filmov
tv
Lecture 6: Data Encryption Standard (DES): Key Schedule and Decryption by Christof Paar

Показать описание
Lecture 6: Data Encryption Standard (DES): Key Schedule and Decryption by Christof Paar
Lecture 6 | Data Encryption Standard - DES
Introduction to Data Encryption Standard (DES)
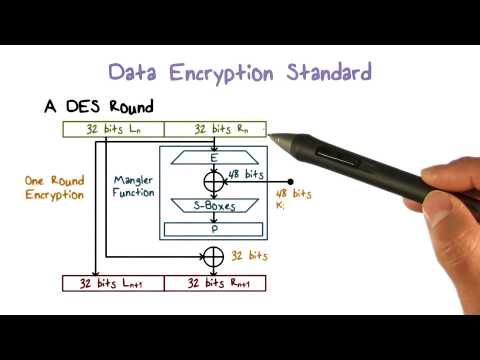
Data Encryption Standard
Lecture 5: Data Encryption Standard (DES): Encryption by Christof Paar
Lecture 6: Advanced Encryption Standard (AES) Part I
Lecture 6: Advanced Encryption Standard AES - Part II
6 Data encryption standard | Computer Monk 🔴
Simplified DES(Data Encryption Standard)(Information Security)
Data Encryption Standard (CSS441, L06, Y15)
DES (Data Encryption Standard) Practice Question Part 2 | Practical Example | Lecture 6
Simplified Data Encryption Standard (DES) Example
Simplified data encryption standard(S-DES) || S-DES key generation with figure || Shafiq Refat
S - DES Decryption || Simplified data encryption standard(S-DES) || Explanation with example
DES Algorithm | Working of DES Algorithm | DES Encryption Process | Data Encryption Standard
Lecture 5: Part II - Data Encryption Standard (DES)
#18 Data Encryption Standard ( DES ) Algorithm |CNS|
Dr. Sami Zhioua, ICS 444: Lecture 02: Data Encryption Standard (DES)
Decoding Cryptography Lecture 6: Semantic, CPA, and CCA Security
DES - Data Encryption Standard | Data Encryption Standard In Cryptography |DES Algorithm|Simplilearn
Working of DES with Example
Fiestel cipher Data Encryption Standard encryption DES#CSS
Data Encryption Standard (DES)- Key generation
S Box
Комментарии
 1:07:06
1:07:06
 0:39:44
0:39:44
 0:08:18
0:08:18
 0:02:53
0:02:53
 1:33:37
1:33:37
 0:45:41
0:45:41
 1:13:29
1:13:29
 0:06:52
0:06:52
 0:23:10
0:23:10
 0:46:39
0:46:39
 0:23:12
0:23:12
 0:44:01
0:44:01
 0:04:48
0:04:48
 0:13:56
0:13:56
 0:18:35
0:18:35
 0:37:52
0:37:52
 0:09:31
0:09:31
 0:41:39
0:41:39
 0:16:54
0:16:54
 0:16:30
0:16:30
 0:13:11
0:13:11
 0:46:35
0:46:35
 0:09:15
0:09:15
 0:00:38
0:00:38