filmov
tv
Find the real IP of protected websites ( EASY METHODS )

Показать описание
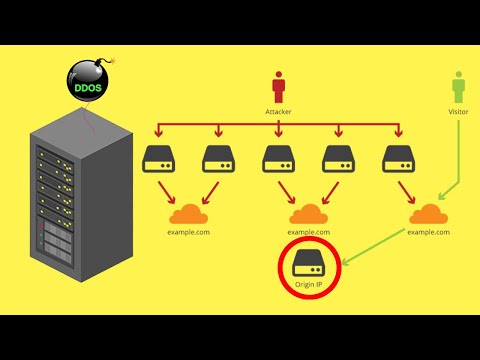
Finding Real IP addresses on Cloud-flare (CDN) Protected websites can be easy, hiding the origin servers IP is good practice but sometimes
simple mistakes in the server configuration can lead to the IP getting leaked.
In today's video we will uncover some easy straight forward methods
#CloudFlare #DDOS #OriginIP.
Enjoying my content? It would be appreciated if you drop a like 👍 , Subscribe ❤️ , and sharing my content is a plus 📤.
Worried about missing any new content? make sure to turn on the notifications, by pressing the bell icon 🔔.
🔥 About Me 🔥
My name is Hussein Muhaisen, since 7 years old, I found interest in playing video games, since then every time I play a video game I wondered how these things are built and made? that interest turned into an obsession in learning how computer systems work, how to test them, break them and fix them! Right now I am following my passion doing what I love, improving, and learning as I move on. I Also love making content ( videos, articles) it really helps with learning new things, I try to document my journey by making content, it motivates me when I look back and see improvements I made through my journey. Lastly, I always love giving back, I follow one rule which I created ” give to be given” simple as it sounds
⚠️⚠️⚠️ All The Content/Videos in My Channel are Made for Educational Purposes only I am Not Responsible for Any Damage Caused. ⚠️⚠️⚠️
Disclaimer:
This Video is for informational and educational purposes only. I believe that ethical hacking, information security, and cybersecurity
should be familiar subjects to anyone using digital information and computers. I believe that it is impossible to defend yourself
from hackers without knowing how hacking is done. This video is only for those who are interested to learn about ethical hacking, Security,
, Penetration Testing, and Other Cyber security-related resources. Please regard the word hacking as ethical hacking or penetration testing every time this
word is used. I do not promote, encourage, support, or excite any illegal activity or hacking without written permission in general. If you plan to use the information for illegal purposes, please leave this video now. I cannot be held responsible for any misuse of the given information.
Compliance with YouTube policy
According to the YouTube Community Policy
We do not urge people to use this software
We advise against using this bad software
We waive any responsibility for misconduct or use of these beta videos
🕒 Timestamps click them to jump into the topic. 🕒
0:00 - Introduction
0:53 - Whois and Dig
3:08 - Virtual Hosts
4:35 - DNS Records
6:40 - IOT Search Engines (Shodan , zoomeye , censys)
9:19 - MX Records ( Analyzing Email Headers )
11:05 - Favicons
13:00 - Ending (Slapping the like button)
simple mistakes in the server configuration can lead to the IP getting leaked.
In today's video we will uncover some easy straight forward methods
#CloudFlare #DDOS #OriginIP.
Enjoying my content? It would be appreciated if you drop a like 👍 , Subscribe ❤️ , and sharing my content is a plus 📤.
Worried about missing any new content? make sure to turn on the notifications, by pressing the bell icon 🔔.
🔥 About Me 🔥
My name is Hussein Muhaisen, since 7 years old, I found interest in playing video games, since then every time I play a video game I wondered how these things are built and made? that interest turned into an obsession in learning how computer systems work, how to test them, break them and fix them! Right now I am following my passion doing what I love, improving, and learning as I move on. I Also love making content ( videos, articles) it really helps with learning new things, I try to document my journey by making content, it motivates me when I look back and see improvements I made through my journey. Lastly, I always love giving back, I follow one rule which I created ” give to be given” simple as it sounds
⚠️⚠️⚠️ All The Content/Videos in My Channel are Made for Educational Purposes only I am Not Responsible for Any Damage Caused. ⚠️⚠️⚠️
Disclaimer:
This Video is for informational and educational purposes only. I believe that ethical hacking, information security, and cybersecurity
should be familiar subjects to anyone using digital information and computers. I believe that it is impossible to defend yourself
from hackers without knowing how hacking is done. This video is only for those who are interested to learn about ethical hacking, Security,
, Penetration Testing, and Other Cyber security-related resources. Please regard the word hacking as ethical hacking or penetration testing every time this
word is used. I do not promote, encourage, support, or excite any illegal activity or hacking without written permission in general. If you plan to use the information for illegal purposes, please leave this video now. I cannot be held responsible for any misuse of the given information.
Compliance with YouTube policy
According to the YouTube Community Policy
We do not urge people to use this software
We advise against using this bad software
We waive any responsibility for misconduct or use of these beta videos
🕒 Timestamps click them to jump into the topic. 🕒
0:00 - Introduction
0:53 - Whois and Dig
3:08 - Virtual Hosts
4:35 - DNS Records
6:40 - IOT Search Engines (Shodan , zoomeye , censys)
9:19 - MX Records ( Analyzing Email Headers )
11:05 - Favicons
13:00 - Ending (Slapping the like button)
Комментарии
 0:13:26
0:13:26
 0:03:52
0:03:52
 0:05:27
0:05:27
 0:09:58
0:09:58
 0:02:22
0:02:22
 0:00:25
0:00:25
 0:15:04
0:15:04
 0:01:03
0:01:03
 1:37:58
1:37:58
 0:01:16
0:01:16
 0:04:03
0:04:03
 0:00:46
0:00:46
 0:09:41
0:09:41
 0:00:57
0:00:57
 0:15:15
0:15:15
 0:03:43
0:03:43
 0:01:23
0:01:23
 0:01:04
0:01:04
 0:00:36
0:00:36
 0:01:33
0:01:33
 0:02:01
0:02:01
 0:01:34
0:01:34
 0:07:11
0:07:11
 0:02:09
0:02:09