filmov
tv
02 C Programming User Input Tutorial GCC

Показать описание
02 C Programming User Input Tutorial GCC
C Programming Tutorial 11 - C Basics Part 3 - Taking Input from User
C++ programming for beginners 02 - Variables and user input
Learn how to enter user input in C! ⌨️
String input in C || C Basics
How to Code in C++ E02: Variables and user input
C++Tutorial for Beginners 7 - User Input
C++ Programming Examples 02-3 Getting User Console Input
JavaScript One Shot Part 1 🚀 | Complete JS Tutorial for Beginners to Advanced | NextEra Coders
C Programming - Tutorial 4 (Getting User Input).avi
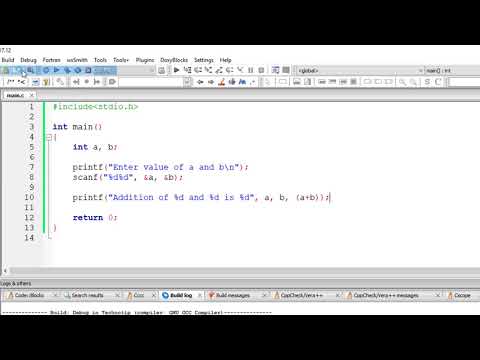
Addition of Two Numbers: C Programming
02_C Programming Language Basics Arabic (scanf, user input)
Printing star pattern using C Programming
C Programming | Add 2 numbers from user input ( with scanf )
Embedded Programming: User Input
Amazing Rotating Python Graphics Design using Turtle 🐢 #python #pythonshorts #coding #viral #design...
#7: Input and Output in C - Part 2 | C Programming for Beginners
Lecture 2 - Taking User Input | C/C++ Video Tutorials and Lectures for Beginners
C program | To calculate values using user input . ||Vector9412||
algorithm & flowchart problem #shorts #c programming
C++ or Java? Comment below #codingninjas #coding #programming #java #c++
C Programming Full Course for free ⚙️ (2025)
This mat helped me learn Java so fast 😭 #coding #java #programming #computer
nameof in C# is FAST
Комментарии
 0:07:45
0:07:45
 0:06:16
0:06:16
 0:04:53
0:04:53
 0:16:15
0:16:15
 0:00:13
0:00:13
 0:11:59
0:11:59
 0:09:36
0:09:36
 0:05:08
0:05:08
 6:54:36
6:54:36
 0:06:25
0:06:25
 0:01:29
0:01:29
 0:05:38
0:05:38
 0:00:34
0:00:34
 0:01:58
0:01:58
 0:11:57
0:11:57
 0:00:17
0:00:17
 0:06:34
0:06:34
 0:02:39
0:02:39
 0:02:22
0:02:22
 0:00:16
0:00:16
 0:00:15
0:00:15
 6:53:35
6:53:35
 0:00:17
0:00:17
 0:00:25
0:00:25