filmov
tv
vCenter Server two-factor authentication configuration

Показать описание
An in depth look at VMware vSphere vCenter Server two-factor authentication configuration using Duo Security. Why do you need to secure your VMware vCenter Server with 2FA? It is simple. Attackers are looking to compromise your vSphere environment and other business-critical infrastructure. By securing your network with multi-factor authentication, specifically two-factor, you will be able to bolster the security of your vSphere login.
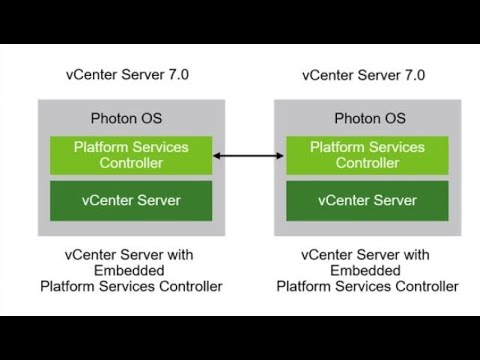
While vSphere 7 adds the new identity federation capability in vCenter Server, currently this is only supported with Active Directory Federation Services (ADFS). If you don't currently have ADFS in your environment it can be overkill to setup ADFS just for two-factor authentication for vCenter. Also, you may be running an older vSphere version such as vSphere 6.5 or 6.7.
Using Duo Security and the Duo authentication proxy, you can easily configure two-factor authentication on your vCenter Server and require 2FA for all vCenter Active Directory logins. This is accomplished by proxying all the authentication requests to Active Directory through your Duo authentication proxy.
_____________________________________________________
Introduction to cybersecurity and challenges - 0:00-0:44
Why is two-factor authentication important? - 0:55
Introduction to Duo Security - 1:55
Setting up a new Duo application to protect vCenter - 2:42
Discussion of setting up the Duo proxy appliance - 4:33
Configuring vCenter Server to use the Duo Proxy - 6:40
Testing the login to vCenter Server and two-factor push - 9:32
Concluding discussion on configuring two-factor authentication on vCenter Server - 10:09
Take note of the detailed blog post I have written on the topic here:
Read the VMware vSphere 7 blog post covering the topic of identity federation:
Link to Duo Security:
Duo Proxy documentation:
While vSphere 7 adds the new identity federation capability in vCenter Server, currently this is only supported with Active Directory Federation Services (ADFS). If you don't currently have ADFS in your environment it can be overkill to setup ADFS just for two-factor authentication for vCenter. Also, you may be running an older vSphere version such as vSphere 6.5 or 6.7.
Using Duo Security and the Duo authentication proxy, you can easily configure two-factor authentication on your vCenter Server and require 2FA for all vCenter Active Directory logins. This is accomplished by proxying all the authentication requests to Active Directory through your Duo authentication proxy.
_____________________________________________________
Introduction to cybersecurity and challenges - 0:00-0:44
Why is two-factor authentication important? - 0:55
Introduction to Duo Security - 1:55
Setting up a new Duo application to protect vCenter - 2:42
Discussion of setting up the Duo proxy appliance - 4:33
Configuring vCenter Server to use the Duo Proxy - 6:40
Testing the login to vCenter Server and two-factor push - 9:32
Concluding discussion on configuring two-factor authentication on vCenter Server - 10:09
Take note of the detailed blog post I have written on the topic here:
Read the VMware vSphere 7 blog post covering the topic of identity federation:
Link to Duo Security:
Duo Proxy documentation:
Комментарии
 0:10:43
0:10:43
 0:00:32
0:00:32
 0:07:30
0:07:30
 0:04:31
0:04:31
 0:05:31
0:05:31
 0:00:41
0:00:41
 0:10:29
0:10:29
 0:07:17
0:07:17
 0:40:37
0:40:37
 0:19:07
0:19:07
 0:13:29
0:13:29
 0:02:27
0:02:27
 0:07:50
0:07:50
 0:24:32
0:24:32
 0:57:50
0:57:50
 0:20:43
0:20:43
 0:03:46
0:03:46
 0:00:53
0:00:53
 0:18:03
0:18:03
 0:17:03
0:17:03
 0:01:46
0:01:46
 0:56:00
0:56:00
 0:15:56
0:15:56
 0:21:38
0:21:38