filmov
tv
What is a Secure Internet Gateway?

Показать описание
Protecting computer systems against attack takes more than implementing a few simple security solutions. When facing threats such as ransonware, phishing, malware and DDOS attacks you need a secure internet gateway that integrates your security system with real time monitoring and analytics.
Transcript-
What is a secure internet gateway?
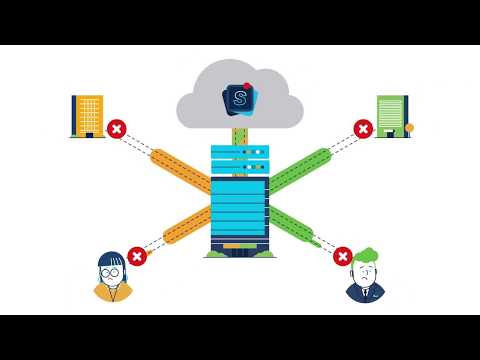
An SIG is a secure connection to the internet that protects internal IT systems, websites and networks from cyber threats.
A typical government agency or business has thousands of genuine online visitors daily. It’s a siege where the fortress gate is open to legitimate visitors while keeping the invaders out.
To do this you need a strong gate and a smart gate keeper. A system that can defend against the invading hordes while sorting the good from the bad, no matter how sneaky their plan is.
Threats are global and they come in many forms. Viruses, spam, malware, DDos attacks, trojans.. some things never change.
And more recently bots, social media engineered attacks and phishing. Threats whether a protest or more malicious aim to shut you down or defraud you and your customers
Leaked customer information can lead to litigation.
The most important thing to know about any threat is the exact mechanism used changes constantly.
The next thing to understand is that its big and getting bigger fast. Fuelled by huge increases in online interaction and the popularity of smart mobile devices.
The key challenge in cyber security is constant vigilance 24/7. the core disciplines are – checking each security event, identifying the true threats and taking countermeasures.
The federal government has introduced a gateway consolidation program to improve cyber security for government.
The goal is a smaller number of well managed gateways available to more agencies.
But agencies still have a choice among these approved gateways.
So what should you look for in a best practice gateway?
The baseline is scale and redundancy in best of breed security systems and the skills to run them 24/7.
More important is a high level of certification - ASD gateway compliance, ISO27001 for systems and PCI for financial transactions.
All managed by a security operations centre directly linked to ASD and ACSC, global cyber policing bodies like CERT, and all while complying to the ISM rulebook.
Most importantly is an Australian owned provider with Australian government-cleared specialists offering support and protection 24/7.
To understand more about how to protect your fortress contact Macquarie Government.
Transcript-
What is a secure internet gateway?
An SIG is a secure connection to the internet that protects internal IT systems, websites and networks from cyber threats.
A typical government agency or business has thousands of genuine online visitors daily. It’s a siege where the fortress gate is open to legitimate visitors while keeping the invaders out.
To do this you need a strong gate and a smart gate keeper. A system that can defend against the invading hordes while sorting the good from the bad, no matter how sneaky their plan is.
Threats are global and they come in many forms. Viruses, spam, malware, DDos attacks, trojans.. some things never change.
And more recently bots, social media engineered attacks and phishing. Threats whether a protest or more malicious aim to shut you down or defraud you and your customers
Leaked customer information can lead to litigation.
The most important thing to know about any threat is the exact mechanism used changes constantly.
The next thing to understand is that its big and getting bigger fast. Fuelled by huge increases in online interaction and the popularity of smart mobile devices.
The key challenge in cyber security is constant vigilance 24/7. the core disciplines are – checking each security event, identifying the true threats and taking countermeasures.
The federal government has introduced a gateway consolidation program to improve cyber security for government.
The goal is a smaller number of well managed gateways available to more agencies.
But agencies still have a choice among these approved gateways.
So what should you look for in a best practice gateway?
The baseline is scale and redundancy in best of breed security systems and the skills to run them 24/7.
More important is a high level of certification - ASD gateway compliance, ISO27001 for systems and PCI for financial transactions.
All managed by a security operations centre directly linked to ASD and ACSC, global cyber policing bodies like CERT, and all while complying to the ISM rulebook.
Most importantly is an Australian owned provider with Australian government-cleared specialists offering support and protection 24/7.
To understand more about how to protect your fortress contact Macquarie Government.
Комментарии
 0:03:30
0:03:30
 0:03:08
0:03:08
 0:07:07
0:07:07
 0:00:54
0:00:54
 0:02:10
0:02:10
 0:02:47
0:02:47
 0:10:38
0:10:38
 0:01:31
0:01:31
 0:00:36
0:00:36
 0:03:59
0:03:59
 0:05:15
0:05:15
 0:17:00
0:17:00
 0:05:02
0:05:02
 0:01:30
0:01:30
 0:01:01
0:01:01
 0:01:52
0:01:52
 0:02:10
0:02:10
 0:03:24
0:03:24
 0:02:07
0:02:07
 0:00:26
0:00:26
 0:00:14
0:00:14
 0:07:54
0:07:54
 0:01:52
0:01:52
 0:02:15
0:02:15