filmov
tv
Fingerprint a Hashed Password with Hash-Identifier [Tutorial]
Показать описание
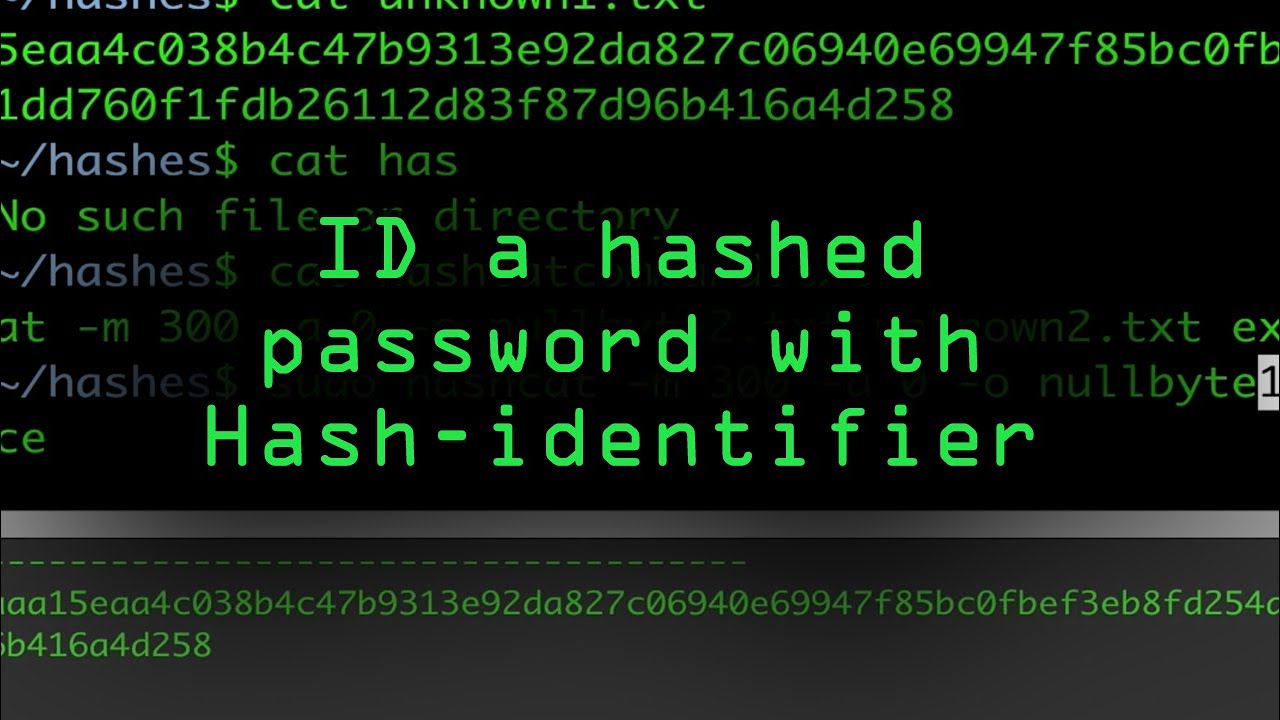
How to Fingerprint Hashed Passwords
Cyber Weapons Lab, Episode 132
Hashes are a way to avoid storing passwords in plain-text. It's a common security feature that requires cracking or brute-forcing in order to obtain a password during an attack. But in order to go about doing this, a hacker or pentester would need to know what kind of hash they're dealing with. We'll show you how to fingerprint a hashed password, on this episode of Cyber Weapons Lab.
Follow Null Byte on:
Cyber Weapons Lab, Episode 132
Hashes are a way to avoid storing passwords in plain-text. It's a common security feature that requires cracking or brute-forcing in order to obtain a password during an attack. But in order to go about doing this, a hacker or pentester would need to know what kind of hash they're dealing with. We'll show you how to fingerprint a hashed password, on this episode of Cyber Weapons Lab.
Follow Null Byte on:
Fingerprint a Hashed Password with Hash-Identifier [Tutorial]
Hash identifier | Fingerprint a Hashed Password with Hash-Identifier [Tutorial] | The AB
Password Storage Tier List: encryption, hashing, salting, bcrypt, and beyond
Fingerprint a Hashed Password | How to easily identify hash type | Identify hash Algorithm in Linux
Passwords & hash functions (Simply Explained)
Password Cracking Methodology || Hash Identifier and Find my Hash
SHA: Secure Hashing Algorithm - Computerphile
Hashing in Python: Using Hashlib Library for Secure Hashing
Fingerprinting with Hash Functions
Password Cracking 101+1: Part 10 - Fingerprint Attacks
Hashing, Hashing Algorithms, and Collisions - Cryptography - Practical TLS
SHA-256 | COMPLETE Step-By-Step Explanation (W/ Example)
What is a Hash for Applying Fingerprint? Watch WYF Session Conference
Password fingerprint safe
🔴 Live Proof - Unlock Any Android Phone Fingerprint, PIN & Password
Asymmetric Encryption - Simply explained
How to crack passwords - Gary Explains
Password Attacks - CompTIA A+ 220-1102 - 2.4
How to extract NTLM Hashes from Wireshark Captures for cracking with Hashcat
DECODIFY || Hash Cracker || Decoding || Kali Linux
Cracking password hashes SUPER FAST and FREE ! (Penglab & Google Colab)
Hashing and Digital Signatures - SY0-601 CompTIA Security+ : 2.8
how to set normal open and normal close on the fingerprint/ rfid access controller?
The Encryption and Password Hashing Recipe (with a little salt)
Комментарии
 0:12:52
0:12:52
 0:03:14
0:03:14
 0:10:16
0:10:16
 0:06:27
0:06:27
 0:07:28
0:07:28
 0:07:22
0:07:22
 0:10:21
0:10:21
 0:15:42
0:15:42
 0:18:31
0:18:31
 0:17:03
0:17:03
 0:11:42
0:11:42
 0:13:01
0:13:01
 0:09:15
0:09:15
 0:02:11
0:02:11
 0:05:31
0:05:31
 0:04:40
0:04:40
 0:08:20
0:08:20
 0:07:05
0:07:05
 0:05:12
0:05:12
 0:08:03
0:08:03
 0:07:01
0:07:01
 0:10:52
0:10:52
 0:01:35
0:01:35
 1:04:30
1:04:30