filmov
tv
OAuth client credentials flow

Показать описание
00:00 What is the OAuth client credentials flow?
00:54 OAuth client credentials walkthrough
03:05 conclusion
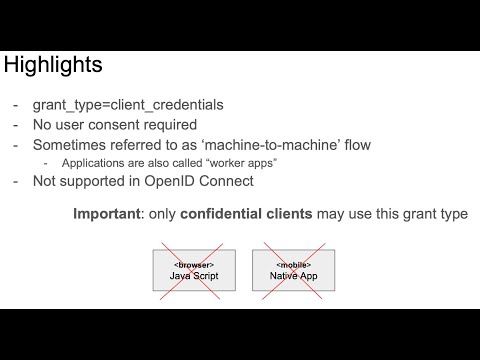
The OAuth client credentials flow was primarily designed for machine to machine communication (e.g for service account). It is sometimes also referred to as two-legged OAuth because there is no natural person involved. The idea is that the application exchanges a client id and a secret for an access token. Since no user is sitting in between, it does not make much sense to also request a refresh token. In fact it is even better for the authorization server to not send a refresh token because then access can be more easily revoked if needed.
OAuth 2.0 Client Credentials Flow (in plain English)
OAuth client credentials flow
Client Credentials Grant Flow is REALLY BAD
OAuth 2.0 client credentials and JWT explained along with keycloak demo
OAuth 2 Explained In Simple Terms
Oauth Client Credentials Flow for Service Apps
Oauth 2.0 Client Credential Flow | Microsoft Graph
OAuth 2.0 - Client Credentials
POSTMAN API OAUTH2 CLIENTCREDENTIALS
How to Use Client Credentials Flow with Spring Security
Salesforce Inbound - OAuth 2.0 Client Credentials Flow for Server-to-Server Integration
Make a Callout using OAuth 2.0 Client Credentials Flow | Named & External Credentials
OAuth 2.0 Client Credentials Flow [Ory Hydra, Golang]
OAuth 2.0 explained with examples
OAuth 2.0 Client Credentials Grant Flow
How to create Google OAuth Credentials (Client ID and Secret)
Salesforce OAuth 2 0 Client Credentials Flow to get Access Token
OAuth 2.0 Client Credentials Flow | Practical Example | How to implement oAuth2.0 Client Cred Flow?
An Illustrated Guide to OAuth and OpenID Connect
ID Tokens VS Access Tokens: What's the Difference?
Implement the OAuth 2.0 client credentials grant type flow in Apigee
Part 9 auth0 tutorial how to get token based on Client credentials flow
oAuth for Beginners - How oauth authentication🔒 works ?
OAuth 2.0 Client Credentials Flow in Salesforce
Комментарии
 0:05:34
0:05:34
 0:03:25
0:03:25
 0:02:16
0:02:16
 0:19:11
0:19:11
 0:04:32
0:04:32
 0:06:59
0:06:59
 0:10:37
0:10:37
 0:03:34
0:03:34
 0:01:00
0:01:00
 0:13:45
0:13:45
 0:06:11
0:06:11
 0:08:50
0:08:50
 0:23:12
0:23:12
 0:10:03
0:10:03
 0:00:26
0:00:26
 0:00:28
0:00:28
 0:03:47
0:03:47
 0:03:30
0:03:30
 0:16:36
0:16:36
 0:08:38
0:08:38
 0:05:01
0:05:01
 0:08:24
0:08:24
 0:10:43
0:10:43
 0:09:09
0:09:09