filmov
tv
TShark: Leveraging statistics | Nik Alleyne

Показать описание
TShark statistics allows you to gain clear insights into the communication occurring on your network, making your analysis easier and quicker.
Join Nik Alleyne, a SANS Certified Instructor for this all new live stream to discuss how you can leverage statistics with TShark.
Nik teaches both SEC503: Intrusion Detection In-Depth and SEC504: Hacker Tools, Techniques, Exploits, and Incident Handling for SANS and is a published author of two books Hack and Detect and Mastering TShark Network Forensics.
Learn more about Nik:
#TShark #infosec #cybersecurity #cyber #networking #network #informationsecurity
Join Nik Alleyne, a SANS Certified Instructor for this all new live stream to discuss how you can leverage statistics with TShark.
Nik teaches both SEC503: Intrusion Detection In-Depth and SEC504: Hacker Tools, Techniques, Exploits, and Incident Handling for SANS and is a published author of two books Hack and Detect and Mastering TShark Network Forensics.
Learn more about Nik:
#TShark #infosec #cybersecurity #cyber #networking #network #informationsecurity
TShark: Leveraging statistics | Nik Alleyne
Intro to packet analysis with TShark
TShark - Exporting Suspicious Content
TShark - Working with Regular Expressions
Full Packet Capturing with TShark for Continuous Monitoring & Threat Intel via IP, Domains, &...
What is a Sniffing Attack: Best Countermeasures Against Such Cyberattacks
how to install tshark tool in kali linux
Sharkfest 2013 - Accessing Packet Traces From Multiple Locations (Bill Eastman)
SharkDump Network Analysis Using tcpdump and Wireshark
Talk 10 - Nick Mitropoulos - Security Certifications: Training on a Budget and Breaking Down the HR
SF17EU - 04: Augmenting Packet Capture with Contextual Meta-Data (Dr. Stephen Donnelly)
Pentesting with PowerShell Data Exfiltration Techniques by Mick Douglas
#HITB2016AMS D1T1 - Exploit Kits: Hunting The Hunters - Nick Biasini
SF20V - Vern Paxson and Robin Sommer Keynote
MolochON 2019 Leveraging Zeek Logs in Moloch with Filebeat and Logstash - Seth Grover
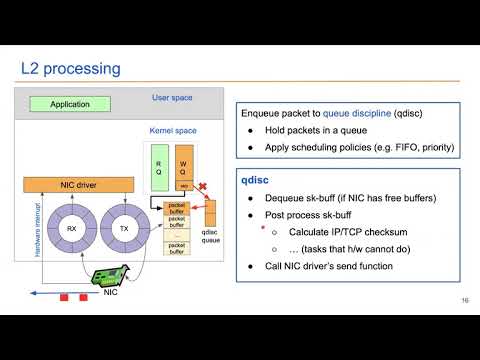
Kernel-bypass techniques for high-speed network packet processing
How to Become a Cybersecurity Expert: Stories and Lessons from SANS’ Nik Alleyne
Connect: How to run two wireless protocols with one device
Mastering Microsoft's CLI Packet Capture: Pktmon.exe for IT Pros
The Hitchhiker’s Guide to Evidence Sources - SANS Webcast
DeTT&CT(ing) Kubernetes ATT&CK(s) with Audit Logs
Scan for Vulnerabilities on Any Website Using Nikto [Tutorial]
NSDI '22 - FlexTOE: Flexible TCP Offload with Fine-Grained Parallelism
Daniel Barlow - NixWRT: purely functional firmware images for IoT (NixCon 2018)
Комментарии
 0:41:17
0:41:17
 1:07:40
1:07:40
 1:01:19
1:01:19
 0:56:12
0:56:12
 0:59:29
0:59:29
 0:08:39
0:08:39
 0:00:51
0:00:51
 0:52:54
0:52:54
 0:20:15
0:20:15
 0:21:52
0:21:52
 0:54:59
0:54:59
 1:07:46
1:07:46
 0:51:21
0:51:21
 1:00:42
1:00:42
 0:33:40
0:33:40
 0:29:05
0:29:05
 0:55:43
0:55:43
 0:09:13
0:09:13
 0:31:18
0:31:18
 0:52:51
0:52:51
 0:35:37
0:35:37
 0:15:56
0:15:56
 0:14:15
0:14:15
 0:30:06
0:30:06