filmov
tv
Linux vs Windows: Malware

Показать описание
Linux vs Windows: Malware
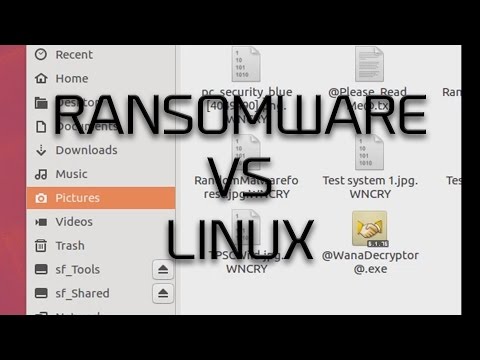
WannaCry on Linux?
Running MEMZ & Other Windows Malware on Ubuntu Linux under WINE
Why Windows Gets Viruses So Often
LINUX vs VIRUSES | HOW SAFE IS LINUX?!? | 4K
Some bad code just broke a billion Windows machines
Kids vs. MALWARE!!
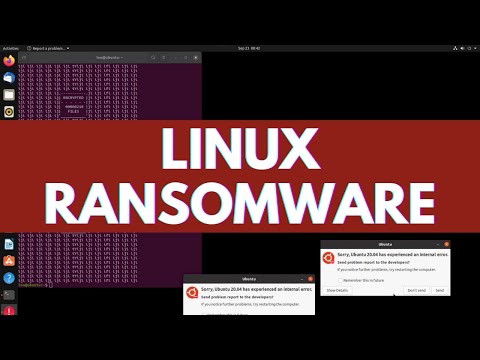
Linux Ransomware
Microsoft Sentinel | Integrate Microsoft Defender Threat Intelligence
macOS or Linux? 🤔 #Shorts
Windows Defender vs Top 100 Malware Sites
Windows Gamers vs Linux Gamers
linux users removing bloatware
I Tested Malware Against Antiviruses
Five Things Linux Does Better Than Windows
how windows defender works vs #malware
Malware beats Windows Defender: How you get hacked
Are Macs REALLY Safer?
The Malware that hacked Linus Tech Tips
How to never accidentally run Malware: Must Have Windows Tweaks
The Biggest Linux Security Mistakes
How risky is Piracy: Do cracks contain malware?
Linux Malware Calls Home: Vermilion Strike
Why Does Windows Gets Viruses So Often | Why Windows Gets Malware | Linux is Safer!
Комментарии
 0:06:57
0:06:57
 0:03:28
0:03:28
 0:12:31
0:12:31
 0:08:13
0:08:13
 0:08:55
0:08:55
 0:03:59
0:03:59
 0:00:58
0:00:58
 0:08:14
0:08:14
 0:13:18
0:13:18
 0:00:14
0:00:14
 0:10:15
0:10:15
 0:06:47
0:06:47
 0:00:39
0:00:39
 0:12:02
0:12:02
 0:06:27
0:06:27
 0:00:17
0:00:17
 0:07:26
0:07:26
 0:05:11
0:05:11
 0:10:13
0:10:13
 0:07:21
0:07:21
 0:09:44
0:09:44
 0:08:00
0:08:00
 0:08:39
0:08:39
 0:06:32
0:06:32