filmov
tv
Anti CSRF tokens - explained

Показать описание
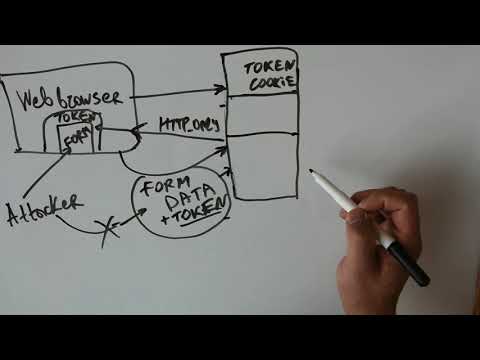
Why we should protect web forms and other sensitive links on websites using CSRF tokens. Describing protection tokens using: sessions and double cookies submission methods. Useful for ensuring secure client-to-server communication coming from a trusted source.
💖Support on Patreon:
----------------------------------------------------------------------------------------------------------------
----------------------------------------------------------------------------------------------------------------
💖Support on Patreon:
----------------------------------------------------------------------------------------------------------------
----------------------------------------------------------------------------------------------------------------
Anti CSRF tokens - explained
Cross-Site Request Forgery (CSRF) Explained
Your App Is NOT Secure If You Don’t Use CSRF Tokens
What is CSRF?
Cross-Site Request Forgery (CSRF) Explained And Demonstrated By A Pro Hacker!
How to Prevent CSRF - Explained In Less Than 5 Minutes
What Is a CSRF Attack and How Do You Prevent It?
Cross-Site Request Forgery (CSRF) Explained
046 Anti forgery Tokens
Cross-site request forgery | How csrf Token Works
#31 Spring Security | CSRF Token
Cross Site Request Forgery (CSRF or XSRF)
Cross-Site Request Forgery (CSRF) | Complete Guide
What is a CSRF token? — Cookies and CSRF explained for Django and Flask
CSRF Attack | CSRF Token | Simply Explained in Malayalam | Bug Bounty | Fetlla
43 Stealing and Bypassing AntiCSRF Tokens
What is CSRF | CSRF Attack | CSRF Token | Cross Site Request Forgery Explanation in Tamil
Laravel CSRF explained
Anti CSRF token protection
[HINDI] Cross Site Request Forgery (CSRF) Explained | Causes and Exploitation | How to be Safe?
What are CSRF Token and how to implement them?
Cross site Request Forgery in telugu | CSRF attack | VulnLogic telugu | vuln logic telugu
HOW CSRF TOKENS ARE CREATED? #shorts #csrf #security #webapplication
Sécurité : l'idée de l'attaque CSRF !
Комментарии
 0:05:57
0:05:57
 0:14:11
0:14:11
 0:09:57
0:09:57
 0:02:26
0:02:26
 0:06:31
0:06:31
 0:04:53
0:04:53
 0:08:54
0:08:54
 0:11:59
0:11:59
 0:04:52
0:04:52
 0:17:20
0:17:20
 0:17:56
0:17:56
 0:03:07
0:03:07
 0:48:11
0:48:11
 0:09:54
0:09:54
 0:06:53
0:06:53
 0:08:00
0:08:00
 0:04:46
0:04:46
 0:09:42
0:09:42
 0:17:36
0:17:36
![[HINDI] Cross Site](https://i.ytimg.com/vi/0OQ3Ajac5xU/hqdefault.jpg) 0:14:13
0:14:13
 0:10:37
0:10:37
 0:13:00
0:13:00
 0:00:52
0:00:52
 0:15:43
0:15:43