filmov
tv
Two Factor Authentication Explained in a Minute | Cyber Security | Data Protection #shorts

Показать описание
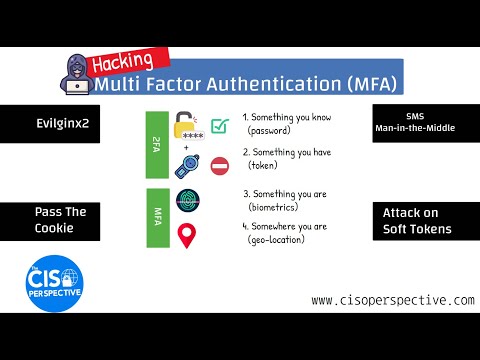
Two-factor authentication (2FA) is a robust security measure that adds an extra layer of protection to digital accounts beyond the traditional password system. It requires users to provide two different forms of identification before gaining access, typically combining something they know (like a password) with something they have (such as a mobile device or hardware token).
This method significantly enhances security by making it harder for unauthorized users to breach accounts, even if they manage to obtain login credentials. 2FA plays a pivotal role in safeguarding sensitive information, financial transactions, and personal data in an increasingly digital world where cyber threats are prevalent.
Its importance cannot be overstated as it mitigates the risks associated with password theft, phishing attacks, and unauthorized access, thereby fortifying the overall security posture of individuals and organizations alike.
What is a Cyberattack?
A Cyberattack is any offensive manoeuvre that targets computer information systems, computer networks, infrastructures, or personal computer devices. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorisation, potentially with malicious intent. Depending on the context, cyberattacks can be part of cyber warfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, societies, or organisations, and it may originate from an anonymous source. A product that facilitates a cyberattack is sometimes called a cyber weapon.
Why is Cybersecurity important?
In today’s connected world, everyone benefits from cyber defence programs. At an individual level, a cybersecurity attack can result in everything from identity theft, to extortion attempts, to the loss of important data like photos or documents. Cyber security is crucial because it involves everything that relates to protecting our data from cyber attackers.
What is Phishing?
Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information or to install malware on the victim’s machine. Phishing is a common type of cyber attack that everyone should learn about in order to protect themselves.
______________________________________________________________________________
About SCALER:
A transformative tech school, creating talent with impeccable skills. Upskill and Create Impact.
📌 Follow us on Social and be a part of an amazing tech community📌
🔔 Hit that bell icon to get notified of all our new videos 🔔
If you liked this video, please don't forget to like and comment. Never miss out on our exclusive videos to help boost your coding career! Subscribe to Scaler now!
This method significantly enhances security by making it harder for unauthorized users to breach accounts, even if they manage to obtain login credentials. 2FA plays a pivotal role in safeguarding sensitive information, financial transactions, and personal data in an increasingly digital world where cyber threats are prevalent.
Its importance cannot be overstated as it mitigates the risks associated with password theft, phishing attacks, and unauthorized access, thereby fortifying the overall security posture of individuals and organizations alike.
What is a Cyberattack?
A Cyberattack is any offensive manoeuvre that targets computer information systems, computer networks, infrastructures, or personal computer devices. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorisation, potentially with malicious intent. Depending on the context, cyberattacks can be part of cyber warfare or cyberterrorism. A cyberattack can be employed by sovereign states, individuals, groups, societies, or organisations, and it may originate from an anonymous source. A product that facilitates a cyberattack is sometimes called a cyber weapon.
Why is Cybersecurity important?
In today’s connected world, everyone benefits from cyber defence programs. At an individual level, a cybersecurity attack can result in everything from identity theft, to extortion attempts, to the loss of important data like photos or documents. Cyber security is crucial because it involves everything that relates to protecting our data from cyber attackers.
What is Phishing?
Phishing attacks are the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information or to install malware on the victim’s machine. Phishing is a common type of cyber attack that everyone should learn about in order to protect themselves.
______________________________________________________________________________
About SCALER:
A transformative tech school, creating talent with impeccable skills. Upskill and Create Impact.
📌 Follow us on Social and be a part of an amazing tech community📌
🔔 Hit that bell icon to get notified of all our new videos 🔔
If you liked this video, please don't forget to like and comment. Never miss out on our exclusive videos to help boost your coding career! Subscribe to Scaler now!
 0:02:07
0:02:07
 0:08:12
0:08:12
 0:00:44
0:00:44
 0:01:59
0:01:59
 0:12:34
0:12:34
 0:04:48
0:04:48
 0:12:15
0:12:15
 0:13:08
0:13:08
 0:04:16
0:04:16
 0:06:43
0:06:43
 0:01:43
0:01:43
 0:14:04
0:14:04
 0:05:05
0:05:05
 0:05:25
0:05:25
 0:06:32
0:06:32
 0:13:16
0:13:16
 0:17:42
0:17:42
 0:10:36
0:10:36
 0:04:03
0:04:03
 0:06:36
0:06:36
 0:16:38
0:16:38
 0:10:16
0:10:16
 0:04:47
0:04:47
 0:00:27
0:00:27