filmov
tv
MCITP 70-640: Active Directory Domain Functional Levels

Показать описание
Active Directory has functional levels at the domain and forest levels which determine which Active Directory features are available. The higher the functional level the more features available. This video looks at which domain functional levels are available and how to raise the domain functional level to get access to these features. The next video in this free series looks at the forest functional levels.
Raising the domain function level demo 17:46
The different domain functional levels and the features you get from the functional level are listed below.
Windows 2000 native
* Gives basic Active Directory functionality
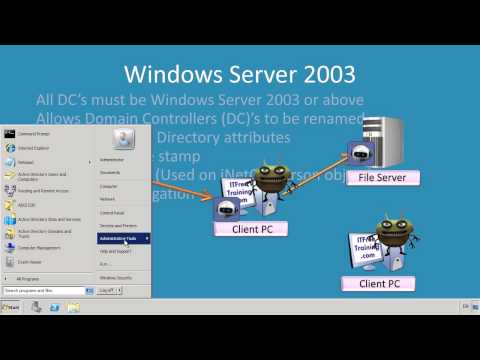
Windows Server 2003
* Allows the computer name of a domain controller to be changed.
* Adds last login time stamp to each user account
* Adds UserPassword to iNetOrgPerson object. This is used when migrating from a 3rd party directory service. It allows the 3rd party password to be stored in Active Directory.
* Constrained delegation. Delegation is when credentials are passed from one system to another; e.g., an administrator connects to a computer and then attempts to have that computer connect to a file share on another computer using the administrator's credentials. Delegation is disabled by default in Active Directory. Windows Server 2003 domain functional level allows you to determine which services are delegated and which are not and to which computers. You could, for example, trust delegation only for file sharing to only a particular server. Before this domain functional level delegation was to everything or nothing.
* Selected authentication for forests. When using multiple forests this feature allows the administrator to configure which users from the trusted forest can have access to which services in the forest that they would normally have access to by default. A user from another forest needs to have access to resources in the either forest like any other user through permissions like NTFS so selected authentication does not change that. The difference with selected authentication is that you can configure which services they can use which would normally be available to everyone. For example, a domain controller will by default authenticate any user from either forest. With selected authentication you can configure which domain controllers will be allowed to authenticate users from the other forest.
* Adds support to store authorization policies in Active Directory.
Windows Server 2008
* DFS for replication of SysVol share.
* Advanced Encryption System (AES) for Kerberos
* Additional last login details. Adds attributes like number of failed login attempts.
* Fine-grained password. Allows multiple password policies to be defined in the same domain.
Windows Server 2008 R2
* Authentication Mechanism Assurance. Adds details to the Kerberos ticket about how it was authenticated, e.g., if a SmartCard was used to authenticate the user.
* Automatic SPN (Service Principal Names) management. Allows services account password to be managed by Active Directory.
Mixed or Interim
domain functional levels that are mixed or interim have been upgraded from an NT4 domain and may have some domain controllers that are still NT4. Once you have removed all of the NT4 domain controllers, raise the domain functional level to one of the domain functional levels listed above.
Rasing the Domain Function Level
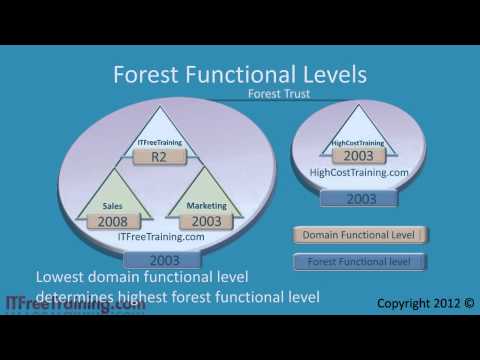
In order to raise the domain functional level, you need to ensure that all of the domain controllers in your domain are at that domain functional level or higher. For example, if you had 3 Windows Server 2008 DC's, 4 Windows Server 2003 DC's and 1 Windows 2000 DC the highest domain functional level that you could go to would be Windows 2000 native. If you upgrade the Windows Server 2000 domain controller to Windows Server 2003, you could raise the domain functional level to Windows Server 2003. Remember also that once you raise your domain functional level you will not be able to add any down level domain controllers to the domain. For example, if you raise the domain functional level to Windows Server 2008, you would not be able to add any domain controllers for Windows 2000 and Windows 2003. Regardless of the domain functional level you can add any Windows client operating system or server to the domain of any operating system level. Raising the domain functional level is a one way process and can't be reversed once complete.
Raising the domain functional level
To raise the functional level, open Active Directory User and Computer and right click on your domain and select raise domain functional level. Select the domain functional level that you want and select raise.
Keywords: "Domain Functional Levels" "Active Directory" 70-640 MCITP MCTS ITFreeTraining
Raising the domain function level demo 17:46
The different domain functional levels and the features you get from the functional level are listed below.
Windows 2000 native
* Gives basic Active Directory functionality
Windows Server 2003
* Allows the computer name of a domain controller to be changed.
* Adds last login time stamp to each user account
* Adds UserPassword to iNetOrgPerson object. This is used when migrating from a 3rd party directory service. It allows the 3rd party password to be stored in Active Directory.
* Constrained delegation. Delegation is when credentials are passed from one system to another; e.g., an administrator connects to a computer and then attempts to have that computer connect to a file share on another computer using the administrator's credentials. Delegation is disabled by default in Active Directory. Windows Server 2003 domain functional level allows you to determine which services are delegated and which are not and to which computers. You could, for example, trust delegation only for file sharing to only a particular server. Before this domain functional level delegation was to everything or nothing.
* Selected authentication for forests. When using multiple forests this feature allows the administrator to configure which users from the trusted forest can have access to which services in the forest that they would normally have access to by default. A user from another forest needs to have access to resources in the either forest like any other user through permissions like NTFS so selected authentication does not change that. The difference with selected authentication is that you can configure which services they can use which would normally be available to everyone. For example, a domain controller will by default authenticate any user from either forest. With selected authentication you can configure which domain controllers will be allowed to authenticate users from the other forest.
* Adds support to store authorization policies in Active Directory.
Windows Server 2008
* DFS for replication of SysVol share.
* Advanced Encryption System (AES) for Kerberos
* Additional last login details. Adds attributes like number of failed login attempts.
* Fine-grained password. Allows multiple password policies to be defined in the same domain.
Windows Server 2008 R2
* Authentication Mechanism Assurance. Adds details to the Kerberos ticket about how it was authenticated, e.g., if a SmartCard was used to authenticate the user.
* Automatic SPN (Service Principal Names) management. Allows services account password to be managed by Active Directory.
Mixed or Interim
domain functional levels that are mixed or interim have been upgraded from an NT4 domain and may have some domain controllers that are still NT4. Once you have removed all of the NT4 domain controllers, raise the domain functional level to one of the domain functional levels listed above.
Rasing the Domain Function Level
In order to raise the domain functional level, you need to ensure that all of the domain controllers in your domain are at that domain functional level or higher. For example, if you had 3 Windows Server 2008 DC's, 4 Windows Server 2003 DC's and 1 Windows 2000 DC the highest domain functional level that you could go to would be Windows 2000 native. If you upgrade the Windows Server 2000 domain controller to Windows Server 2003, you could raise the domain functional level to Windows Server 2003. Remember also that once you raise your domain functional level you will not be able to add any down level domain controllers to the domain. For example, if you raise the domain functional level to Windows Server 2008, you would not be able to add any domain controllers for Windows 2000 and Windows 2003. Regardless of the domain functional level you can add any Windows client operating system or server to the domain of any operating system level. Raising the domain functional level is a one way process and can't be reversed once complete.
Raising the domain functional level
To raise the functional level, open Active Directory User and Computer and right click on your domain and select raise domain functional level. Select the domain functional level that you want and select raise.
Keywords: "Domain Functional Levels" "Active Directory" 70-640 MCITP MCTS ITFreeTraining
Комментарии
 0:18:56
0:18:56
 0:08:48
0:08:48
 0:26:14
0:26:14
 0:14:24
0:14:24
 0:08:09
0:08:09
 0:20:45
0:20:45
 0:17:24
0:17:24
 0:13:43
0:13:43
 0:17:57
0:17:57
 0:05:55
0:05:55
 0:18:41
0:18:41
 0:08:04
0:08:04
 0:10:03
0:10:03
 0:08:30
0:08:30
 0:14:12
0:14:12
 0:13:41
0:13:41
 0:18:55
0:18:55
 0:09:53
0:09:53
 0:07:32
0:07:32
 0:20:45
0:20:45
 0:09:38
0:09:38
 0:15:07
0:15:07
 0:08:30
0:08:30
 0:08:43
0:08:43