filmov
tv
Linux Privilege Escalation Techniques | Red Team Series 9-13

Показать описание
In this video in our @HackerSploit Red Team Series, we will cover Linux privilege escalation techniques. This includes obtaining root access, and exploiting permissions or binaries to achieve access.
Chapters:
0:00 Introduction
0:35 What We’ll Be Covering
1:00 Linux Privilege Escalation Techniques
4:00 MITRE Attack Privilege Escalation Techniques
5:12 Techniques You Should Follow
15:36 How to Obtain Root Access
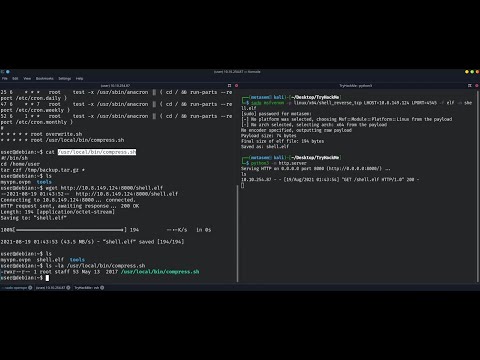
19:22 How to Exploit SUID Binaries / SUDO Permissions
22:25 How to Use a Kernel Exploit
27:45 How to Transfer the Exploit to the Target
32:26 How Does the Exploit Work?
34:48 How to Execute the Exploit
38:43 Conclusion
#Linode #Hackersploit #Security #RedTeam ; @HackerSploit
Chapters:
0:00 Introduction
0:35 What We’ll Be Covering
1:00 Linux Privilege Escalation Techniques
4:00 MITRE Attack Privilege Escalation Techniques
5:12 Techniques You Should Follow
15:36 How to Obtain Root Access
19:22 How to Exploit SUID Binaries / SUDO Permissions
22:25 How to Use a Kernel Exploit
27:45 How to Transfer the Exploit to the Target
32:26 How Does the Exploit Work?
34:48 How to Execute the Exploit
38:43 Conclusion
#Linode #Hackersploit #Security #RedTeam ; @HackerSploit
Linux Red Team Privilege Escalation Techniques - Kernel Exploits & SUDO Permissions
Linux Privilege Escalation for Beginners
Linux Privilege Escalation - Three Easy Ways to Get a Root Shell
How Hacker Gain Root Access | Linux Privilege Escalation
Linux Privilege Escalation Techniques | Red Team Series 9-13
Linux Privilege Escalation Techniques | Cron Jobs | TryHackMe
OSCP - Linux Privilege Escalation Methodology
Linux Privilege Escalation – Full Free Course
Linux Privilege Escalation : CAPABILITIES
Hacking Linux // Linux Privilege escalation // Featuring HackerSploit
Linux Privilege Escalation: SUID || Episode #5
Try This Linux Privilege Escalation Method
Linux Privilege Escalation - Tradecraft Security Weekly #22
Mastering Linux Privilege Escalation: Penetration Testing Techniques!
BOOK RELEASE - Privilege Escalation Techniques
Linux Privilege Escalation Crash Course
Linux Privilege Escalation : Capabilities || Episode #6
Linux Privilege Escalation 2024 | C 29/29 | Automated Scripts for Linux Privilege Escalation
Linux Privilege Escalation : PATH || Episode #8
💻 Unveiling the Ultimate Privilege Escalation Hack Unraveling Vulnerabilities
Linux Privilege Escalation for Beginners | CEH v12 ILabs Walkthrough
Linux Privilege Escalation - The different ways to do it
Dirty Pipe - CVE-2022-0847 - Linux Privilege Escalation
Linux Privilege Escalation : SUDO Rights with VIM
Комментарии
 0:40:42
0:40:42
 2:53:12
2:53:12
 0:05:53
0:05:53
 0:09:55
0:09:55
 0:41:12
0:41:12
 0:17:21
0:17:21
 0:19:25
0:19:25
 8:51:03
8:51:03
 0:03:15
0:03:15
 1:07:08
1:07:08
 0:09:52
0:09:52
 0:15:16
0:15:16
 0:17:59
0:17:59
 0:16:48
0:16:48
 0:08:03
0:08:03
 0:50:10
0:50:10
 0:09:04
0:09:04
 0:05:19
0:05:19
 0:13:17
0:13:17
 0:00:27
0:00:27
 0:13:47
0:13:47
 0:14:30
0:14:30
 0:23:20
0:23:20
 0:01:21
0:01:21