provide you with a detailed explanation of Token-based Authentication, including the concepts of Access Tokens and Refresh Tokens, their workings, benefits, and implementation.
**Key Points Covered:**
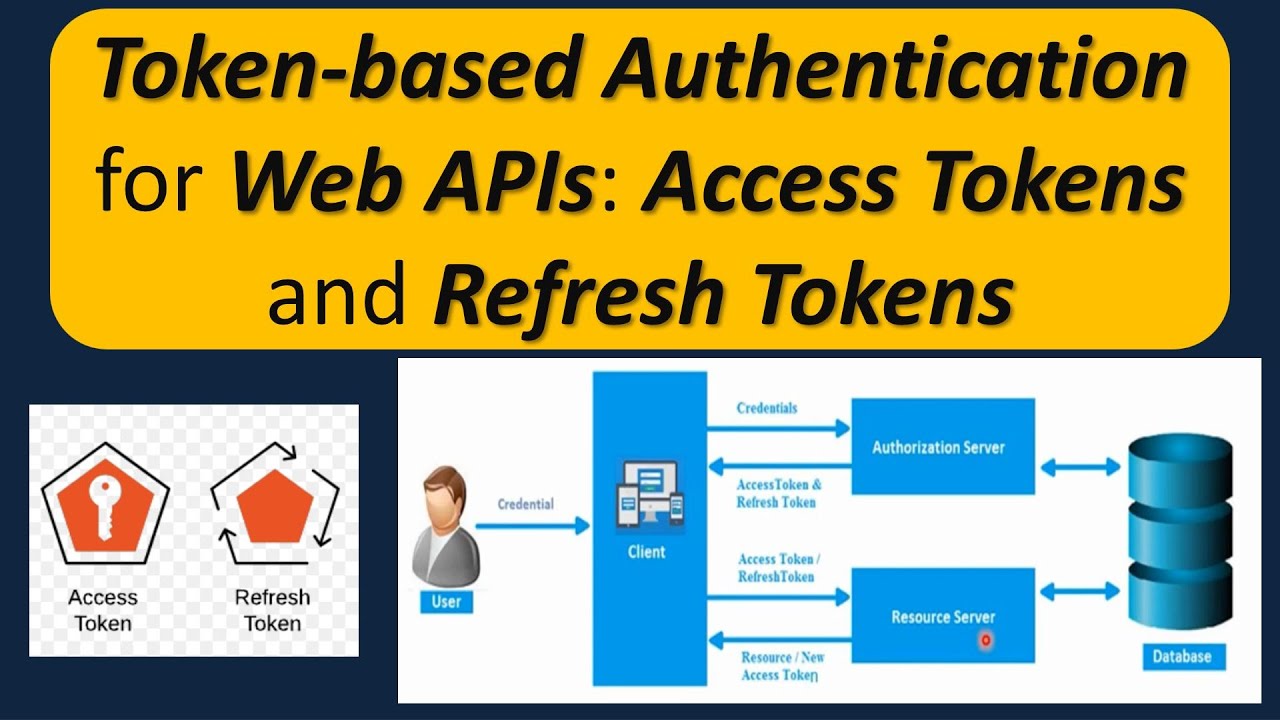
1. **Introduction to Token-based Authentication:** We kick off by introducing the concept of Token-based Authentication and its significance in securing Web APIs. Learn how this authentication method allows clients to authenticate themselves using tokens instead of traditional credentials like usernames and passwords.
2. **Access Tokens Explained:** Dive into the mechanics of Access Tokens. Understand how Access Tokens are securely generated and issued by an authentication server upon successful authentication. Explore how these tokens are included in API requests to grant access to protected resources.
3. **Refresh Tokens Explained:** Explore the workings of Refresh Tokens. Learn how Refresh Tokens are used to obtain new Access Tokens without requiring users to re-enter their credentials. Understand the role of Refresh Tokens in enhancing security and user experience.
4. **Token Lifecycle:** Gain insights into the lifecycle of Access Tokens and Refresh Tokens. Understand how Access Tokens expire after a certain period and how Refresh Tokens can be used to obtain new Access Tokens when they expire or become invalid.
5. **Benefits of Token-based Authentication:** Discover the benefits of using Token-based Authentication for securing Web APIs. From improved security to better scalability and flexibility, Token-based Authentication offers several advantages for developers and system administrators.
6. **Implementing Token-based Authentication:** Gain practical insights into implementing Token-based Authentication securely. Learn how to generate, validate, and manage Access Tokens and Refresh Tokens, as well as handle token expiration and revocation.
7. **Best Practices:** Explore best practices for implementing Token-based Authentication effectively. From token storage to token transmission and token revocation, understand key considerations for ensuring the security and reliability of your authentication system.
Whether you're a web developer, system administrator, or API enthusiast, understanding Token-based Authentication, Access Tokens, and Refresh Tokens is essential for building secure and reliable Web APIs. Subscribe to our channel for more tutorials, guides, and insights on API security and authentication methods. Like, share, and comment to join the conversation and stay updated on the latest developments in API security practices. Thank you for watching!
Token-based Authentication for Web APIs: Access Tokens and Refresh Tokens
Click the below link to download the Java Source code and PPT:
Click the below Github link to download the Java Source code and PPT:
Click the below Bitbucket link to download the Java Source code and PPT:
#TokenBasedAuthentication #WebAPIs #AccessRefreshTokens #APISecurity #AuthenticationMethods #WebDevelopment #SoftwareDevelopment #DigitalSecurity #InternetSecurity #Cybersecurity
**Key Points Covered:**
1. **Introduction to Token-based Authentication:** We kick off by introducing the concept of Token-based Authentication and its significance in securing Web APIs. Learn how this authentication method allows clients to authenticate themselves using tokens instead of traditional credentials like usernames and passwords.
2. **Access Tokens Explained:** Dive into the mechanics of Access Tokens. Understand how Access Tokens are securely generated and issued by an authentication server upon successful authentication. Explore how these tokens are included in API requests to grant access to protected resources.
3. **Refresh Tokens Explained:** Explore the workings of Refresh Tokens. Learn how Refresh Tokens are used to obtain new Access Tokens without requiring users to re-enter their credentials. Understand the role of Refresh Tokens in enhancing security and user experience.
4. **Token Lifecycle:** Gain insights into the lifecycle of Access Tokens and Refresh Tokens. Understand how Access Tokens expire after a certain period and how Refresh Tokens can be used to obtain new Access Tokens when they expire or become invalid.
5. **Benefits of Token-based Authentication:** Discover the benefits of using Token-based Authentication for securing Web APIs. From improved security to better scalability and flexibility, Token-based Authentication offers several advantages for developers and system administrators.
6. **Implementing Token-based Authentication:** Gain practical insights into implementing Token-based Authentication securely. Learn how to generate, validate, and manage Access Tokens and Refresh Tokens, as well as handle token expiration and revocation.
7. **Best Practices:** Explore best practices for implementing Token-based Authentication effectively. From token storage to token transmission and token revocation, understand key considerations for ensuring the security and reliability of your authentication system.
Whether you're a web developer, system administrator, or API enthusiast, understanding Token-based Authentication, Access Tokens, and Refresh Tokens is essential for building secure and reliable Web APIs. Subscribe to our channel for more tutorials, guides, and insights on API security and authentication methods. Like, share, and comment to join the conversation and stay updated on the latest developments in API security practices. Thank you for watching!
Token-based Authentication for Web APIs: Access Tokens and Refresh Tokens
Click the below link to download the Java Source code and PPT:
Click the below Github link to download the Java Source code and PPT:
Click the below Bitbucket link to download the Java Source code and PPT:
#TokenBasedAuthentication #WebAPIs #AccessRefreshTokens #APISecurity #AuthenticationMethods #WebDevelopment #SoftwareDevelopment #DigitalSecurity #InternetSecurity #Cybersecurity
 0:02:18
0:02:18
 0:20:25
0:20:25
 0:03:07
0:03:07
 0:26:29
0:26:29
 0:14:53
0:14:53
 0:01:12
0:01:12
 0:21:27
0:21:27
 2:22:41
2:22:41
 0:05:07
0:05:07
 0:09:01
0:09:01
 0:14:53
0:14:53
 1:02:05
1:02:05
 0:32:46
0:32:46
 0:17:26
0:17:26
 0:25:21
0:25:21
 0:05:13
0:05:13
 0:01:51
0:01:51
 0:11:53
0:11:53
 0:01:16
0:01:16
 0:53:11
0:53:11
 0:27:36
0:27:36
 0:23:05
0:23:05
 0:15:19
0:15:19
 0:16:01
0:16:01