filmov
tv
Implement Azure Web Application Firewall - WAF Tutorial CDN, Azure Front Door, Application Gateway
Показать описание
azure web application firewall tutorial
Implement Azure Web Application Firewall - WAF Tutorial CDN, Azure Front Door, Application Gateway
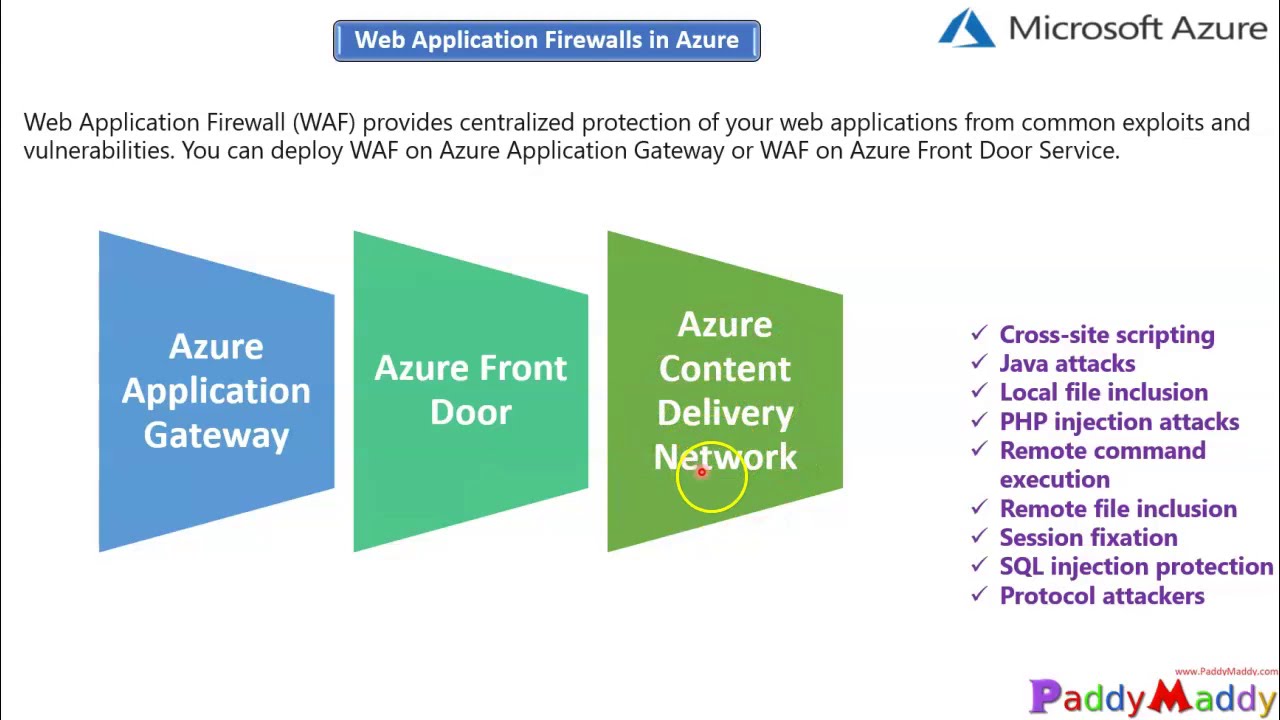
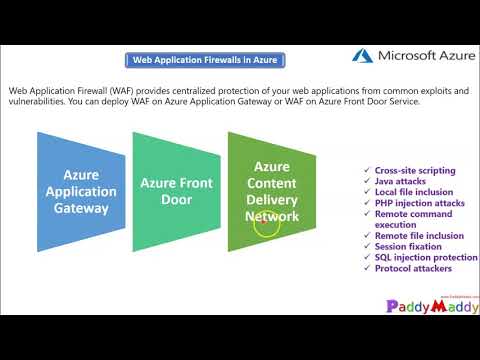
You can design, configure and implement (WAF) Azure Web Application Firewall for Application Gateway, Azure Front Door, and CDN - content delivery network
What is Azure Web Application Firewall on Azure Application Gateway?
Azure Web Application Firewall (WAF) on Azure Application Gateway provides centralized protection of your web applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks.
WAF on Application Gateway is based on Core Rule Set (CRS) 3.1, 3.0, or 2.2.9 from the Open Web Application Security Project (OWASP). The WAF automatically updates to include protection against new vulnerabilities, with no additional configuration needed.
All of the WAF features listed below exist inside of a WAF Policy. You can create multiple policies, and they can be associated with an Application Gateway, to individual listeners, or to path-based routing rules on an Application Gateway. This way, you can have separate policies for each site behind your Application Gateway if needed. For more information on WAF Policies, see Create a WAF Policy.
00:00 - Intro
01:10 Understand the configuration Demo for Protection
01:30 WAF on Azure Firewalls Protection
02:30 WAF on Azure Firewalls Protection features
04:00 WAF DEMO for Application Gateway secure with WAF
05:30 WAF Rules Demo for Application Gateway
06:45 Azure Front Door Protect with WAF
08:45 Azure Front Door DEMO to configure with WAF
09:40 Create WAF from Azure Portal and associate with Front Door
14:50 Azure CDN with WAF Configuration
15:55 DEMO Azure CDN with WAF Configuration
19:45 Compare Application Gateway vs Azure Front Door
21:52 What's next
Application Gateway security enhancements include TLS policy management and end-to-end TLS support. Application security is strengthened by WAF integration into the Application Gateway. The combination protects your web applications against common vulnerabilities. And it provides an easy-to-configure central location to manage.
Benefits
This section describes the core benefits that WAF on Application Gateway provides.
Protection
Protect your web applications from web vulnerabilities and attacks without modification to back-end code.
Protect multiple web applications at the same time. An instance of Application Gateway can host up to 40 websites that are protected by a web application firewall.
Create custom WAF policies for different sites behind the same WAF
Protect your web applications from malicious bots with the IP Reputation ruleset (preview)
Monitoring
Monitor attacks against your web applications by using a real-time WAF log. The log is integrated with Azure Monitor to track WAF alerts and easily monitor trends.
The Application Gateway WAF is integrated with Azure Security Center. Security Center provides a central view of the security state of all your Azure resources.
Customization
Customize WAF rules and rule groups to suit your application requirements and eliminate false positives.
Associate a WAF Policy for each site behind your WAF to allow for site-specific configuration
Create custom rules to suit the needs of your application
Features :
SQL-injection protection.
Cross-site scripting protection.
Protection against other common web attacks, such as command injection, HTTP request smuggling, HTTP response splitting, and remote file inclusion.
Protection against HTTP protocol violations.
Protection against HTTP protocol anomalies, such as missing host user-agent and accept headers.
Protection against crawlers and scanners.
Detection of common application misconfigurations (for example, Apache and IIS).
Configurable request size limits with lower and upper bounds.
Exclusion lists let you omit certain request attributes from a WAF evaluation. A common example is Active Directory-inserted tokens that are used for authentication or password fields.
Create custom rules to suit the specific needs of your applications.
Geo-filter traffic to allow or block certain countries/regions from gaining access to your applications. (preview)
Protect your applications from bots with the bot mitigation ruleset. (preview)
Inspect JSON and XML in the request body
WAF modes
Detection mode: Monitors and logs all threat alerts. You turn on logging diagnostics for Application Gateway in the Diagnostics section. You must also make sure that the WAF log is selected and turned on. Web application firewall doesn't block incoming requests when it's operating in Detection mode.
Prevention mode: Blocks intrusions and attacks that the rules detect. The attacker receives a "403 unauthorized access" exception, and the connection is closed. Prevention mode records such attacks in the WAF logs.
Implement Azure Web Application Firewall - WAF Tutorial CDN, Azure Front Door, Application Gateway
You can design, configure and implement (WAF) Azure Web Application Firewall for Application Gateway, Azure Front Door, and CDN - content delivery network
What is Azure Web Application Firewall on Azure Application Gateway?
Azure Web Application Firewall (WAF) on Azure Application Gateway provides centralized protection of your web applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks.
WAF on Application Gateway is based on Core Rule Set (CRS) 3.1, 3.0, or 2.2.9 from the Open Web Application Security Project (OWASP). The WAF automatically updates to include protection against new vulnerabilities, with no additional configuration needed.
All of the WAF features listed below exist inside of a WAF Policy. You can create multiple policies, and they can be associated with an Application Gateway, to individual listeners, or to path-based routing rules on an Application Gateway. This way, you can have separate policies for each site behind your Application Gateway if needed. For more information on WAF Policies, see Create a WAF Policy.
00:00 - Intro
01:10 Understand the configuration Demo for Protection
01:30 WAF on Azure Firewalls Protection
02:30 WAF on Azure Firewalls Protection features
04:00 WAF DEMO for Application Gateway secure with WAF
05:30 WAF Rules Demo for Application Gateway
06:45 Azure Front Door Protect with WAF
08:45 Azure Front Door DEMO to configure with WAF
09:40 Create WAF from Azure Portal and associate with Front Door
14:50 Azure CDN with WAF Configuration
15:55 DEMO Azure CDN with WAF Configuration
19:45 Compare Application Gateway vs Azure Front Door
21:52 What's next
Application Gateway security enhancements include TLS policy management and end-to-end TLS support. Application security is strengthened by WAF integration into the Application Gateway. The combination protects your web applications against common vulnerabilities. And it provides an easy-to-configure central location to manage.
Benefits
This section describes the core benefits that WAF on Application Gateway provides.
Protection
Protect your web applications from web vulnerabilities and attacks without modification to back-end code.
Protect multiple web applications at the same time. An instance of Application Gateway can host up to 40 websites that are protected by a web application firewall.
Create custom WAF policies for different sites behind the same WAF
Protect your web applications from malicious bots with the IP Reputation ruleset (preview)
Monitoring
Monitor attacks against your web applications by using a real-time WAF log. The log is integrated with Azure Monitor to track WAF alerts and easily monitor trends.
The Application Gateway WAF is integrated with Azure Security Center. Security Center provides a central view of the security state of all your Azure resources.
Customization
Customize WAF rules and rule groups to suit your application requirements and eliminate false positives.
Associate a WAF Policy for each site behind your WAF to allow for site-specific configuration
Create custom rules to suit the needs of your application
Features :
SQL-injection protection.
Cross-site scripting protection.
Protection against other common web attacks, such as command injection, HTTP request smuggling, HTTP response splitting, and remote file inclusion.
Protection against HTTP protocol violations.
Protection against HTTP protocol anomalies, such as missing host user-agent and accept headers.
Protection against crawlers and scanners.
Detection of common application misconfigurations (for example, Apache and IIS).
Configurable request size limits with lower and upper bounds.
Exclusion lists let you omit certain request attributes from a WAF evaluation. A common example is Active Directory-inserted tokens that are used for authentication or password fields.
Create custom rules to suit the specific needs of your applications.
Geo-filter traffic to allow or block certain countries/regions from gaining access to your applications. (preview)
Protect your applications from bots with the bot mitigation ruleset. (preview)
Inspect JSON and XML in the request body
WAF modes
Detection mode: Monitors and logs all threat alerts. You turn on logging diagnostics for Application Gateway in the Diagnostics section. You must also make sure that the WAF log is selected and turned on. Web application firewall doesn't block incoming requests when it's operating in Detection mode.
Prevention mode: Blocks intrusions and attacks that the rules detect. The attacker receives a "403 unauthorized access" exception, and the connection is closed. Prevention mode records such attacks in the WAF logs.
Комментарии
 0:14:08
0:14:08
 0:13:19
0:13:19
 0:02:57
0:02:57
 0:17:22
0:17:22
 0:22:08
0:22:08
 0:18:53
0:18:53
 0:15:56
0:15:56
 0:19:14
0:19:14
 1:08:38
1:08:38
 0:02:17
0:02:17
 1:02:11
1:02:11
 0:17:16
0:17:16
 0:49:36
0:49:36
 0:15:26
0:15:26
 0:18:27
0:18:27
 0:46:28
0:46:28
 0:07:38
0:07:38
 0:02:32
0:02:32
 0:05:38
0:05:38
 0:24:41
0:24:41
 1:22:20
1:22:20
 0:18:20
0:18:20
 0:10:04
0:10:04
 0:26:48
0:26:48