filmov
tv
The Age of Universal XSS

Показать описание
In August 1996, Internet Explorer joined the JavaScript security scene after they added JScript. During this era from around 1996-2000, tons of bugs were found what we would call today "Universal Cross-site Scripting". I find this word confusing, but looking back at the history, we can try to make sense of it.
Episode 03:
00:00 - Intro to the "Age of Universal XSS"
01:16 - JavaScript Security in Netscape 1996
01:52 - JScript Vulnerability in Internet Explorer
03:38 - Georgi Guninski: IE can read local files (1998)
05:12 - Who is Georgi Guninski?
06:36 - Georgi Guninski: IE 5 circumventing cross-frame security policy
09:41 - David Ross from Microsoft about Georgi
10:16 - "Cross-Frame" Browser Bugs
11:17 - Universal Cross-Site Scripting
12:15 - Outro
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
Episode 03:
00:00 - Intro to the "Age of Universal XSS"
01:16 - JavaScript Security in Netscape 1996
01:52 - JScript Vulnerability in Internet Explorer
03:38 - Georgi Guninski: IE can read local files (1998)
05:12 - Who is Georgi Guninski?
06:36 - Georgi Guninski: IE 5 circumventing cross-frame security policy
09:41 - David Ross from Microsoft about Georgi
10:16 - "Cross-Frame" Browser Bugs
11:17 - Universal Cross-Site Scripting
12:15 - Outro
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
The Age of Universal XSS
$750 Bounty for Universal XSS | BRAVE
Universal XSS, Open redirect in HackerOne unofficial Android App
XSSPwn - Cross Site Scripting XSS Automatic Scanner
XSS: How To Look For XSS - HackALong
Why proofing impact for every XSS is 'dumb' - Bug Bounty Reports
XSS History and Conclusion - Jim Manico
Do you know what XSS is?
The Origin of Cross-Site Scripting (XSS) - Hacker Etymology
November 9, 2022
Tracking Origins of Hackers Start Gmail on iPad XSS 20191001
Easy Way To Find cross-site scripting (xss) | #shorts #shortsvideo | #bugbounty
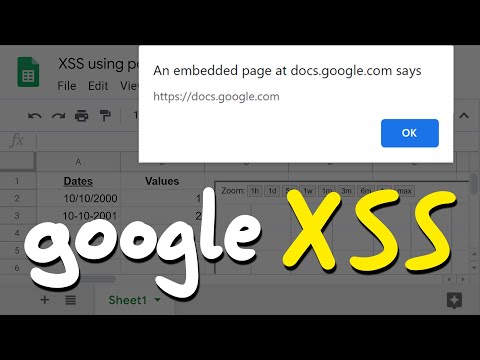
Script Gadgets! Google Docs XSS Vulnerability Walkthrough
🏃💨 Subway Surfers - Official Launch Trailer
What is XSS/Cross-Site Scripting? // Featuring XSS Rat
The Same Origin Policy - Hacker History
The Future Of Hacking #shorts
X-SS
The Three JavaScript Hacking Legends
Dani & Gigi -Move In
DEF CON 30 - Dongsung Kim - CSRF Resurrections Starring the Unholy Trinity
Seatbelts for Web App (Security Headers)
XSS-уязвимости
Diana and Roma Funny Kids Adventure stories / Video compilation
Комментарии
 0:12:35
0:12:35
 0:00:11
0:00:11
 0:00:40
0:00:40
 0:05:35
0:05:35
 0:06:00
0:06:00
 0:04:47
0:04:47
 0:13:38
0:13:38
 0:13:42
0:13:42
 0:14:21
0:14:21
 0:00:16
0:00:16
 0:00:16
0:00:16
 0:00:55
0:00:55
 0:18:57
0:18:57
 0:01:06
0:01:06
 0:09:40
0:09:40
 0:12:19
0:12:19
 0:00:58
0:00:58
 0:02:02
0:02:02
 0:11:59
0:11:59
 0:00:46
0:00:46
 0:39:55
0:39:55
 0:51:32
0:51:32
 1:02:02
1:02:02
 0:31:14
0:31:14