filmov
tv
How To Use Nessus Vulnerability Scanner | Beginner’s Guide to Nessus | Nessus Vulnerability Scanner

Показать описание
In this tutorial, you will learn Nessus Vulnerability Scanner
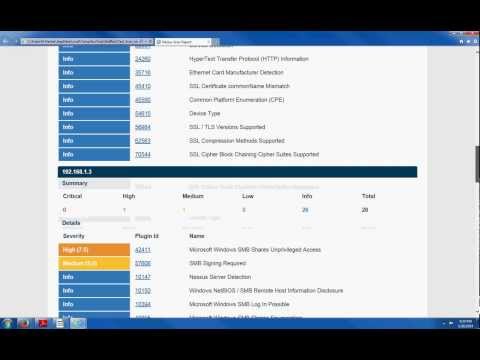
Nessus is one of the many vulnerability scanners used during vulnerability assessments and penetration testing engagements, including malicious attacks. This video will focus on this vulnerability scanner, discussing the fundamentals that one needs to have before getting started with the tool, the different scanning capabilities that it provides, what it takes to run the tool and how results appear once scans are complete.
Ethical Hacking Course | Cyber security | Information Security | Class 1 - Hindi
What is Reconnaissance | What is Information Gathering | Whois and Reverse Whois | Class 2 - Hindi
DNS Reconnaissance and Footprinting | What is DNS Footprinting | IP to location | Class 3 - Hindi
Hackers Online Information Gathering Tools | Online Hackers Tools | Class - 4
Hackers Search Engine Shodan | The Best Internet Search Engines Used by Hackers | Class - 5 Hindi
Open-Source Intelligence Gathering and Analysis | OSINT Framework | How to use SpiderFoot | Class 6
Google Hacking Database (ghdb) | Exploring Google Hacking Techniques | Google Dorks | Class 7 Hindi
How Hackers Trace Your IP Address | Grabify IP Logger| IP Grabber | GetNtoify | Class 8 - Hindi
Passive Information Gathering with Maltego | How to Use Maltego to Do Reconnaissance |Class 9 Hindi
Ethical Hacking Course in Hindi
Oracle VM VirtualBox: Hacking lab setup for Hackers
Kali Linux Basic Fundamentals | Kali Linux Basic Commands
Oracle VM VirtualBox: Hacking lab setup for Hackers
Kali Linux Basic Fundamentals
PLEASE SUBSCRIBE & FOLLOW ;-)
Get More Details
Nessus is one of the many vulnerability scanners used during vulnerability assessments and penetration testing engagements, including malicious attacks. This video will focus on this vulnerability scanner, discussing the fundamentals that one needs to have before getting started with the tool, the different scanning capabilities that it provides, what it takes to run the tool and how results appear once scans are complete.
Ethical Hacking Course | Cyber security | Information Security | Class 1 - Hindi
What is Reconnaissance | What is Information Gathering | Whois and Reverse Whois | Class 2 - Hindi
DNS Reconnaissance and Footprinting | What is DNS Footprinting | IP to location | Class 3 - Hindi
Hackers Online Information Gathering Tools | Online Hackers Tools | Class - 4
Hackers Search Engine Shodan | The Best Internet Search Engines Used by Hackers | Class - 5 Hindi
Open-Source Intelligence Gathering and Analysis | OSINT Framework | How to use SpiderFoot | Class 6
Google Hacking Database (ghdb) | Exploring Google Hacking Techniques | Google Dorks | Class 7 Hindi
How Hackers Trace Your IP Address | Grabify IP Logger| IP Grabber | GetNtoify | Class 8 - Hindi
Passive Information Gathering with Maltego | How to Use Maltego to Do Reconnaissance |Class 9 Hindi
Ethical Hacking Course in Hindi
Oracle VM VirtualBox: Hacking lab setup for Hackers
Kali Linux Basic Fundamentals | Kali Linux Basic Commands
Oracle VM VirtualBox: Hacking lab setup for Hackers
Kali Linux Basic Fundamentals
PLEASE SUBSCRIBE & FOLLOW ;-)
Get More Details
Комментарии
 0:13:06
0:13:06
 0:17:11
0:17:11
 0:17:40
0:17:40
 0:05:44
0:05:44
 0:13:20
0:13:20
 0:16:33
0:16:33
 0:28:21
0:28:21
 0:41:57
0:41:57
 0:07:13
0:07:13
 0:10:08
0:10:08
 0:13:05
0:13:05
 0:09:46
0:09:46
 0:22:04
0:22:04
 0:14:56
0:14:56
 0:12:37
0:12:37
 0:27:39
0:27:39
 0:20:04
0:20:04
 0:10:39
0:10:39
 0:13:43
0:13:43
 0:13:26
0:13:26
 0:23:15
0:23:15
 0:30:50
0:30:50
 0:05:25
0:05:25
 0:15:18
0:15:18