filmov
tv
SSLv3 Poodle Vulnerability | Password theft
Показать описание
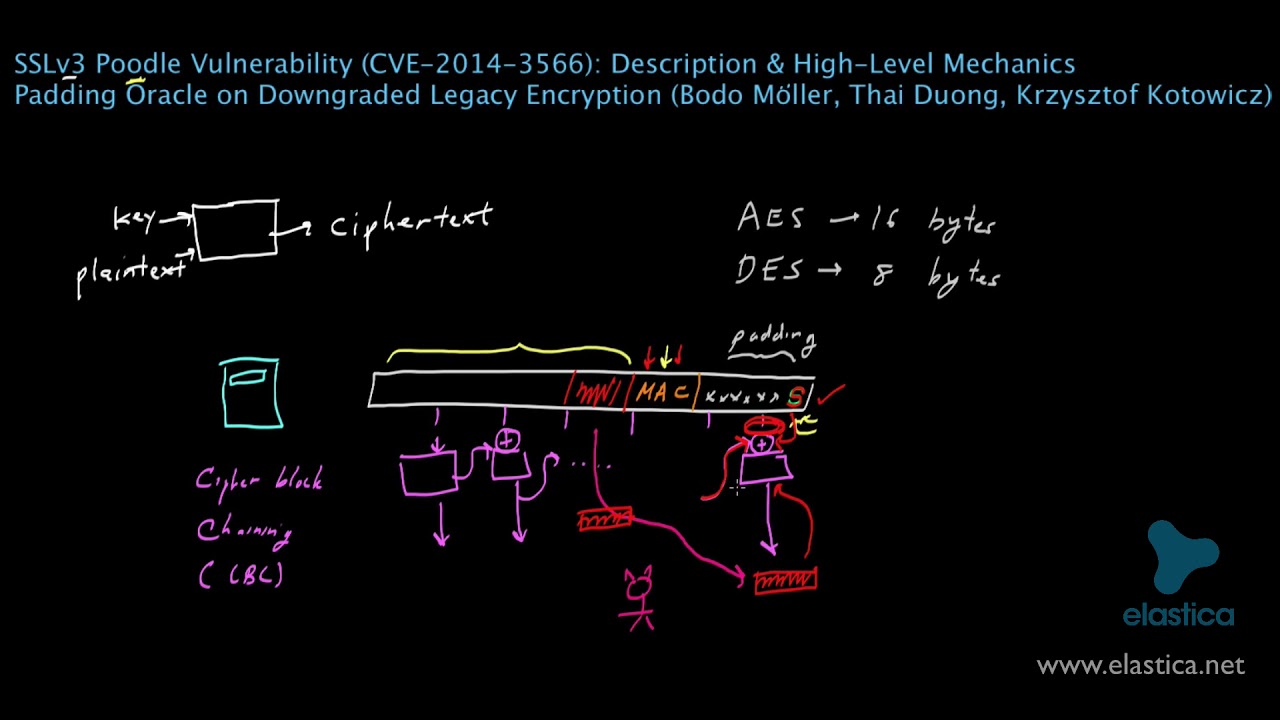
All systems and applications utilizing the Secure Socket Layer (SSL) 3.0 with cipher-block chaining (CBC) mode ciphers may be vulnerable. However, the POODLE (Padding Oracle On Downgraded Legacy Encryption) attack demonstrates this vulnerability using web browsers and web servers, which is one of the most likely exploitation scenarios.
Some Transport Layer Security (TLS) implementations are also vulnerable to the POODLE attack.
The POODLE attack can be used against any system or application that supports SSL 3.0 with CBC mode ciphers. This affects most current browsers and websites, but also includes any software that either references a vulnerable SSL/TLS library (e.g. OpenSSL) or implements the SSL/TLS protocol suite itself. By exploiting this vulnerability in a likely web-based scenario, an attacker can gain access to sensitive data passed within the encrypted web session, such as passwords, cookies and other authentication tokens that can then be used to gain more complete access to a website (impersonating that user, accessing database content, etc.).
Subscribe and share!
Some Transport Layer Security (TLS) implementations are also vulnerable to the POODLE attack.
The POODLE attack can be used against any system or application that supports SSL 3.0 with CBC mode ciphers. This affects most current browsers and websites, but also includes any software that either references a vulnerable SSL/TLS library (e.g. OpenSSL) or implements the SSL/TLS protocol suite itself. By exploiting this vulnerability in a likely web-based scenario, an attacker can gain access to sensitive data passed within the encrypted web session, such as passwords, cookies and other authentication tokens that can then be used to gain more complete access to a website (impersonating that user, accessing database content, etc.).
Subscribe and share!
SSLv3 Poodle Vulnerability | Password theft
What is POODLE attack & TLS_FALLBACK_SCSV | Test POODLE Vulnerability Using testssl | Secure Ngi...
POODLE attack | Vulnerability in the SSL 3.0 #shorts
SSLV3-Vulnerability-Part1
The POODLE bug! SSL vulnerability explained | Graham Cluley
Ubuntu: How do I patch/workaround SSLv3 POODLE vulnerability (CVE-2014-3566)?
What is Beast and Poodle attack | How do they work | What's the actual difference between them?
SSL POODLE Attack - Definition and Prevention
Poodle SSLv3 Vulnerability in Telugu (Practical) | Cyber Security | Bug Bounty | Telugu White Hats
Poodle-me: SSL vulnerability scanner
POODLE Attack
A2SV(Auto Scanning to SSL Vulnerability | How To Find SSL Vulnerability
Docker Images and Poodle Bleed SSL Vulnerability
On IIS, how do I patch the SSL 3.0 POODLE vulnerability (CVE-2014-3566)? (8 Solutions!!)
SSLV3-Vulnerability-Part2
POODLE Vulnerability
DevOps & SysAdmins: POODLE: SSLv3 vulnerability (CVE-2014-3566) with Apache24 on FreeBSD-9.2
Twitter Kills Support For SSL 3.0 In Wake Of Poodle Vulnerability
FLIPKART POODLE VULNERABILITY
What You Need To Know About The Poodle Bug | TIME
Poodle Vulnerability Mitigation in client side
MassBleed SSL Vulnerability Scanner
POODLE attack - Padding Oracle On Downgraded Legacy Encryption (TLS Academy)
Poodle: Schutz vor SSL 3.0 Sicherheitslücke
Комментарии
 0:13:10
0:13:10
 0:07:39
0:07:39
 0:00:32
0:00:32
 0:14:47
0:14:47
 0:04:05
0:04:05
 0:02:51
0:02:51
 0:04:21
0:04:21
 0:09:09
0:09:09
 0:06:16
0:06:16
 0:02:33
0:02:33
 0:16:49
0:16:49
 0:05:12
0:05:12
 0:05:33
0:05:33
 0:04:30
0:04:30
 0:03:43
0:03:43
 0:02:40
0:02:40
 0:02:33
0:02:33
 0:00:43
0:00:43
 0:16:03
0:16:03
 0:01:05
0:01:05
 0:09:10
0:09:10
 0:01:36
0:01:36
 0:07:59
0:07:59
 0:01:01
0:01:01