filmov
tv
Remote Procedure Calls

Показать описание
🎓 MCSI Certified Reverse Engineer 🎓
👩🏫 MCSI Reverse Engineering Certifications and Courses 👨🏫
💻🔎 MCSI Reverse Engineering Library 🔎💻
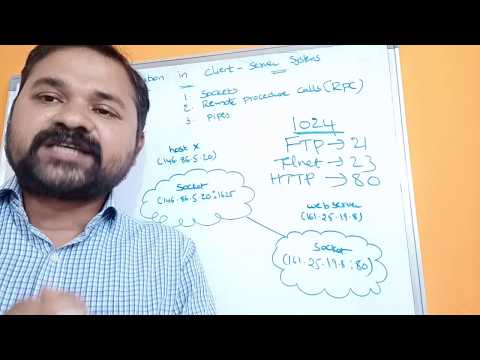
Remote Procedure Calls (RPC) within Windows internals form a pivotal avenue for reverse engineering exploration, unveiling a complex world of interprocess communication and distributed computing. RPCs enable software components to collaborate seamlessly across different processes, even spanning networked systems.
From a reverse engineering perspective, delving into RPCs is akin to unraveling the threads that connect software entities. By dissecting RPC mechanisms, reverse engineers gain insight into how functions and data are marshaled for communication between processes, regardless of their physical location. This understanding is crucial for comprehending software interactions and communication patterns.
Furthermore, RPCs offer a lens through which reverse engineers can decipher the orchestration of remote function calls and parameter passing. Analyzing RPC interfaces provides a deeper understanding of the protocols and conventions that govern interprocess communication, enabling reverse engineers to reconstruct communication flows and assess potential vulnerabilities.
In essence, exploring Remote Procedure Calls within Windows internals empowers reverse engineers to peer into the intricate web of distributed software systems. By uncovering the mechanics of RPCs, reverse engineers enhance their ability to analyze software behavior, identify potential security gaps, and optimize communication pathways.
👩🏫 MCSI Reverse Engineering Certifications and Courses 👨🏫
💻🔎 MCSI Reverse Engineering Library 🔎💻
Remote Procedure Calls (RPC) within Windows internals form a pivotal avenue for reverse engineering exploration, unveiling a complex world of interprocess communication and distributed computing. RPCs enable software components to collaborate seamlessly across different processes, even spanning networked systems.
From a reverse engineering perspective, delving into RPCs is akin to unraveling the threads that connect software entities. By dissecting RPC mechanisms, reverse engineers gain insight into how functions and data are marshaled for communication between processes, regardless of their physical location. This understanding is crucial for comprehending software interactions and communication patterns.
Furthermore, RPCs offer a lens through which reverse engineers can decipher the orchestration of remote function calls and parameter passing. Analyzing RPC interfaces provides a deeper understanding of the protocols and conventions that govern interprocess communication, enabling reverse engineers to reconstruct communication flows and assess potential vulnerabilities.
In essence, exploring Remote Procedure Calls within Windows internals empowers reverse engineers to peer into the intricate web of distributed software systems. By uncovering the mechanics of RPCs, reverse engineers enhance their ability to analyze software behavior, identify potential security gaps, and optimize communication pathways.
 0:14:32
0:14:32
 0:07:16
0:07:16
 0:06:09
0:06:09
 0:09:16
0:09:16
 0:33:05
0:33:05
 0:19:45
0:19:45
 0:03:56
0:03:56
 0:05:03
0:05:03
 0:13:12
0:13:12
 0:06:21
0:06:21
 0:20:38
0:20:38
 1:20:22
1:20:22
 0:06:50
0:06:50
 0:03:55
0:03:55
 0:53:46
0:53:46
 0:11:51
0:11:51
 0:05:18
0:05:18
 0:08:06
0:08:06
 1:25:30
1:25:30
 0:11:17
0:11:17
 0:01:58
0:01:58
 0:13:18
0:13:18
 0:06:45
0:06:45
 0:03:02
0:03:02