filmov
tv
Execute Hidden Python Commands [Tutorial]
Показать описание
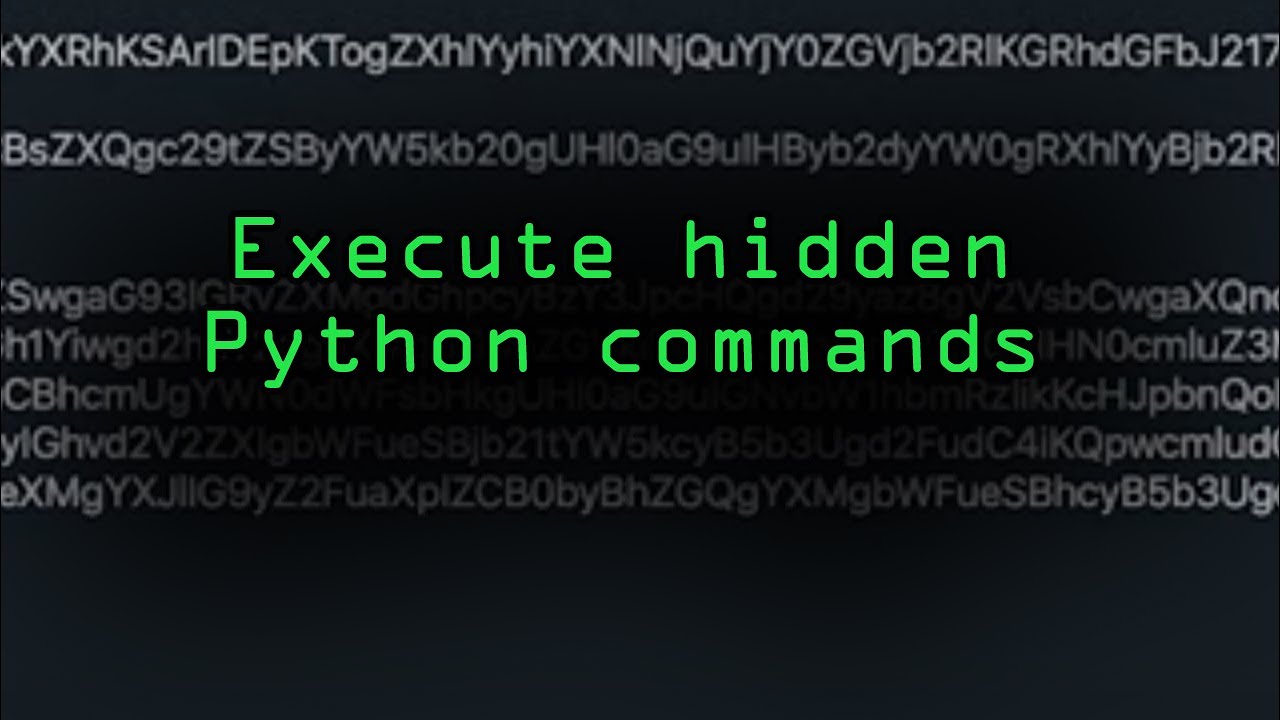
Hide a Stager in One Line of Code
Cyber Weapons Lab, Episode 153
A stager is how a hacker establishes a communication channel between them and their target in preparation for an attack. Today, on Cyber Weapons Lab, we'll explore how a stager works and how to execute any hidden Python commands you sneak onto a target's machine.
Follow Null Byte on:
Cyber Weapons Lab, Episode 153
A stager is how a hacker establishes a communication channel between them and their target in preparation for an attack. Today, on Cyber Weapons Lab, we'll explore how a stager works and how to execute any hidden Python commands you sneak onto a target's machine.
Follow Null Byte on:
Execute Hidden Python Commands [Tutorial]
How to hide console window in python when python app runs
Easy Hide Password Input in Python
How to Run a Python Program in the Background Like a PRO
How to HIDE Your API Keys in Python Projects
How to execute a Command Prompt command from Python
Obfuscate Python Code With PyArmor
Execute CMD and Python Commands C#
Algorithmic Trading Platform From Scratch in Python | Coding Until I Become a Quant
I Found Another Hidden F-String Feature In Python
Normal People VS Programmers #coding #python #programming #easy #funny #short
The Hidden Secrets of Python Byte Code Finally Revealed
how to run your python script in the background with no user interactive every time windows starts.
How to hide user input in Python? #python #programming #coding
Automatically Clear Printed Output From Terminal Using Python
Encryption program in Python 🔐
Running Shell Commands using Python (Detailed Explanation)
Hidden Password Input in Python
How to Hide Passwords and Secret Keys in Your Python Script (Windows/macOS)
Creating malicious software in Python. Pt:1 #Python #malware #linode #IT #tech #code #coding
Python Interactive mode is really helpful!
Run Python Script from C#
Simple Automated SSH Python Bot
Python Requests Tutorial: Request Web Pages, Download Images, POST Data, Read JSON, and More
Комментарии
 0:10:02
0:10:02
 0:01:25
0:01:25
 0:00:24
0:00:24
 0:01:22
0:01:22
 0:04:27
0:04:27
 0:01:36
0:01:36
 0:11:22
0:11:22
 0:06:09
0:06:09
 2:57:21
2:57:21
 0:00:55
0:00:55
 0:00:21
0:00:21
 0:00:27
0:00:27
 0:05:24
0:05:24
 0:00:15
0:00:15
 0:00:18
0:00:18
 0:08:41
0:08:41
 0:29:42
0:29:42
 0:09:40
0:09:40
 0:05:22
0:05:22
 0:01:00
0:01:00
 0:00:26
0:00:26
 0:12:43
0:12:43
 0:17:50
0:17:50
 0:25:01
0:25:01