filmov
tv
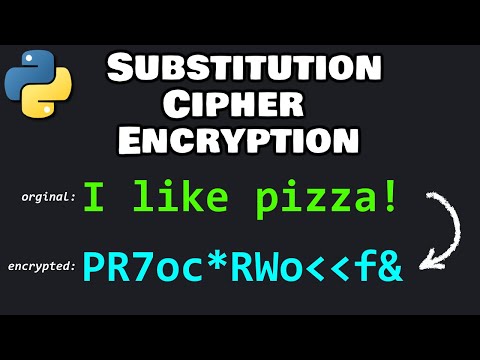
Substitution Cipher Implementation with Python

Показать описание
One of my favorite basic encryption methods: the substitution cipher. Enjoy!
Check out this code here:
Join my Discord server to chat with me:
Check out some code on my GitHub:
Tweet me something funny on Twitter:
Say hi over at Facebook:
Sincerely,
Engineer Man
Check out this code here:
Join my Discord server to chat with me:
Check out some code on my GitHub:
Tweet me something funny on Twitter:
Say hi over at Facebook:
Sincerely,
Engineer Man
Substitution Cipher in Python - Simple Cryptography
Substitution Cipher Implementation with Python
Substitution Cipher Technique in Python
GuidePoint Security CTF - 'Sub' Decrypting a Substitution Cipher with Python
Substitution Cipher in Python
Substitution Ciphers in Python
TUDev's Cryptography with Python Workshop! Creating a Substitution Cipher (Caesar Cipher)
Simple Substitution Cipher - Demo and Code
4 Keyword Substitution Cipher in Python
Encryption program in Python 🔐
Substitution based Encryption and Decryption in Python (Part A)
How to Encrypt Data Using Caesar Cipher in Python (Simple)
substitution cipher python code application of dictionary and strings
Trillions of Keys with the Substitution Cipher - Cracking Codes with Python (part 17)
Crack The Code! Substitution Ciphers
Hacking the Simple Substitution Cipher - Cracking Codes with Python (part 18)
Understanding Caesar Cipher in Python
Caesar Cipher Program in Python | Encryption and Decryption With Caesar Cipher
Python Project #4 | Caesar Cipher Introduction - part1 | Python Project for beginners #lec65
substitution cipher
Setup for Cracking NSA Ciphertext - simple substitution with Python
Substitution Cipher (HINDI) | Python code | Encryption-Decryption | Cryptography | Codewithvamp
Solving very simple substitution ciphers algorithmically - Stephen Enright Ward
CSC-120 Computing Fundamentals, the Substitution / Caesar Cipher, and implementing it in Python
Комментарии
 0:10:33
0:10:33
 0:08:15
0:08:15
 0:02:32
0:02:32
 0:07:03
0:07:03
 0:47:54
0:47:54
 0:10:28
0:10:28
 0:35:48
0:35:48
 0:06:09
0:06:09
 0:13:34
0:13:34
 0:08:41
0:08:41
 0:56:45
0:56:45
 0:04:10
0:04:10
 0:22:11
0:22:11
 0:16:03
0:16:03
 0:11:11
0:11:11
 0:17:35
0:17:35
 0:07:49
0:07:49
 0:17:31
0:17:31
 0:08:48
0:08:48
 0:10:32
0:10:32
 0:14:53
0:14:53
 0:28:34
0:28:34
 0:41:05
0:41:05
 0:26:53
0:26:53