filmov
tv
AWS Security | Automate Key Rotation for IAM Users | Best Practices

Показать описание
What is AWS Access KEY Rotation?
How should admins do Key rotation?
How can we automate Access Key rotation using AWS APIs via Python & Lambda?
Steps involved in AWS Access Key Rotation.
&&
-----------------------------------------------------------
I would request to look at our playlists to learn systematically for AWS Certifications ---
&&&
++++++++++++++++++++++++++++++++++++++++
&
++++++++++++++++++++++++++++++++++++++++
How should admins do Key rotation?
How can we automate Access Key rotation using AWS APIs via Python & Lambda?
Steps involved in AWS Access Key Rotation.
&&
-----------------------------------------------------------
I would request to look at our playlists to learn systematically for AWS Certifications ---
&&&
++++++++++++++++++++++++++++++++++++++++
&
++++++++++++++++++++++++++++++++++++++++
AWS Security | Automate Key Rotation for IAM Users | Best Practices
AWS Supports You - Identifying and Mitigating Aged IAM Access Keys
AWS Supports You: Securing Your Identity and Access Management Access Keys
AWS Security Hub Automated Response And Remediation Tutorial! Learn Cloud Security Now!
Security Automation using AWS Management Tools
An Overview of AWS Security Hub | Amazon Web Services
AWS re:Invent 2016: Automated Governance of Your AWS Resources (DEV302)
AWS re:Invent 2019: Automate your security on AWS (MKT204)
AWS Certified Solutions Architect Professional Exam Questions Dumps - JULY 2024 - Part 2 (SAP-C02)
Automate Container Security Using DevOps Processes on AWS with Trend Micro
Encryption and Key Management in AWS
AWS Security - AWS Key Management Service | Fully Visualized
AWS re:Inforce 2019: Automate Compliance Verification on AWS Using Provable Security (GRC301)
AWS re:Invent 2018: Five New Security Automations Using AWS Security Services & Open Source (SEC...
AWS re:Invent 2016: 5 Security Improvements You Can Make by Using CloudWatch and AWS Rules (SAC401)
Back to Basics: Secrets Management
Achieving Continuous Compliance using AWS Config
AWS Summit SF 2022 - Using AWS Key Management Service for data protection (SEC303)
Secure Your AWS API Gateway with API Keys | AWS Tutorial
What are hardware security modules (HSM), why we need them and how they work.
AWS Security by Design
AWS re:Invent 2020: AWS security: Where we’ve been, where we’re going
AWS Security Hub Deep Dive
AWS re:Invent 2022 - AWS data protection: Using locks, keys, signatures, and certificates (SEC212)
Комментарии
 0:22:16
0:22:16
 0:39:38
0:39:38
 0:42:45
0:42:45
 0:17:14
0:17:14
 0:49:45
0:49:45
 0:09:57
0:09:57
 0:49:41
0:49:41
 0:56:00
0:56:00
 1:35:06
1:35:06
 0:33:32
0:33:32
 0:35:16
0:35:16
 0:50:14
0:50:14
 0:47:19
0:47:19
 1:00:24
1:00:24
 0:59:16
0:59:16
 0:04:35
0:04:35
 0:18:51
0:18:51
 0:51:27
0:51:27
 0:15:01
0:15:01
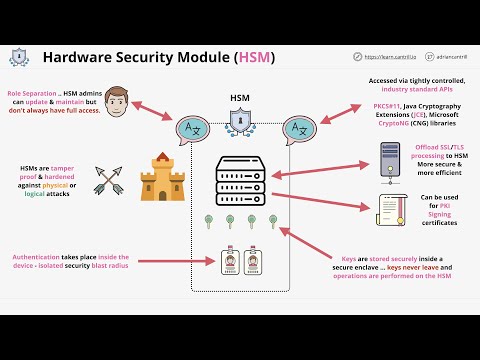 0:06:40
0:06:40
 0:43:32
0:43:32
 0:56:42
0:56:42
 0:08:40
0:08:40
 0:55:13
0:55:13