filmov
tv
Foundations of Cryptography 1-1: The 5 Pillars of Information Security

Показать описание
🛡️ The Changing Business Climate: Learn about the rapid changes in the business world and why information security has become a top priority. We'll look at the rise in cybercrime, the impact of the pandemic on security, and the increasing demands from customers for robust information security practices.
📊 Five Pillars of Information Security: Discover the five pillars of information security—confidentiality, integrity, availability, authenticity, and non-repudiation. Understand how each pillar plays a crucial role in protecting sensitive information.
⚖️ Regulations and Laws: Explore the various laws and regulations designed to protect consumers, employees, and sensitive information. Understand the growing importance of cybersecurity insurance and the stringent requirements companies must meet to be covered.
🔍 The CIA Triad and Beyond: Dive into the CIA Triad (Confidentiality, Integrity, Availability) and learn about the additional pillars—authenticity and non-repudiation—emphasized by certifications like CISSP.
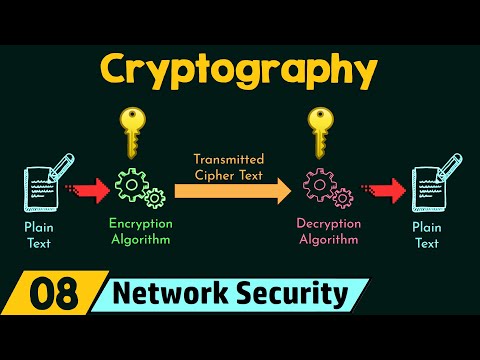
🔐 Cryptography's Role: Understand how cryptography underpins these pillars, ensuring data remains secure, authentic, and tamper-proof.
In this video, we'll cover the evolving importance of information security and the foundational pillars that support it. Don't forget to like and subscribe for more tech insights! #InformationSecurity #CyberSecurity #Cryptography
🌐 Connect With Us: Let us know your thoughts in the comment section
At TechKnowSurge, our mission is to empower purpose-driven students to learn and comprehend IT while making a positive impact on the world. Join us on this exciting journey!
 0:04:58
0:04:58
 0:03:23
0:03:23
 0:04:18
0:04:18
 0:03:30
0:03:30
 0:05:24
0:05:24
 0:01:01
0:01:01
 0:09:27
0:09:27
 0:01:36
0:01:36
 0:08:05
0:08:05
 0:01:37
0:01:37
 0:13:34
0:13:34
 0:16:33
0:16:33
 1:23:54
1:23:54
 0:01:24
0:01:24
 0:07:58
0:07:58
 0:11:55
0:11:55
 0:57:41
0:57:41
 0:01:12
0:01:12
 2:15:01
2:15:01
 1:12:45
1:12:45
 0:01:09
0:01:09
 1:02:31
1:02:31
 0:01:45
0:01:45
 0:10:01
0:10:01