filmov
tv
Kerberos - authentication protocol

Показать описание
At 4:30: A mistake: step 3: When the file server gets the token, it "decrypts" (not "encrypts") the token with the secret key shared with TGS.
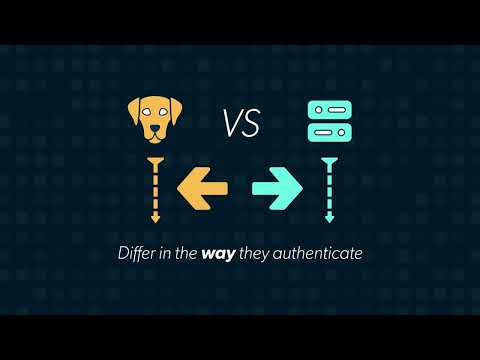
In Greek mythology, Kerberos is a dog with three heads. But today I will not talk about the dog. Kerberos is an authentication protocol for client/server applications. I will demonstrate with an example how Kerberos works. Keep in mind, Kerberos implements private key encryption.
Playlist: Basic Cryptography
Advanced Cryptography:
Please leave comments, questions and
Please subscribe to my channel
Many thanks,
Sunny Classroom
How Kerberos Works
Kerberos - authentication protocol
Kerberos Simplified - CISSP Exam Prep
Kerberos vs. LDAP: What’s the Difference?
Kerberos Authentication Protocol 🔥🔥
Kerberos Authentication Explained | A deep dive
Taming Kerberos - Computerphile
#40 Kerberos - Authentication Protocol, Working with diagram|CNS|
Kerberos
Basic Kerberos Authentication
MicroNugget: How Kerberos Works in Windows Active Directory | CBT Nuggets
Kerberos - CompTIA Security+ SY0-401: 5.1
KERBEROS || AUTHENITCATION APPLICATION || AUTHENTICATION SERVER|| TICKET GRANTING SERVER
The Kerberos Authentication Protocol explained
NTLM vs Kerberos Authentication
Kerberos Authentication
Kerberos Authentication Process
Authentication Methods - CompTIA A+ 220-1102 - 2.2
Overview Kerberos Authentication
kerberos authentication system | demo
Kerberos Authentication Protocol - part 1 (In detail)
Kerberos Authentication | Basics to Kerberos attacks
Kerberos - Authentication Protocol
Kerberos - Network Authentication Protocol explained in hindi || Working ,History ,AS ,TGS and AP
Комментарии
 0:02:19
0:02:19
 0:06:08
0:06:08
 0:04:16
0:04:16
 0:03:46
0:03:46
 0:06:43
0:06:43
 0:16:52
0:16:52
 0:16:06
0:16:06
 0:07:01
0:07:01
 0:02:42
0:02:42
 0:12:15
0:12:15
 0:07:08
0:07:08
 0:09:55
0:09:55
 0:29:31
0:29:31
 0:05:03
0:05:03
 0:08:08
0:08:08
 0:04:11
0:04:11
 0:13:51
0:13:51
 0:06:16
0:06:16
 0:19:13
0:19:13
 0:02:26
0:02:26
 0:05:55
0:05:55
 0:01:44
0:01:44
 0:05:25
0:05:25
 0:06:35
0:06:35