filmov
tv
Your App Is NOT Secure If You Don’t Use CSRF Tokens

Показать описание
Cross Site Request Forgery (CSRF) is one of the most common security vulnerabilities that most sites face, but many people don’t actually protect from it. In this video I will show you what CSRF is, how to protect against it, and what could happen if you don’t.
📚 Materials/References:
🌎 Find Me Here:
⏱️ Timestamps:
00:00 - Introduction
00:52 - Project Overview
02:42 - How CSRF Works
05:15 - How To Fix CSRF Vulnerabilities
#CSRF #WDS #WebSecurity
📚 Materials/References:
🌎 Find Me Here:
⏱️ Timestamps:
00:00 - Introduction
00:52 - Project Overview
02:42 - How CSRF Works
05:15 - How To Fix CSRF Vulnerabilities
#CSRF #WDS #WebSecurity
Your App Is NOT Secure If You Don’t Use CSRF Tokens
Our system detected that the device you are using is not secure (problem solved) / GCASH PROBLEM
Less secure app access not showing @gmail (SOLVED)
Which Encrypted Messaging App is Most Secure - Telegram, WhatsApp, Signal?
STOP using this Two-Factor Authentication (2FA) method!
Fix This Browser or App May Not be Secure Problem Solved!! 2021 🔥
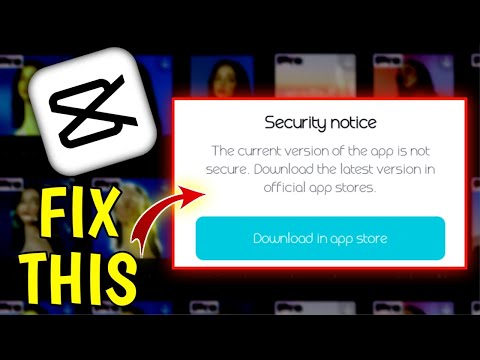
The current version of the app is not secure Capcut | Fix Capcut security Notice Problem
The current version of the app is not secure capcut | Security notice capcut
Fixed | Install Unknown sources disabled | Allow from other sources disabled
[FIXED] This browser or app may not secure. Try using a different browser
This browser or app may not secure. Try using a different browser. [SOLVED] in 1 minute!
How to Fix GCash App Device Is Not Secure - Android & Ios | Final Solution
GCASH PROBLEM DEVICE SECURITY
Solution for not working apps on mobile | Malayalam Explained By SPINACH MEDIA
How to Secure Your App With AppSweep
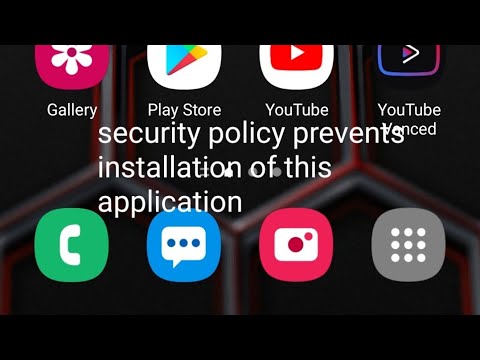
how to fix security policy prevents installation of this application samsung
Zangi Secure Messenger - Easy-to-use, Private and Secure Messaging App
How to Fix GCash App Error: The device you are using has settings that are not secure.
Why Telegram messaging app isn’t as secure as you think | Tech It Out
How To Fix Not Secure Website On Chrome!
This Browser Or App May Not Be Secure Google Chrome | How To Fix This Problem In Mobile
this apk file might contain unsafe content make sure you trust the sender problem fix | meaning
#1 Most Important iPhone PRIVACY Setting (You Need To Know This!)
The current version of the app is not secure Capcut | Fix Capcut security Notice Problem
Комментарии
 0:09:57
0:09:57
 0:02:56
0:02:56
 0:01:01
0:01:01
 0:06:30
0:06:30
 0:05:05
0:05:05
 0:01:12
0:01:12
 0:01:54
0:01:54
 0:02:53
0:02:53
 0:01:42
0:01:42
![[FIXED] This browser](https://i.ytimg.com/vi/FVumnHy5Tzo/hqdefault.jpg) 0:06:21
0:06:21
 0:01:00
0:01:00
 0:00:47
0:00:47
 0:01:31
0:01:31
 0:03:58
0:03:58
 0:27:44
0:27:44
 0:02:08
0:02:08
 0:01:05
0:01:05
 0:02:33
0:02:33
 0:04:00
0:04:00
 0:02:41
0:02:41
 0:01:49
0:01:49
 0:01:26
0:01:26
 0:03:36
0:03:36
 0:01:44
0:01:44