filmov
tv
Session Hijacking and Cross site Request CompTIA SY0 601 | Security + | Security + Certification
Показать описание
#securiumsolutions #blackbox #whitebox #penetrationtesting #webtesting #webpenetrationtesting #serverpenetrationtesting #networkpenetrationtesting #webhacking #cybersecurityservices #cybersecurity #cybersecuritycompany #bughutingservices
Get Special Offer Contact Us And Get More Information Call & WhatsApp - +91 - 9310-62-4042 | +1 - 201-549-9007
SESSION HIJACKING AND CROSS-SITE REQUEST FORGERY
In the context of a web application, session hijacking most often means replaying a cookie in some way. Attackers can sniff network traffic to obtain session cookies sent over an unsecured network, like a public Wi-Fi hotspot. To counter cookie hijacking, you can encrypt cookies during transmission, delete cookies from the client's browser cache when the client terminates the session, and design your web app to deliver a new cookie with each new session between the app and the client's browser.
Session prediction attacks focus on identifying possible weaknesses in the generation of session tokens that will enable an attacker to predict future valid session values. If an attacker can predict the session token, then the attacker can take over a session that has yet to be established. A session token must be generated using a non-predictable algorithm, and it must not reveal any information about the session client. In addition, proper session management dictates that apps limit the lifespan of a session and require re-authentication after a certain period.
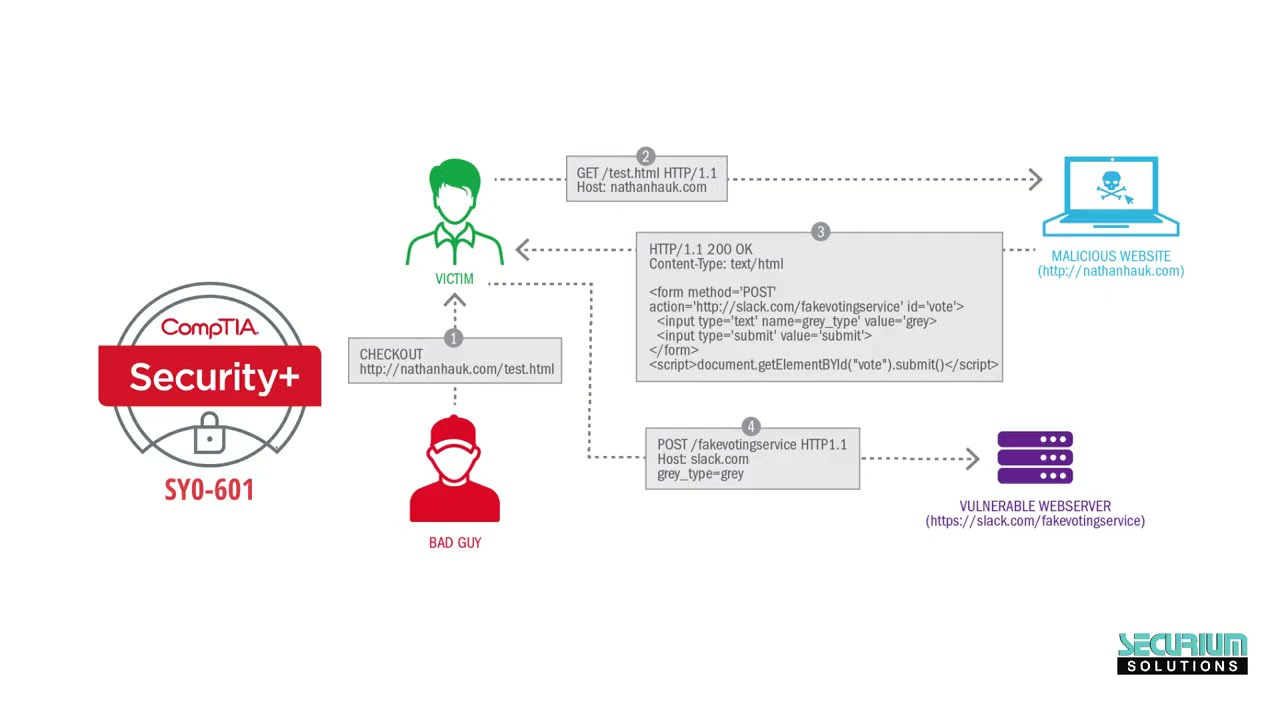
Cross-Site Request Forgery
A client-side or cross-site request forgery (CSRF or XSRF) can exploit applications that use cookies to authenticate users and track sessions. To work, the attacker must convince the victim to start a session with the target site. The attacker must then pass an HTTP request to the victim's browser that spoofs an action on the target site, such as changing a password or an email address. This request could be disguised in a few ways and so could be accomplished without the victim necessarily having to click a link. If the target site assumes that the browser is authenticated because there is a valid session cookie and doesn't complete any additional authorization process on the attacker's input (or if the attacker is able to spoof the authorization), it will accept the input as genuine. This is also referred to as a confused deputy attack (the point being that the user and the user's browser are not necessarily the same thing).
Securium Solutions is a cybersecurity company in Noida this company provides all kind of penetration testing services over the world such as Network Penetration Testing, Server Penetration Testing, Black Box Penetration Testing, White Box Testing, Web Application Testing, Android And iPhone Application Testing, as well as securium solutions, provide All EC-Council's Cyber Security Certification like as CEHv11, CHFI, LPT, ECSA, CPENT, CSCU, etc.
Clickjacking
Clickjacking is an attack where what the user sees and trusts as a web application with some sort of login page or form contains a malicious layer or invisible iFrame (a web page embedded inside another web page) that allows an attacker to intercept or redirect user input. Clickjacking can be launched using any type of compromise that allows the adversary to run arbitrary code as a script. Clickjacking can be mitigated by using HTTP response headers that instruct the browser not to open frames from different origins (domains) and by ensuring that any buttons or input boxes on a page are positioned on the top-most layer.
SSL Strip
Get Special Offer Contact Us And Get More Information Call & WhatsApp - +91 - 9310-62-4042 | +1 - 201-549-9007
SESSION HIJACKING AND CROSS-SITE REQUEST FORGERY
In the context of a web application, session hijacking most often means replaying a cookie in some way. Attackers can sniff network traffic to obtain session cookies sent over an unsecured network, like a public Wi-Fi hotspot. To counter cookie hijacking, you can encrypt cookies during transmission, delete cookies from the client's browser cache when the client terminates the session, and design your web app to deliver a new cookie with each new session between the app and the client's browser.
Session prediction attacks focus on identifying possible weaknesses in the generation of session tokens that will enable an attacker to predict future valid session values. If an attacker can predict the session token, then the attacker can take over a session that has yet to be established. A session token must be generated using a non-predictable algorithm, and it must not reveal any information about the session client. In addition, proper session management dictates that apps limit the lifespan of a session and require re-authentication after a certain period.
Cross-Site Request Forgery
A client-side or cross-site request forgery (CSRF or XSRF) can exploit applications that use cookies to authenticate users and track sessions. To work, the attacker must convince the victim to start a session with the target site. The attacker must then pass an HTTP request to the victim's browser that spoofs an action on the target site, such as changing a password or an email address. This request could be disguised in a few ways and so could be accomplished without the victim necessarily having to click a link. If the target site assumes that the browser is authenticated because there is a valid session cookie and doesn't complete any additional authorization process on the attacker's input (or if the attacker is able to spoof the authorization), it will accept the input as genuine. This is also referred to as a confused deputy attack (the point being that the user and the user's browser are not necessarily the same thing).
Securium Solutions is a cybersecurity company in Noida this company provides all kind of penetration testing services over the world such as Network Penetration Testing, Server Penetration Testing, Black Box Penetration Testing, White Box Testing, Web Application Testing, Android And iPhone Application Testing, as well as securium solutions, provide All EC-Council's Cyber Security Certification like as CEHv11, CHFI, LPT, ECSA, CPENT, CSCU, etc.
Clickjacking
Clickjacking is an attack where what the user sees and trusts as a web application with some sort of login page or form contains a malicious layer or invisible iFrame (a web page embedded inside another web page) that allows an attacker to intercept or redirect user input. Clickjacking can be launched using any type of compromise that allows the adversary to run arbitrary code as a script. Clickjacking can be mitigated by using HTTP response headers that instruct the browser not to open frames from different origins (domains) and by ensuring that any buttons or input boxes on a page are positioned on the top-most layer.
SSL Strip
 0:08:29
0:08:29
 0:05:20
0:05:20
 0:14:04
0:14:04
 0:06:00
0:06:00
 0:04:41
0:04:41
 0:01:51
0:01:51
 0:05:33
0:05:33
 0:05:08
0:05:08
 0:00:59
0:00:59
 0:04:01
0:04:01
 0:02:07
0:02:07
 0:00:22
0:00:22
 0:02:33
0:02:33
 0:09:58
0:09:58
 0:09:31
0:09:31
 0:09:01
0:09:01
 0:07:05
0:07:05
 0:07:32
0:07:32
 0:09:51
0:09:51
 0:02:56
0:02:56
 0:04:17
0:04:17
 0:05:48
0:05:48
 0:00:58
0:00:58
 0:00:51
0:00:51