filmov
tv
How to structure networks with VLANs

Показать описание
In this video, I show you my new managed Switch from Sophos. I've split my network into multiple segments with VLAN, and created a fast transmission speed between the switch and my firewall system. #Sophos #VLAN #HomeLab
Follow me:
Timestamps:
00:00 - Introduction
00:55 - Disclaimer
01:44 - My Home Network
02:52 - Why I needed a managed Switch
05:49 - Configure the LAG
08:14 - Whare are VLANs?
10:39 - Configure VLANs
13:48 - PVID and Filtering
16:43 - Advantages of VLANs in networks
________________
All links with "*" are affiliate links.
Follow me:
Timestamps:
00:00 - Introduction
00:55 - Disclaimer
01:44 - My Home Network
02:52 - Why I needed a managed Switch
05:49 - Configure the LAG
08:14 - Whare are VLANs?
10:39 - Configure VLANs
13:48 - PVID and Filtering
16:43 - Advantages of VLANs in networks
________________
All links with "*" are affiliate links.
How to structure networks with VLANs
Basics of internet network structure.
Network Organisational Structure | Organisational Design | MeanThat
work Break down Structure (WBS) and Network Diagram how to?
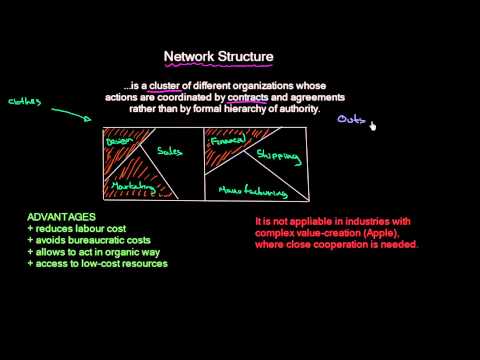
Network Structure
Network structure
How to structure a Tensorflow Neural Network in 7 minutes
Work Breakdown Structure [WBS EXPLAINED]
The Water Systems of Ancient Rome A Miracle of Engineering
Lesson 9: How to Structure Network Objects to Plan for Future Policy Growth
Social Network Structure
OTN Basic | Frame structure | OPU/ODU/OTU mapping with multiplexing in OTN #OTN
Neural networks tutorial: Fully Connected 2 [Java] - Basic structure
Network Structure
Lecture 3: DCCN | Internet Structure | Types of Delay | Throughput
Political Network Structure
IP Address Structure: Network and host portion
Neural Networks [Machine Learning] #2: Structure
WE MUST ADD STRUCTURE TO DEEP LEARNING BECAUSE...
Structure and visualize plant-specific networks with SINEMA Server
Large-scale structure in networks and the limits of detectability
DT&SC 5/6-5: Network Structure
Episode 1: How to Structure the Speech?
CN4: Network Structure and Architecture in Computer Networks| Network Topology and its Type
Комментарии
 0:18:36
0:18:36
 0:06:14
0:06:14
 0:05:01
0:05:01
 0:11:32
0:11:32
 0:04:55
0:04:55
 0:01:31
0:01:31
 0:07:27
0:07:27
 0:05:42
0:05:42
 0:00:48
0:00:48
 0:05:35
0:05:35
 0:12:08
0:12:08
 0:12:30
0:12:30
 0:08:37
0:08:37
 0:08:33
0:08:33
 0:35:06
0:35:06
 0:24:00
0:24:00
 0:20:40
0:20:40
 0:13:52
0:13:52
 1:49:11
1:49:11
 0:06:00
0:06:00
 0:44:36
0:44:36
 0:19:10
0:19:10
 0:02:04
0:02:04
 0:14:56
0:14:56