filmov
tv
Cryptography Fundamentals: Algorithms, Uses & Limitations Explained | Module 3

Показать описание
Welcome to our video on Module 3: Fundamentals of Cryptography, where we dive into the core concepts and techniques that underpin the security of information systems. In this video, you'll learn:
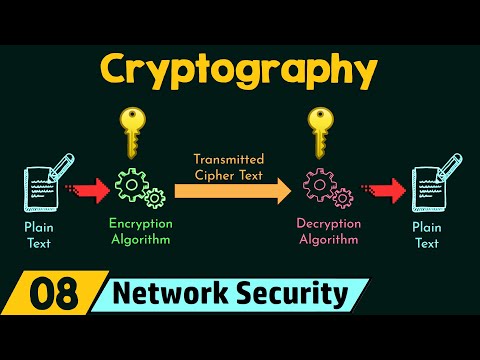
-Define Cryptography: Understand the basics of cryptography and its role in securing data.
-Describe Hash, Symmetric, and Asymmetric Cryptographic Algorithms: Gain insights into different types of cryptographic algorithms and their applications.
-List the Various Ways in Which Cryptography is Used: Discover the practical uses of cryptography in real-world scenarios.
-Explain Different Cryptographic Limitations and Attacks: Learn about the potential weaknesses in cryptographic systems and common attack methods.
-Enhance your knowledge of cryptographic principles and how they protect information in today's digital world!
Stay Connected: Subscribe to our channel for more insightful videos on information systems security. If you found this video helpful, please like it and comment with any questions or topics you'd like us to cover in future videos.
Follow Us:
Recommended Resources:
Textbook: Ciampa, M. (2025). CompTIA Security+ Guide to Network Security Fundamentals (8th ed.). Cengage. ISBN: 9798214000749
Cengage E-Text: From $44.99+ (Approximately)
VitalSource: From $50.99 (Approximately)
About the Instructor: Dr. Schuessler is a seasoned professor at Tarleton State University with extensive experience in information systems security. Join us as we break down complex topics into easy-to-understand lessons that will help you excel in your studies and career.
Watch Next:
Module 4: Advanced Cryptography:
Don’t forget to hit the notification bell so you never miss an update!
#CyberSecurity #InformationSecurity #SocialEngineering #DataProtection #cryptography
Special thanks to these influencers for their ongoing contributions to the field: @elithecomputerguy | @comptia | @hak5 | @powerdmarc | @CybraryIt | @HackTheBox | @RealTryHackMe | @ippsec | @SecurityWeekly | @TarletonState | @TarletonCoB
-Define Cryptography: Understand the basics of cryptography and its role in securing data.
-Describe Hash, Symmetric, and Asymmetric Cryptographic Algorithms: Gain insights into different types of cryptographic algorithms and their applications.
-List the Various Ways in Which Cryptography is Used: Discover the practical uses of cryptography in real-world scenarios.
-Explain Different Cryptographic Limitations and Attacks: Learn about the potential weaknesses in cryptographic systems and common attack methods.
-Enhance your knowledge of cryptographic principles and how they protect information in today's digital world!
Stay Connected: Subscribe to our channel for more insightful videos on information systems security. If you found this video helpful, please like it and comment with any questions or topics you'd like us to cover in future videos.
Follow Us:
Recommended Resources:
Textbook: Ciampa, M. (2025). CompTIA Security+ Guide to Network Security Fundamentals (8th ed.). Cengage. ISBN: 9798214000749
Cengage E-Text: From $44.99+ (Approximately)
VitalSource: From $50.99 (Approximately)
About the Instructor: Dr. Schuessler is a seasoned professor at Tarleton State University with extensive experience in information systems security. Join us as we break down complex topics into easy-to-understand lessons that will help you excel in your studies and career.
Watch Next:
Module 4: Advanced Cryptography:
Don’t forget to hit the notification bell so you never miss an update!
#CyberSecurity #InformationSecurity #SocialEngineering #DataProtection #cryptography
Special thanks to these influencers for their ongoing contributions to the field: @elithecomputerguy | @comptia | @hak5 | @powerdmarc | @CybraryIt | @HackTheBox | @RealTryHackMe | @ippsec | @SecurityWeekly | @TarletonState | @TarletonCoB
 0:21:51
0:21:51
 0:11:55
0:11:55
 0:04:40
0:04:40
 0:12:33
0:12:33
 0:32:46
0:32:46
 0:02:18
0:02:18
 0:08:40
0:08:40
 0:13:34
0:13:34
 0:06:03
0:06:03
 0:14:14
0:14:14
 2:15:01
2:15:01
 0:13:03
0:13:03
 0:11:11
0:11:11
 0:13:58
0:13:58
 0:07:31
0:07:31
 0:00:17
0:00:17
 0:38:36
0:38:36
 0:06:43
0:06:43
 0:00:08
0:00:08
 0:22:51
0:22:51
 0:05:17
0:05:17
 0:35:00
0:35:00
 0:19:13
0:19:13
 0:03:51
0:03:51