filmov
tv
Friendly Intro to Hardware Security Modules (HSMs)

Показать описание
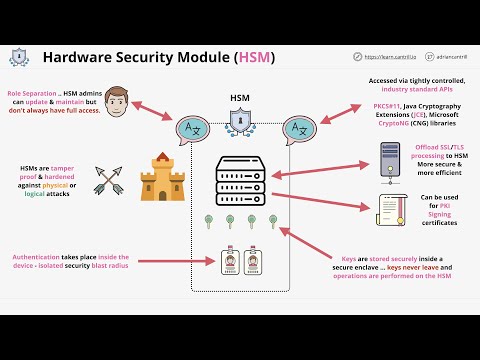
Hardware security modules are specialized security devices for storing sensitive cryptographic material like encryption keys. By storing keys on a fortified hardware device, stealing the key becomes much more difficult. The alternative is to store keys on a normal server or computer, which can be significantly riskier.
Feel free to ask questions below.
00:00 Intro
00:41 When Encrypting, Storing Keys On The Server Is Risky
02:02 Enter The Hardware Security Module
02:32 Why Are HSMs Better?
03:35 Sequence Diagram Using A HSM
03:57 Before HSM And After HSM
Feel free to ask questions below.
00:00 Intro
00:41 When Encrypting, Storing Keys On The Server Is Risky
02:02 Enter The Hardware Security Module
02:32 Why Are HSMs Better?
03:35 Sequence Diagram Using A HSM
03:57 Before HSM And After HSM
Friendly Intro to Hardware Security Modules (HSMs)
What are hardware security modules (HSM), why we need them and how they work.
What is a Hardware Security Module (HSM)?
The Future of Hardware Security
What is a hardware security module (HSM)?
Hardware Security Module intro
Lec 36: Introduction to Hardware Security
YubiHSM 2 - Hardware Security Module Setup
Crypto HardWare Wallet using Raspberry Pi and drive - A minimal viable product | | ECE Project .
Cryptography : What are Hardware Security Modules (HSM)?
1 Introduction to Hardware Security
Intel Hardware Security Technologies | Intel Technology
Overview of HSM - Hardware Security Module
SWIFT Training - Operating your Hardware Security Module (HSM)
Hardware Security Module (HSM) Basics | Introduction To HSM
WOOT '20 - Hardware Security Is Hard: How Hardware Boundaries Define Platform Security
Hardware security modules (HSMs) and Security World
DEF CON 23 - Teddy Reed and Nick Anderson - Hardware and Trust Security ELI5
wolfHSM Design for Automotive Hardware Security Modules
DEF CON 23 - Hardware Hacking Village - Matt DuHarte - Introduction to USB and Fuzzing
CLF-C01 — Hardware Security Module
What is a Hardware Security Module?
Intro to Encryption, in Friendly Terms: Cryptography, AES, Man In The Middle, and HTTPS
Philippe Laulheret - Intro to Hardware Hacking - DEF CON 27 Conference
Комментарии
 0:04:32
0:04:32
 0:06:40
0:06:40
 0:05:53
0:05:53
 0:07:23
0:07:23
 0:03:19
0:03:19
 0:15:39
0:15:39
 0:23:18
0:23:18
 0:05:37
0:05:37
 0:02:37
0:02:37
 0:11:18
0:11:18
 0:11:06
0:11:06
 0:02:18
0:02:18
 0:10:20
0:10:20
 0:02:15
0:02:15
 0:08:57
0:08:57
 0:39:59
0:39:59
 0:03:33
0:03:33
 0:45:23
0:45:23
 1:05:30
1:05:30
 0:44:38
0:44:38
 0:02:26
0:02:26
 0:09:29
0:09:29
 0:06:45
0:06:45
 0:46:07
0:46:07