filmov
tv
[Cybersecurity Essentials] Packet Tracer - Communicating in a Cyber World
Показать описание
Background
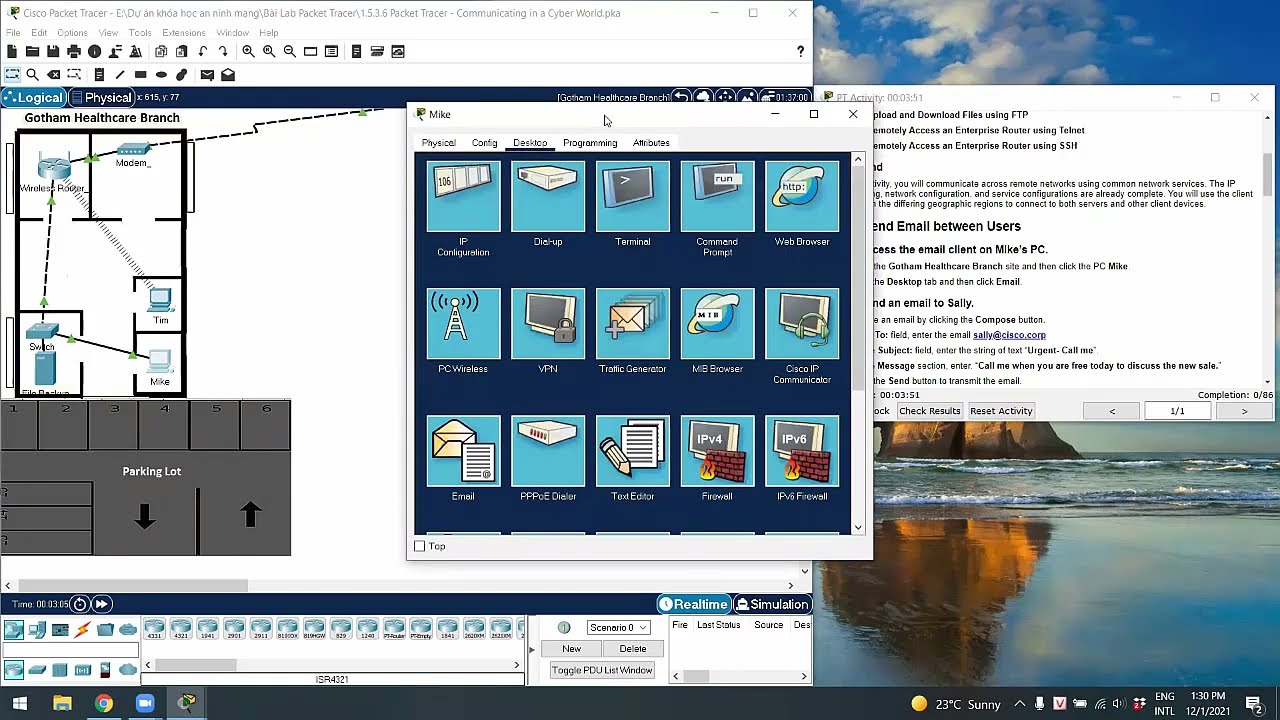
In this activity, you will communicate across remote networks using common network services. The IP addressing, network configuration, and service configurations are already complete. You will use the client devices in the differing geographic regions to connect to both servers and other client devices.
Objectives
Part 1: Send Email between Users
Part 2: Upload and Download Files using FTP
Part 3: Remotely Access an Enterprise Router using Telnet
Part 4: Remotely Access an Enterprise Router using SSH
In this activity, you will communicate across remote networks using common network services. The IP addressing, network configuration, and service configurations are already complete. You will use the client devices in the differing geographic regions to connect to both servers and other client devices.
Objectives
Part 1: Send Email between Users
Part 2: Upload and Download Files using FTP
Part 3: Remotely Access an Enterprise Router using Telnet
Part 4: Remotely Access an Enterprise Router using SSH
Cybersecurity Essentials Packet Tracer - Creating a Cyber World
[Cybersecurity Essentials] Packet Tracer - Creating a Cyber World
[Cybersecurity Essentials] Packet Tracer - Exploring File and Data Encryption
[Cybersecurity Essentials] Packet Tracer - Communicating in a Cyber World
Cybersecurity Essentials Packet Tracer - Communicating in a Cyber World.
Cisco Cybersecurity Essentials 7.4.2.4 Server Firewalls and Router ACLs | Packet Tracer demo Lab10
Cybersecurity Essentials Packet Tracer 2.5.2.6 - Exploring File and Data Encryption
1.Build a Home Network by Cisco Packet Tracer | Cybersecurity Essentials Course
How to Learn Hacking in 2025 | The FASTEST Way to Learn Hacking in 2025 | Become a Hacker in 2025
2.Investigate a Threat Landscape | Cybersecurity Essentials Lab
7.4.2.4 Packet Tracer - Server Firewalls and Router ACLs
Cybersecurity Essentials Packet Tracer 3.3.2.7 - Configuring WEP/WPA2 PSK/WPA2 RADIUS
1.5.3.6 Packet Tracer - Communicating in a Cyber World - Step by Step Guide
Cybersecurity Essentials Packet Tracer 2.5.2.7 - Using File and Data Integrity Checks
1.5.3.5 Packet Tracer - Creating a Cyber World
4.Explore File and Data Encryption | Cybersecurity Essentials Lab
Cisco Cybersecurity Essentials 1.5.3.6 Communicating in a Cyber World | Packet Tracer demonstration
Cybersecurity Essentials Packet Tracer 4.3.3.3 – Configuring VPN Transport Mode
1.5.3.6 Packet Tracer - Communicating in a Cyber World
Cybersecurity Essentials Packet Tracer 2 5 2 4 Install a Virtual Machine on a Personal Computer
How to solve all Packet Tracer exercises for the Cisco Cybersecurity Essentials course
Cisco Cybersecurity Essentials 8.3.1.3 Skills Integrated Challenge | Packet Tracer demonstration
3.File and Data Integrity Checks | Cybersecurity Essentials Lab
Cisco Packet Tracer | Everything You Need to Know
Комментарии
 0:34:17
0:34:17
![[Cybersecurity Essentials] Packet](https://i.ytimg.com/vi/7HuVMWjeLSI/hqdefault.jpg) 0:13:55
0:13:55
![[Cybersecurity Essentials] Packet](https://i.ytimg.com/vi/-x5SNGPg9sU/hqdefault.jpg) 0:16:02
0:16:02
![[Cybersecurity Essentials] Packet](https://i.ytimg.com/vi/OGSafqPxtqo/hqdefault.jpg) 0:15:37
0:15:37
 0:25:37
0:25:37
 0:10:02
0:10:02
 0:25:58
0:25:58
 0:26:24
0:26:24
 0:06:18
0:06:18
 0:15:51
0:15:51
 0:05:52
0:05:52
 0:31:34
0:31:34
 0:09:23
0:09:23
 0:38:46
0:38:46
 0:14:57
0:14:57
 0:10:55
0:10:55
 0:10:22
0:10:22
 0:19:46
0:19:46
 0:09:11
0:09:11
 0:22:17
0:22:17
 1:40:53
1:40:53
 0:20:16
0:20:16
 0:10:36
0:10:36
 0:17:10
0:17:10