filmov
tv
Can C be Memory Safe?

Показать описание
Can C be Memory Safe?
how can memory safe code STOP HACKERS?
Why the sudden attention on 'memory safe' languages like Rust?
Memory Safe Languages DO NOT PREVENT MEMORY LEAKS
Explaining memory safety
Memory Safety: Rust vs. C - Robert Seacord - NDC TechTown 2024
How rust forces you to respect memory
i wrote my own memory allocator in C to prove a point
System Security: Tightly Seal Your Sensitive Pointers with PACTight by Dr. Mohannad Ismail (2024)
Finally solve memory leaks in C++!
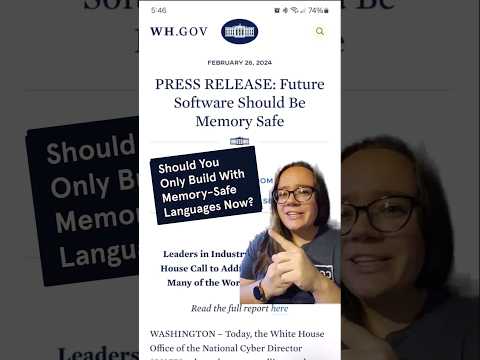
Do developers need to use memory-safe programming languages now? 🔐
[OOPSLA23] Fat Pointers for Temporal Memory Safety of C
Good practice for freeing memory in C
-memory-safe C++ - Jim Radigan - CppCon 2022
2020 LLVM Developers’ Meeting: “Checked C: Adding Memory Safety to LLVM”
This Is How Rust Stops Memory Leaks
A demo of a memory-safe C called Fil-C
What is memory leak?
memory safe c jim radigan cppcon 2022
CISA is NOT Using Memory Safe Code #cisa #infosecnews #podcastclips #code #opensource #projects
All The Memory Safety Of C Combined With All The Blazing Speed Of JavaScript -Sarah Lim
Automated Code Repair for Memory Safety
CONFidence 2014: Preventing violation of memory safety in C/C++ software - Andreas Bogk
The Origins of Process Memory | Exploring the Use of Various Memory Allocators in Linux C
Комментарии
 0:00:51
0:00:51
 0:07:43
0:07:43
 0:04:38
0:04:38
 0:23:42
0:23:42
 0:05:16
0:05:16
 1:00:54
1:00:54
 0:06:01
0:06:01
 0:05:23
0:05:23
 0:25:07
0:25:07
 0:08:03
0:08:03
 0:01:00
0:01:00
![[OOPSLA23] Fat Pointers](https://i.ytimg.com/vi/Pebo1dvab5A/hqdefault.jpg) 0:16:56
0:16:56
 0:08:17
0:08:17
 1:05:45
1:05:45
 0:35:05
0:35:05
 0:05:53
0:05:53
 0:19:13
0:19:13
 0:03:22
0:03:22
 0:07:19
0:07:19
 0:00:25
0:00:25
 0:31:49
0:31:49
 0:29:24
0:29:24
 0:33:37
0:33:37
 0:09:03
0:09:03