filmov
tv
Find Vulnerable Services & Hidden Info Using Google Dorks [Tutorial]

Показать описание
How to Find Hidden Information Online Using Google Dorks
A Google search may not be what one thinks of when it comes to hacking. However, Google offers advanced techniques when searching which can offer a treasure trove of hidden and vulnerable services if used correctly. Today, we'll introduce you to Google dorking, on this episode of Cyber Weapons Lab.
Follow Null Byte on:
Find Vulnerable Services & Hidden Info Using Google Dorks [Tutorial]
Google Dorking: How to Find Vulnerable & Hidden Services for Bug Bounties
Find Vulnerable Services & Hidden Info Using Google Dorks
Find Vulnerable Services & Hidden Info Using Google Dorks[Google hacking]
Find Vulnerable Services & Hidden Info Using Google Dorks ☠️
Find Vulnerable Services & Hidden Info Using Google Dorks [Tutorial 2024]
Hidden Info & Vulnerable Services Found With Google Dorking
How to find website Vulnerability ( CVEs)
Using Google Dorks to find sensitive info & Vulnerable Services
What is Google Hacking and Dorks? | Finding Vulnerable Services & Webcams
Nessus Vulnerability Scanner Tutorial: Finding Hidden Vulnerabilities
How to use Google web browser to find vulnerable MySQL websites to hack
Searching for System Vulnerability Exploits
Find SQL Injection Vulnerable Website Using Google | Google Dork Method
Cybersecurity Expert Demonstrates How Hackers Easily Gain Access To Sensitive Information
Search for Vulnerable Devices Around the World with Shodan [Tutorial]
🔐 Revealing Vulnerable Web Servers: Uncover Potential Risks 🔐
Basic SQL Injection ! How to find Vulnerable websites ✌️
How to find #SQLinjection vulnerable sites using #GoogleDorks
DO THIS to get under the skin of a VULNERABLE narcissist
Find Hidden Data | JS FILE RECON | Bug Bounty course for Beginners @Mr-Horbio
how to find vulnerable websites using google dorks
Payment Gateway Bypass Vulnerability | Bypass Payment Gateway | Web Application Security
Business Logic Vulnerability with hidden input | FirstBlood v3 | Bug Bounty Service
Комментарии
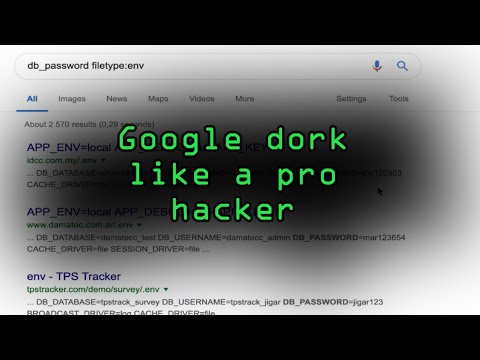 0:13:37
0:13:37
 0:12:38
0:12:38
 0:04:53
0:04:53
 0:06:18
0:06:18
 0:00:46
0:00:46
 0:05:18
0:05:18
 0:00:34
0:00:34
 0:07:30
0:07:30
 0:09:22
0:09:22
 0:13:20
0:13:20
 0:09:47
0:09:47
 0:00:51
0:00:51
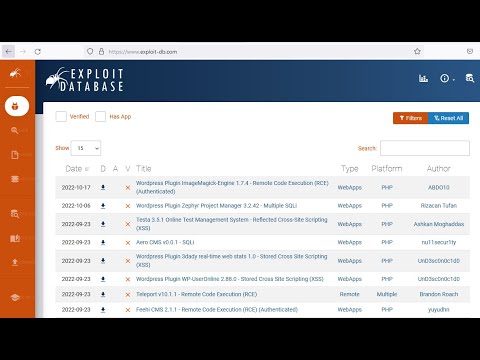 0:19:29
0:19:29
 0:02:53
0:02:53
 0:03:27
0:03:27
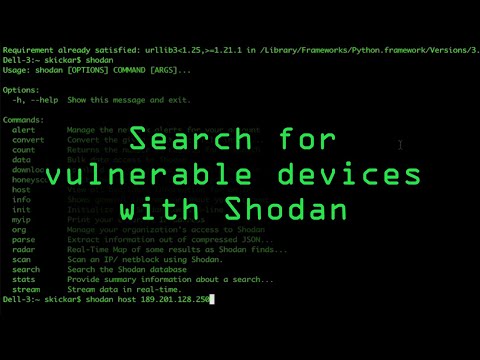 0:18:03
0:18:03
 0:00:57
0:00:57
 0:06:56
0:06:56
 0:01:16
0:01:16
 0:07:22
0:07:22
 0:03:43
0:03:43
 0:05:27
0:05:27
 0:01:53
0:01:53
 0:03:21
0:03:21