filmov
tv
Hashing and Hashing Algorithms - md5 sha1 sha256 sha2 sha3 - Cryptography Essentials

Показать описание
In this video, we dive into the fascinating world of hashing and how it transforms data. You'll learn how hashing algorithms, like MD5 and SHA, convert messages into unique, fixed-length strings called digests. Hashing plays a critical role in ensuring data integrity and security, making it a foundational concept in cryptography and networking.
We break down the basics of hashing with simple examples, showing you how a hashing algorithm works and why it's crucial for comparing and verifying data. We also touch on the efficiency and practical applications of hashing in bulk data processing.
💡 Key Takeaways:
- Understand how hashing algorithms transform data into a digest.
- Learn why hashing is essential for data integrity and security.
- Explore common hashing algorithms such as MD5, SHA-1, and SHA-256.
- Discover the differences between SHA-2 and SHA-3 families.
#DataIntegrity #DataHashing #HashingAlgorithms #HashingForBeginners #HashFunction
// CHAPTERS //
00:00 - Intro
00:12 - What is Hashing
01:44 - Hashing is Impossible to Reverse
02:20 - Hashing is Efficient
03:00 - Common Hashing Algorithms
04:17 - Hashing Examples
05:27 - Outro
// FULL SERIES - Cryptography Essentials //
This video is part of a 16-part series covering the essentials of modern Cryptography. Explained simply, and technically accurate.
The full series is available here:
00 Series Introduction
01 Hashing
02 Keys / Secret Keys
03 Symmetric Cryptography
04 Encryption
05 MAC / HMAC
06 Pseudo Random Function
07 Asymmetric Cryptography
08 Asymmetric Encryption (RSA)
09 Signatures
10 RSA Signatures
11 DSA Signatures
12 Key Exchanges
13 RSA Key Exchanges
14 DH Key Exchanges
15 Elliptic Curve Cryptography
// ADDITIONAL RESOURCES //
// SUPPORT PRACTICAL NETWORKING //
If this content benefited you, then here are TOTALLY FREE ways to show your appreciation:
- 👍 Like to help this video reach more viewers
- 💬 Comment to boost the channel's visibility
- 🔔 Subscribe to help me attract sponsors (this is the number they care about)
We break down the basics of hashing with simple examples, showing you how a hashing algorithm works and why it's crucial for comparing and verifying data. We also touch on the efficiency and practical applications of hashing in bulk data processing.
💡 Key Takeaways:
- Understand how hashing algorithms transform data into a digest.
- Learn why hashing is essential for data integrity and security.
- Explore common hashing algorithms such as MD5, SHA-1, and SHA-256.
- Discover the differences between SHA-2 and SHA-3 families.
#DataIntegrity #DataHashing #HashingAlgorithms #HashingForBeginners #HashFunction
// CHAPTERS //
00:00 - Intro
00:12 - What is Hashing
01:44 - Hashing is Impossible to Reverse
02:20 - Hashing is Efficient
03:00 - Common Hashing Algorithms
04:17 - Hashing Examples
05:27 - Outro
// FULL SERIES - Cryptography Essentials //
This video is part of a 16-part series covering the essentials of modern Cryptography. Explained simply, and technically accurate.
The full series is available here:
00 Series Introduction
01 Hashing
02 Keys / Secret Keys
03 Symmetric Cryptography
04 Encryption
05 MAC / HMAC
06 Pseudo Random Function
07 Asymmetric Cryptography
08 Asymmetric Encryption (RSA)
09 Signatures
10 RSA Signatures
11 DSA Signatures
12 Key Exchanges
13 RSA Key Exchanges
14 DH Key Exchanges
15 Elliptic Curve Cryptography
// ADDITIONAL RESOURCES //
// SUPPORT PRACTICAL NETWORKING //
If this content benefited you, then here are TOTALLY FREE ways to show your appreciation:
- 👍 Like to help this video reach more viewers
- 💬 Comment to boost the channel's visibility
- 🔔 Subscribe to help me attract sponsors (this is the number they care about)
Комментарии
 0:09:45
0:09:45
 0:02:36
0:02:36
 0:11:42
0:11:42
 0:10:21
0:10:21
 0:44:09
0:44:09
 0:18:40
0:18:40
 0:07:08
0:07:08
 0:03:52
0:03:52
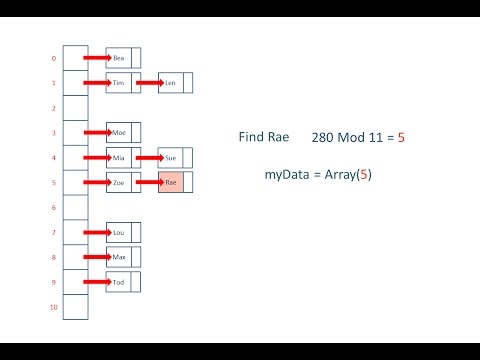 0:13:56
0:13:56
 0:08:04
0:08:04
 0:05:53
0:05:53
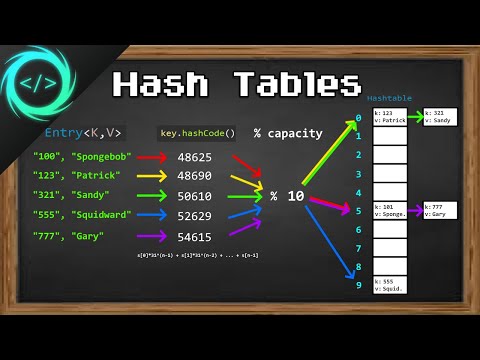 0:13:26
0:13:26
 0:52:55
0:52:55
![#032 [Data Structures]](https://i.ytimg.com/vi/mZFuZHOESEY/hqdefault.jpg) 0:13:48
0:13:48
 0:10:24
0:10:24
 0:10:59
0:10:59
 0:07:28
0:07:28
 0:06:03
0:06:03
 0:04:30
0:04:30
 0:07:27
0:07:27
 0:06:25
0:06:25
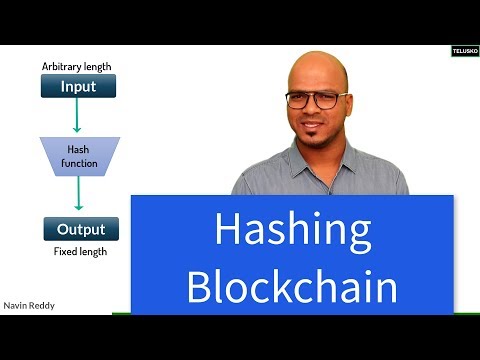 0:05:51
0:05:51
 0:03:36
0:03:36
 0:04:29
0:04:29