filmov
tv
Cybersecurity Architecture: Fundamentals of Confidentiality, Integrity, and Availability

Показать описание
In this next installment of the Cybersecurity Architecture series, Jeff "the Security guy" covers the three fundamentals that must be part of your security checklist: Confidentiality, Integrity, and Availability, also known as the "CIA Triad".
#AI #Software #ITModernization #Cybersecurity #QRadar #JeffCrume
Chapters
00:00 Confidentiality
03:51 Integrity
06:50 Availability
Cybersecurity Architecture: Fundamentals of Confidentiality, Integrity, and Availability
Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)
Cybersecurity Architecture: Networks
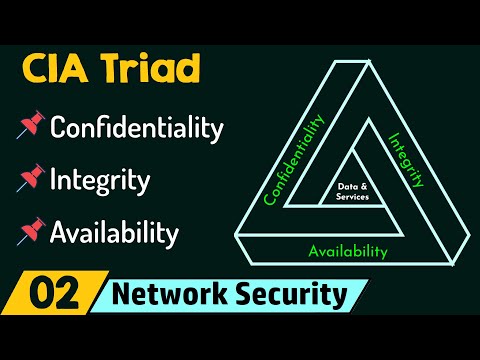
CIA Triad
Cybersecurity Architecture: Roles and Tools
CIA Properties | Confidentiality, Integrity, Availability with examples
Cybersecurity Architecture: Endpoints Are the IT Front Door - Guard Them
Cybersecurity Architecture: Who Are You? Identity and Access Management
Next-Generation Cybersecurity Architecture
What is the CIA Triad
Principles of Information Security: Confidentiality, Integrity, & Availability
Security Services
What is Confidential Compute?
How do SSL & TLS protect your Data? - Confidentiality, Integrity, Authentication - Practical TLS
What is the CIA Triad? (See Description)
Cybersecurity: Confidentiality | CIA Triad
What is the CIA triad and why is it important?
60 Second Cybersecurity: Information Confidentiality
AI in Cybersecurity
Internet Networks & Network Security | Google Cybersecurity Certificate
A REAL Day in the life in Cybersecurity in Under 10 Minutes!
CIA Triad Explained - Confidentiality / Integrity / Availability
Introduction to Enterprise Security Architecture by Praveen
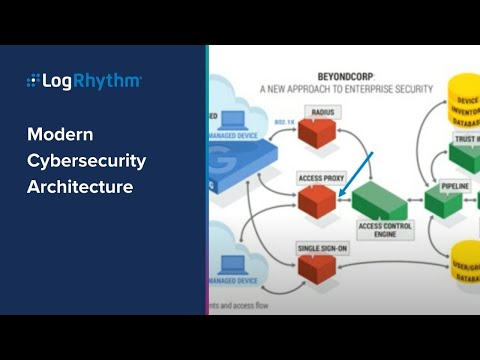
Modern Cybersecurity Architecture
Комментарии
 0:12:34
0:12:34
 0:17:34
0:17:34
 0:27:31
0:27:31
 0:16:08
0:16:08
 0:14:07
0:14:07
 0:09:27
0:09:27
 0:14:22
0:14:22
 0:31:15
0:31:15
 0:55:43
0:55:43
 0:04:07
0:04:07
 0:06:22
0:06:22
 0:08:56
0:08:56
 0:06:06
0:06:06
 0:05:15
0:05:15
 0:02:06
0:02:06
 0:10:22
0:10:22
 0:03:00
0:03:00
 0:01:30
0:01:30
 0:06:19
0:06:19
 1:09:05
1:09:05
 0:09:33
0:09:33
 0:03:23
0:03:23
 1:03:17
1:03:17
 1:02:41
1:02:41