filmov
tv
WPA Decryption Using Wireshark
Показать описание
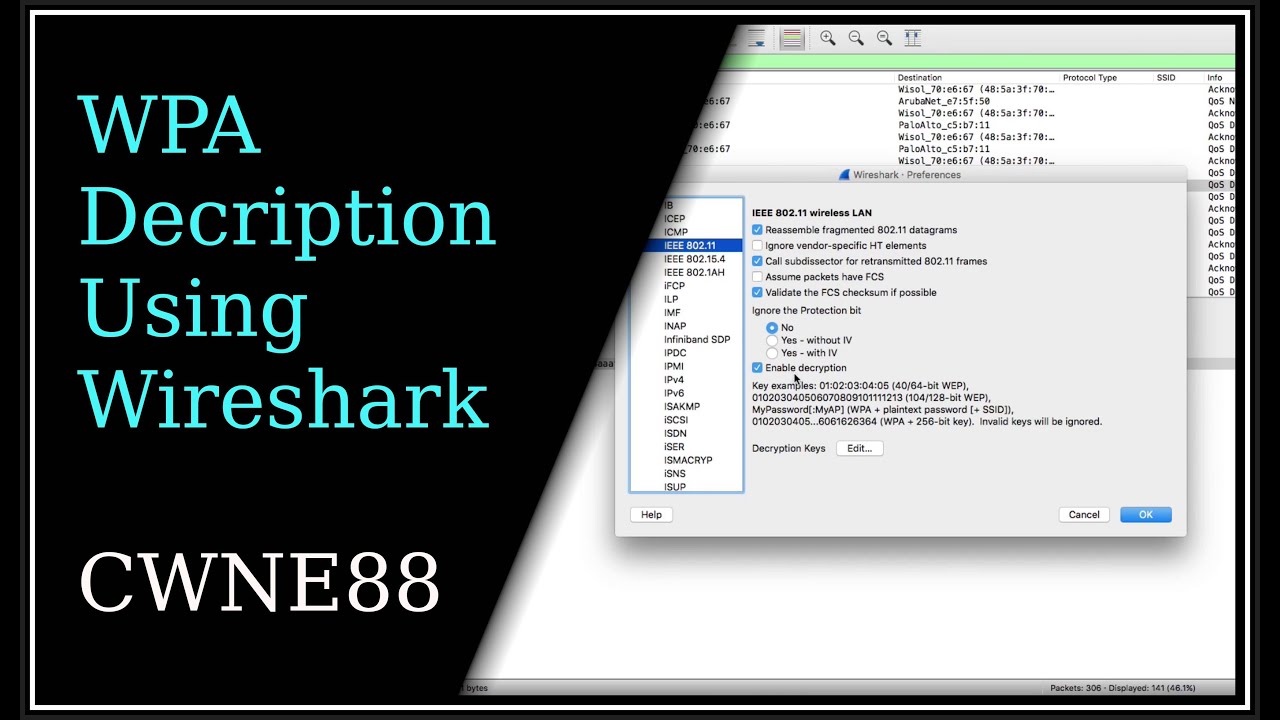
This method enables you to see the actual IP traffic of a Wi-Fi client that uses WPA encryption.
You must know the WPA passphrase, and capture a 4-way handshake for that client.
You must know the WPA passphrase, and capture a 4-way handshake for that client.
WPA Decryption Using Wireshark
Wireshark Decrypting 802 11 - evidence07
How to DECRYPT HTTPS Traffic with Wireshark
How To Decrypt WPA2 with Wireshark
Wi-Fi WPA2 handshake and cracking it
WiFi Hacking and Security - Decrypting WPA WPA2 Traffic
Decrypting a WEP Trace file With Wireshark
Grab Passwords and User Names with Wireshark
Wireshark Wi-Fi Capturing
Using Wireshark's Decode As Feature
WPA Key Capturing and Cracking|| Wi-Fi Hacking|| Wireshark || Aircrack-ng ||
Wireshark Learning Series: HTTPS Decrypt
Capturing WiFi Traffic using Wireshark
Wirelss Packet Capture and Decryption using Omnipeek (WPA/WPA2), by Advanced Network Devices Inc.
PicoCTF Walkthru [55] - WPA'ing Out (WiFi PW cracking, Wireshark)
Decrypt HTTPS traffic with Wireshark on Windows
Decrypt SSL / TLS traffic using wireshark.
Using Wireshark to decrypt tls encrypted file with private key
Wireshark: Basic Tutorial on TLSv1.2 Decryption
Wpa handshake crack😁😁😁
Decrypt TLS Wireshark
SSL Decryption using Wireshark on Windows
find password in handshake file online method | kali linux 
Wireshark Tutorial: Decrypting HTTPS Traffic
Комментарии
 0:02:17
0:02:17
 0:04:12
0:04:12
 0:08:41
0:08:41
 0:02:39
0:02:39
 0:12:59
0:12:59
 0:01:39
0:01:39
 0:02:04
0:02:04
 0:03:07
0:03:07
 0:06:25
0:06:25
 0:02:25
0:02:25
 0:06:34
0:06:34
 0:04:34
0:04:34
 0:04:20
0:04:20
 0:07:22
0:07:22
![PicoCTF Walkthru [55]](https://i.ytimg.com/vi/mAZ7PjEfWU0/hqdefault.jpg) 0:20:10
0:20:10
 0:03:59
0:03:59
 0:14:27
0:14:27
 0:02:17
0:02:17
 0:09:57
0:09:57
 0:00:24
0:00:24
 0:05:35
0:05:35
 0:05:57
0:05:57
 0:02:55
0:02:55
 0:19:53
0:19:53