filmov
tv
What is a Phishing Attack? Types of Phishing attack | Email Phising Spear Phishing Smishing Vishing

Показать описание
What is a Phishing attack?
A Phishing attack is a social engineering cyber attack that's main aims are to steal personal information, gain unauthorized access to accounts or install malware on a device. We'll look at 5 common types of Phishing. Email Phishing, Spear Phishing, Smishing, Vishing and Whaling.
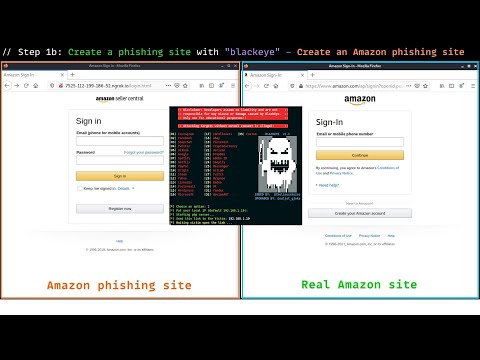
Lets start with the most common type and one everyone has likely come across before at some point, email phishing. An attacker sends an email to a huge list of email addresses they have obtained. They will pretend to be from a reputable company such as a bank or online shopping site like amazon and usually say there has been an issue with your account, please click the follow link to resolve it. This can cause panic by claiming a transaction has been made from your bank account that you know you didn't make, causing you to be more likely to click the link in the email to get it sorted out asap without fully thinking it through. Once you've clicked the link it will usually take you to a fake site the attacker has created, a fake online banking site for example. Once the victim has entered their login credentials on what they think is their legitimate online banking site these credentials are given straight to the attacker, giving them full access of the victims account. A good way to protect yourself from this is to always check the email address an email has been received from is official and to check for spelling and grammatical errors in the email as these are usually a dead give away. There's also likely to be a generic greeting as these emails are sent to 1000's of people at once.
Spear Fishing is similar to email phishing with one key difference, they target one small group or individual person rather than 1000's at once. The message or email sent to the victim will likely contain their name, job title, company or any information specific to that person or group making it appear more genuine and therefor more likely for the victim to click the link or provide the information. An example could be sending an email to a HR department pretending to be a new starter at the company and asking a question a on the employee handbook, they mention they have attached the document they're confused about. Once the HR worker opens they link the attacker can install malware on their device or take them to another fake website to trick them into providing their login details. This attack is more likely to work as its targeted at the HR department who this may appear as a genuine query to.
Smishing is a very similar type of attack, however instead of using email or social media a text message is used. The name Smishing comes from SMS Text. A common example here is getting a text from a number claiming that your parcel was unable to be delivered and to click the link to re arrange delivery, credentials will then be stolen just like the previous attacks mentioned or payment will be requested for the fake re arranged delivery. This is usually fairly easy to spot as the phone number sending you the text will not be an official number and likely just another mobile number.
The next type of Fishing we'll look at is Vishing, this is where a voice call is used as the method of contacting the victim. A well known and well used example of Vishing is an attacker calling pretending to be from Microsoft tech support. They will often say they've detected a virus on your PC and request payment from you to remove the virus or update you to the latest anti virus software which is often just malware. To stop vishing is easy, never let someone take remote access of your PC or make payment to them without being 100% sure of their identity.
The final type of attack we'll look at is Whaling, this is where someone high up in an organisation such as a CEO is targeted. They may be sent an email with an attachment stating the company is in legal trouble or claim they have a damaging story about the company. This is designed to make the victim panic and open the attachment without thinking if this is likely to be genuine. If we use the legal trouble email as an example when they open the link or attachment they may be asked to enter sensitive information about the company to confirm their identity which is then passed straight onto the attacker.
Thanks for watching! Please consider liking and subscribing if you found this video useful.
#phishing #cybersecurity #smishing #vishing
A Phishing attack is a social engineering cyber attack that's main aims are to steal personal information, gain unauthorized access to accounts or install malware on a device. We'll look at 5 common types of Phishing. Email Phishing, Spear Phishing, Smishing, Vishing and Whaling.
Lets start with the most common type and one everyone has likely come across before at some point, email phishing. An attacker sends an email to a huge list of email addresses they have obtained. They will pretend to be from a reputable company such as a bank or online shopping site like amazon and usually say there has been an issue with your account, please click the follow link to resolve it. This can cause panic by claiming a transaction has been made from your bank account that you know you didn't make, causing you to be more likely to click the link in the email to get it sorted out asap without fully thinking it through. Once you've clicked the link it will usually take you to a fake site the attacker has created, a fake online banking site for example. Once the victim has entered their login credentials on what they think is their legitimate online banking site these credentials are given straight to the attacker, giving them full access of the victims account. A good way to protect yourself from this is to always check the email address an email has been received from is official and to check for spelling and grammatical errors in the email as these are usually a dead give away. There's also likely to be a generic greeting as these emails are sent to 1000's of people at once.
Spear Fishing is similar to email phishing with one key difference, they target one small group or individual person rather than 1000's at once. The message or email sent to the victim will likely contain their name, job title, company or any information specific to that person or group making it appear more genuine and therefor more likely for the victim to click the link or provide the information. An example could be sending an email to a HR department pretending to be a new starter at the company and asking a question a on the employee handbook, they mention they have attached the document they're confused about. Once the HR worker opens they link the attacker can install malware on their device or take them to another fake website to trick them into providing their login details. This attack is more likely to work as its targeted at the HR department who this may appear as a genuine query to.
Smishing is a very similar type of attack, however instead of using email or social media a text message is used. The name Smishing comes from SMS Text. A common example here is getting a text from a number claiming that your parcel was unable to be delivered and to click the link to re arrange delivery, credentials will then be stolen just like the previous attacks mentioned or payment will be requested for the fake re arranged delivery. This is usually fairly easy to spot as the phone number sending you the text will not be an official number and likely just another mobile number.
The next type of Fishing we'll look at is Vishing, this is where a voice call is used as the method of contacting the victim. A well known and well used example of Vishing is an attacker calling pretending to be from Microsoft tech support. They will often say they've detected a virus on your PC and request payment from you to remove the virus or update you to the latest anti virus software which is often just malware. To stop vishing is easy, never let someone take remote access of your PC or make payment to them without being 100% sure of their identity.
The final type of attack we'll look at is Whaling, this is where someone high up in an organisation such as a CEO is targeted. They may be sent an email with an attachment stating the company is in legal trouble or claim they have a damaging story about the company. This is designed to make the victim panic and open the attachment without thinking if this is likely to be genuine. If we use the legal trouble email as an example when they open the link or attachment they may be asked to enter sensitive information about the company to confirm their identity which is then passed straight onto the attacker.
Thanks for watching! Please consider liking and subscribing if you found this video useful.
#phishing #cybersecurity #smishing #vishing
 0:06:48
0:06:48
 0:02:57
0:02:57
 0:00:40
0:00:40
 0:17:54
0:17:54
 0:07:54
0:07:54
 0:01:49
0:01:49
 0:05:22
0:05:22
 0:04:21
0:04:21
 0:01:19
0:01:19
 0:02:50
0:02:50
 0:05:35
0:05:35
 0:02:10
0:02:10
 0:01:33
0:01:33
 0:01:51
0:01:51
 0:03:44
0:03:44
 0:02:55
0:02:55
 0:03:02
0:03:02
 0:08:55
0:08:55
 0:07:53
0:07:53
 0:07:47
0:07:47
 0:04:31
0:04:31
 0:11:14
0:11:14
 0:10:00
0:10:00
 0:04:06
0:04:06