filmov
tv
JWT Explained in Depth | CyberSecurityTv

Показать описание
JWT is a common form of method to maintain user sessions as well as authorize the users. It is essential to learn how JWT are formed and their use-cases.
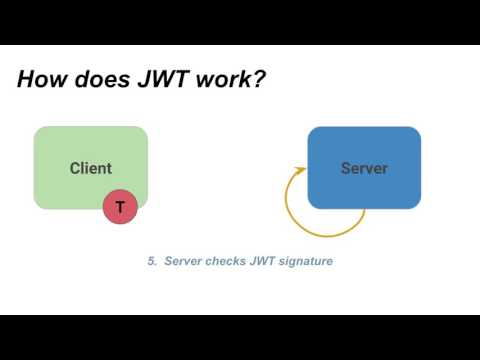
In this episode, we will learn the JWT schema, how it is connected, and its use. We will also learn how the signature is verified of the tokens.
Watch this video for full information - JWT Explained in Depth | CyberSecurityTv
🍁 𝐀𝐁𝐎𝐔𝐓 𝐂𝐲𝐛𝐞𝐫𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲𝐓𝐕 🍁
Cyber Security is an initiative taken by security professionals. Here we are uploading a series of videos to learn and get expertise in various domains of security. We are teaching tools, techniques, and methods which can be used on penetration testing assignments.
✨ 𝗝𝗢𝗜𝗡 𝐂𝐲𝐛𝐞𝐫𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲𝐓𝐕 ✨
💌 𝐋𝐄𝐓'𝐒 𝐒𝐓𝐀𝐘 𝐈𝐍 𝐓𝐎𝐔𝐂𝐇 💌
➟ Security Blog
➟ Facebook
📌𝐑𝐄𝐅𝐄𝐑𝐍𝐂𝐄𝐒
📌𝐂𝐲𝐛𝐞𝐫𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲𝐓𝐕 𝐎𝐓𝐇𝐄𝐑 𝐕𝐈𝐃𝐄𝐎𝐒
➟Tips for Secure Code Review | CybersecurityTV
➟Encryption Basics | CyberSecurityTV
➟ What are Dark Web | Email Providers | CyberSecurityTv
➟How to Bypass XSS Filters | CyberSecurityTV
#jsonwebtokens #applicationsecurity #jwt#cybersecurityonlinetraining #freesecuritytraining #penetrationtest #ethicalhacking #openaischema
𝐑𝐄𝐋𝐀𝐓𝗘𝐃 𝐒𝐄𝐀𝐑𝐂𝐇𝐄𝐒:
JSON web token introduction
parts of JWT
JWT authentication schema
JWT and its uses
JWT use in api
In this episode, we will learn the JWT schema, how it is connected, and its use. We will also learn how the signature is verified of the tokens.
Watch this video for full information - JWT Explained in Depth | CyberSecurityTv
🍁 𝐀𝐁𝐎𝐔𝐓 𝐂𝐲𝐛𝐞𝐫𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲𝐓𝐕 🍁
Cyber Security is an initiative taken by security professionals. Here we are uploading a series of videos to learn and get expertise in various domains of security. We are teaching tools, techniques, and methods which can be used on penetration testing assignments.
✨ 𝗝𝗢𝗜𝗡 𝐂𝐲𝐛𝐞𝐫𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲𝐓𝐕 ✨
💌 𝐋𝐄𝐓'𝐒 𝐒𝐓𝐀𝐘 𝐈𝐍 𝐓𝐎𝐔𝐂𝐇 💌
➟ Security Blog
📌𝐑𝐄𝐅𝐄𝐑𝐍𝐂𝐄𝐒
📌𝐂𝐲𝐛𝐞𝐫𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲𝐓𝐕 𝐎𝐓𝐇𝐄𝐑 𝐕𝐈𝐃𝐄𝐎𝐒
➟Tips for Secure Code Review | CybersecurityTV
➟Encryption Basics | CyberSecurityTV
➟ What are Dark Web | Email Providers | CyberSecurityTv
➟How to Bypass XSS Filters | CyberSecurityTV
#jsonwebtokens #applicationsecurity #jwt#cybersecurityonlinetraining #freesecuritytraining #penetrationtest #ethicalhacking #openaischema
𝐑𝐄𝐋𝐀𝐓𝗘𝐃 𝐒𝐄𝐀𝐑𝐂𝐇𝐄𝐒:
JSON web token introduction
parts of JWT
JWT authentication schema
JWT and its uses
JWT use in api
 0:14:53
0:14:53
 0:05:14
0:05:14
 0:09:18
0:09:18
 0:07:52
0:07:52
 0:05:13
0:05:13
 0:02:18
0:02:18
 0:01:07
0:01:07
 0:11:38
0:11:38
 0:02:15
0:02:15
 0:03:55
0:03:55
 0:11:27
0:11:27
 0:14:53
0:14:53
 0:10:25
0:10:25
 0:46:46
0:46:46
 0:02:05
0:02:05
 0:08:31
0:08:31
 0:01:00
0:01:00
 1:41:00
1:41:00
 0:01:00
0:01:00
 0:07:33
0:07:33
 0:26:12
0:26:12
 0:10:20
0:10:20
 0:27:36
0:27:36
 0:04:24
0:04:24