filmov
tv
Malware Analysis & Threat Intel: UAC Bypasses

Показать описание
🔥YOUTUBE ALGORITHM ➡ Like, Comment, & Subscribe!
Malware Analysis & Threat Intel: UAC Bypasses
Threat Intelligence 101 with Sophos MDR (Ep. #3): Malware analysis
Malware Analysis II: Traffic & Log Analysis (Threat Intelligence)
Cybersecurity Threat Hunting Explained
Identify Unknown Malware Using Four Free Threat Intelligence Services
Threat Intelligence 101 with Sophos MDR (Ep. #2): Analysis & Clustering
Threat Intelligence and the Limits of Malware Analysis with Joe Slowik - SANS CTI Summit 2020
GrayHat 2020 - Threat Intelligence, The Malware Analysis Way - Felipe Durate
ESET + Intel: Driving the Future of AI-Powered Cybersecurity
ANY.RUN – Real-Time Malware Analysis and Threat Intelligence
Cyber Threat Intel war stories and day to day “best” practices
little-known threat intelligence trick to detect the malware country of origin
THREAT INTELLIGENCE THREATENING INTEL OPERATIONS
SANS Threat Analysis Rundown | Katie Nickels
Threat Intelligence and Incident Response
E 01 | Houdini Phishing Campaign 1/3 | Threat Intelligence & Malware Analysis
Tracking Cybercrime on Telegram
Practical Malware Analysis Essentials for Incident Responders
The Cycle of Cyber Threat Intelligence
What Is Cyber Threat Intelligence?
How Threat Intelligence Helps You Combat Targeted Malware
Threat intelligence explained
Sweet New Threat Intel Just Dropped
Ransomware, Threat Hunting and Threat Intelligence
Комментарии
 0:33:00
0:33:00
 0:16:39
0:16:39
 0:09:03
0:09:03
 0:06:51
0:06:51
 0:17:41
0:17:41
 0:12:48
0:12:48
 0:26:52
0:26:52
 1:57:51
1:57:51
 0:02:01
0:02:01
 0:01:52
0:01:52
 0:15:41
0:15:41
 0:06:24
0:06:24
 0:26:50
0:26:50
 0:58:44
0:58:44
 0:58:49
0:58:49
 0:11:47
0:11:47
 0:23:26
0:23:26
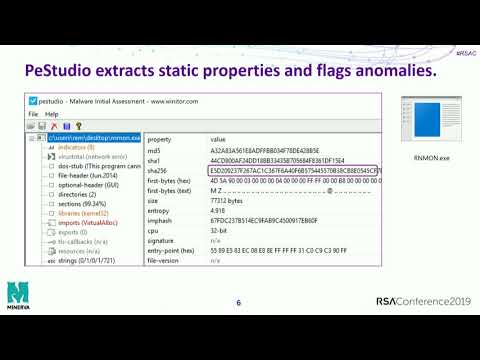 0:50:49
0:50:49
 1:00:27
1:00:27
 0:05:42
0:05:42
 0:37:28
0:37:28
 0:39:05
0:39:05
 0:12:00
0:12:00
 0:17:55
0:17:55