filmov
tv
Best Practice pfSense Initial Setup w/Netgate 4100

Показать описание
The Netgate 4100 running pfSense is an excellent router/firewall for business. We like using this device for our clients because of the port options as well as the fact that it's the first model of Netgate pfSense router that can do high availability (HA).
In this video we briefly discuss the Netgate 4100 and then dig into a best practice pfSense setup that is typical for businesses featuring a standard secure LAN, a guest network VLAN, and some firewall rules. Our resident pfSense expert, David Barger leads the way through this process - if you need networking assistance, make sure to contact Crosstalk Solutions!
Timecodes:
00:00 Intro
01:40 Netgate 4100 Overview
04:24 Initial Setup Wizard
10:34 Updating pfSense
15:23 Install and Update Packages
18:44 Netgate Cloud Backup setup
22:44 Add Guest Network VLAN/Subnet/DHCP
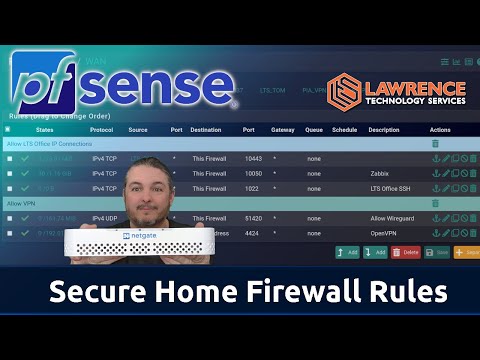
27:33 Set up Simple Firewall Rules
33:53 VoIP Considerations
------------------------
Follow me on Twitter: @crosstalksol
Connect with Chris:
Twitter: @CrosstalkSol
In this video we briefly discuss the Netgate 4100 and then dig into a best practice pfSense setup that is typical for businesses featuring a standard secure LAN, a guest network VLAN, and some firewall rules. Our resident pfSense expert, David Barger leads the way through this process - if you need networking assistance, make sure to contact Crosstalk Solutions!
Timecodes:
00:00 Intro
01:40 Netgate 4100 Overview
04:24 Initial Setup Wizard
10:34 Updating pfSense
15:23 Install and Update Packages
18:44 Netgate Cloud Backup setup
22:44 Add Guest Network VLAN/Subnet/DHCP
27:33 Set up Simple Firewall Rules
33:53 VoIP Considerations
------------------------
Follow me on Twitter: @crosstalksol
Connect with Chris:
Twitter: @CrosstalkSol
Комментарии
 0:37:33
0:37:33
 0:19:24
0:19:24
 0:17:27
0:17:27
 0:11:55
0:11:55
 0:38:04
0:38:04
 0:31:49
0:31:49
 3:35:47
3:35:47
 0:45:31
0:45:31
 0:53:21
0:53:21
 1:30:58
1:30:58
 0:09:09
0:09:09
 0:02:17
0:02:17
 0:27:52
0:27:52
 0:21:53
0:21:53
 0:13:32
0:13:32
 0:11:58
0:11:58
 0:18:29
0:18:29
 0:07:34
0:07:34
 0:23:51
0:23:51
 0:25:11
0:25:11
 0:27:49
0:27:49
 0:10:36
0:10:36
 0:08:36
0:08:36
 0:47:28
0:47:28