filmov
tv
Exploit Tomcat CVE & Create Backdoors for Reverse Shell Access | Ethical Hacking Tutorial

Показать описание
#learncybersecuritybd
🔐 In this ethical hacking tutorial, you'll learn how to *exploit Apache Tomcat CVE* by uploading a malicious *WAR file* to gain *reverse shell access*. We’ll show how to *create a backdoor* using `msfvenom`, set up a *reverse TCP payload*, and connect through *Metasploit* to control the target system from your *home lab*.
*Samba file Share Exploitation- CVE*
*I have described all those things in my blog so if anyone need to know more can visit.*
📌 This step-by-step guide is perfect for beginners and cybersecurity learners who want to understand:
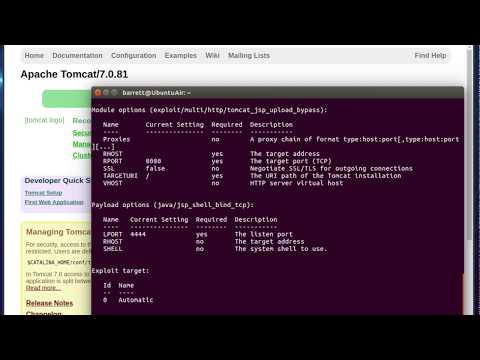
- How to *create and deploy WAR files in Tomcat*
- Generating *Java-based payloads* with `msfvenom`
- Setting up a *reverse backdoor*
- Performing a *reverse shell attack* using *Metasploit*
- Using *Linux reverse shells* and *Java TCP backdoors*
- Hands-on *Tomcat exploitation techniques*
- Running *reverse shell scripts** in *Kali Linux*
- How to exploit tomcat server with war file.
🧪 Whether you're building your *lab environment* or learning to craft a *reverse shell backdoor script*, this video walks you through every step with explanations.
📂 Topics Covered:
- Tomcat CVE Exploitation
- Creating & Uploading WAR Files
- msfvenom Reverse Shell Payloads
- Backdoor Script Execution
- Reverse TCP Connections
- Real-World Penetration Testing in a Lab
🛠 Tools Used:
- Apache Tomcat
- Metasploit Framework
- msfvenom
- Kali Linux
⚠️ *This content is for educational purposes only. Do not attempt these techniques on systems you do not own or have permission to test.*
# You May get Idea with the Video
- tomcat cve exploitation tutorial
- how to exploit tomcat server
- apache tomcat vulnerability explained
- cve-2020-1938 ghostcat exploit
- tomcat war file upload exploit
- beginner guide to tomcat hacking
- apache tomcat server hacking
- cve tomcat metasploit module
- remote code execution tomcat
- exploit tomcat ajp vulnerability
- cve-2017-12615 tomcat exploit
- tomcat exploitation with metasploit
- ethical hacking apache tomcat
- web server exploitation for beginners
- how hackers exploit apache tomcat
- nmap tomcat vulnerability scan
- tomcat ajp protocol exploit tutorial
- cve-2020-1938 metasploit tutorial
- upload reverse shell to tomcat
- apache tomcat rce vulnerability
# Related Videos:
*Network Under Cyber Attack with Wireshark*
*Network Discovery Made Easy*
*Linux Firewall for Linux server security*
*linux log analysis*
*Linux Networking Commands*
*The Commands That Matter Most!*
*Parrot OS USB Persistence for Ethical Hackers*
# Where in the video You'll Learn:
00:00 About backdoors with msfvenom
02:40 Tomcat backdoor web exploitation
03:19 Port Discovery with nmap
04:59 Identify RHOST IP and Port
05:49 Search Payload from msfconsol .
07:29 Set remote port from msfconsol
08:29 How to set username and password in metasploit
09:19 How to set TARGETURI in metasploit
08:39 How to set Payload in metasploit
10:19 How to run exploit in metasploit
12:49 How to make WAR file to use msfvenom
15:09 How to upload WAR file
15:49 How to Execute war file
16:29 How to connect remote site to use backdoor
*My Social Links*
*Facebook*
*Iinstagram*
*Linkedin*
*My Blog here you will find lots of content*
#TomcatExploit #MetasploitTutorial #reverseshell #BackdoorScript #msfvenom #ethicalhacking #ReverseTCP #TomcatCVE #payload #WARFile #kalilinux #JavaPayload #homelab #LinuxReverseShell #cybersecurity #cve #exploit #apache #tomcat #cybersecuritytutorial #ethicalhackingtutorial #exploitation #pentesting #metasploit #metasploitable3 #homelab #tomcat #apache #payload #metasploitframework #vulnerability #ethicalhackingtutorial #vulnerabilitymanagement #websitesecurity #linuxsecurity #linuxterminal #linuxcommandlinetutorial #linuxskills
🔐 In this ethical hacking tutorial, you'll learn how to *exploit Apache Tomcat CVE* by uploading a malicious *WAR file* to gain *reverse shell access*. We’ll show how to *create a backdoor* using `msfvenom`, set up a *reverse TCP payload*, and connect through *Metasploit* to control the target system from your *home lab*.
*Samba file Share Exploitation- CVE*
*I have described all those things in my blog so if anyone need to know more can visit.*
📌 This step-by-step guide is perfect for beginners and cybersecurity learners who want to understand:
- How to *create and deploy WAR files in Tomcat*
- Generating *Java-based payloads* with `msfvenom`
- Setting up a *reverse backdoor*
- Performing a *reverse shell attack* using *Metasploit*
- Using *Linux reverse shells* and *Java TCP backdoors*
- Hands-on *Tomcat exploitation techniques*
- Running *reverse shell scripts** in *Kali Linux*
- How to exploit tomcat server with war file.
🧪 Whether you're building your *lab environment* or learning to craft a *reverse shell backdoor script*, this video walks you through every step with explanations.
📂 Topics Covered:
- Tomcat CVE Exploitation
- Creating & Uploading WAR Files
- msfvenom Reverse Shell Payloads
- Backdoor Script Execution
- Reverse TCP Connections
- Real-World Penetration Testing in a Lab
🛠 Tools Used:
- Apache Tomcat
- Metasploit Framework
- msfvenom
- Kali Linux
⚠️ *This content is for educational purposes only. Do not attempt these techniques on systems you do not own or have permission to test.*
# You May get Idea with the Video
- tomcat cve exploitation tutorial
- how to exploit tomcat server
- apache tomcat vulnerability explained
- cve-2020-1938 ghostcat exploit
- tomcat war file upload exploit
- beginner guide to tomcat hacking
- apache tomcat server hacking
- cve tomcat metasploit module
- remote code execution tomcat
- exploit tomcat ajp vulnerability
- cve-2017-12615 tomcat exploit
- tomcat exploitation with metasploit
- ethical hacking apache tomcat
- web server exploitation for beginners
- how hackers exploit apache tomcat
- nmap tomcat vulnerability scan
- tomcat ajp protocol exploit tutorial
- cve-2020-1938 metasploit tutorial
- upload reverse shell to tomcat
- apache tomcat rce vulnerability
# Related Videos:
*Network Under Cyber Attack with Wireshark*
*Network Discovery Made Easy*
*Linux Firewall for Linux server security*
*linux log analysis*
*Linux Networking Commands*
*The Commands That Matter Most!*
*Parrot OS USB Persistence for Ethical Hackers*
# Where in the video You'll Learn:
00:00 About backdoors with msfvenom
02:40 Tomcat backdoor web exploitation
03:19 Port Discovery with nmap
04:59 Identify RHOST IP and Port
05:49 Search Payload from msfconsol .
07:29 Set remote port from msfconsol
08:29 How to set username and password in metasploit
09:19 How to set TARGETURI in metasploit
08:39 How to set Payload in metasploit
10:19 How to run exploit in metasploit
12:49 How to make WAR file to use msfvenom
15:09 How to upload WAR file
15:49 How to Execute war file
16:29 How to connect remote site to use backdoor
*My Social Links*
*Facebook*
*Iinstagram*
*Linkedin*
*My Blog here you will find lots of content*
#TomcatExploit #MetasploitTutorial #reverseshell #BackdoorScript #msfvenom #ethicalhacking #ReverseTCP #TomcatCVE #payload #WARFile #kalilinux #JavaPayload #homelab #LinuxReverseShell #cybersecurity #cve #exploit #apache #tomcat #cybersecuritytutorial #ethicalhackingtutorial #exploitation #pentesting #metasploit #metasploitable3 #homelab #tomcat #apache #payload #metasploitframework #vulnerability #ethicalhackingtutorial #vulnerabilitymanagement #websitesecurity #linuxsecurity #linuxterminal #linuxcommandlinetutorial #linuxskills
Комментарии
 0:19:02
0:19:02
 0:11:19
0:11:19
 0:21:49
0:21:49
 0:02:20
0:02:20
 0:12:19
0:12:19
 0:08:12
0:08:12
 0:32:44
0:32:44
 0:14:26
0:14:26
 0:00:56
0:00:56
 0:14:28
0:14:28
 1:05:24
1:05:24
 0:08:21
0:08:21
 0:02:25
0:02:25
 0:04:17
0:04:17
 0:20:01
0:20:01
 0:00:05
0:00:05
 0:01:12
0:01:12
 0:02:59
0:02:59
 0:01:15
0:01:15
 0:06:29
0:06:29
 0:02:51
0:02:51
 0:09:38
0:09:38
 0:00:18
0:00:18
 0:08:50
0:08:50