filmov
tv
SSL Certificate Revocation | The Backend Engineering Show

Показать описание
Certificates contain useful metadata including the public key, domain name, signature, etc. However, the private key can be leaked which causes the certificate to be invalid/dangerous to keep around. In that particular situation, we need a mechanism to revoke certificates and that is what I’m going to discuss in this show.
0:00 Intro
0:30 Why Certificates
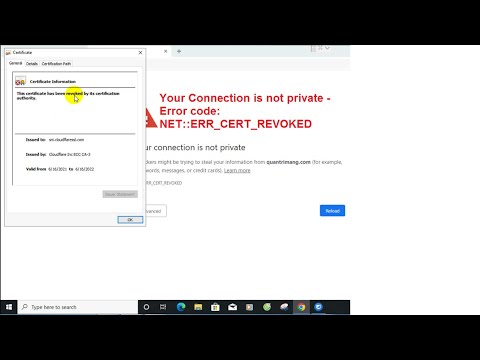
12:00 Certificates can go bad
14:50 Certificate Revocation Lists (CRLs)
18:30 OCSP (Online Certificate Status Protocol)
20:40 OCSP Stapling
24:30 Best certificates are short
26:30 Summary
Become a Member on YouTube
🔥 Members Only Content
Support my work on PayPal
🧑🏫 Courses I Teach
🏭 Backend Engineering Videos in Order
💾 Database Engineering Videos
🎙️Listen to the Backend Engineering Podcast
Gears and tools used on the Channel (affiliates)
🖼️ Slides and Thumbnail Design
Canva
🎙️ Mic Gear
Shure SM7B Cardioid Dynamic Microphone
Cloudlifter
XLR cables
Focusrite Audio Interface
📷 Camera Gear
Canon M50 Mark II
Micro HDMI to HDMI
Video capture card
AC Wall for constant power
Stay Awesome,
Hussein
0:00 Intro
0:30 Why Certificates
12:00 Certificates can go bad
14:50 Certificate Revocation Lists (CRLs)
18:30 OCSP (Online Certificate Status Protocol)
20:40 OCSP Stapling
24:30 Best certificates are short
26:30 Summary
Become a Member on YouTube
🔥 Members Only Content
Support my work on PayPal
🧑🏫 Courses I Teach
🏭 Backend Engineering Videos in Order
💾 Database Engineering Videos
🎙️Listen to the Backend Engineering Podcast
Gears and tools used on the Channel (affiliates)
🖼️ Slides and Thumbnail Design
Canva
🎙️ Mic Gear
Shure SM7B Cardioid Dynamic Microphone
Cloudlifter
XLR cables
Focusrite Audio Interface
📷 Camera Gear
Canon M50 Mark II
Micro HDMI to HDMI
Video capture card
AC Wall for constant power
Stay Awesome,
Hussein
Комментарии
 0:27:21
0:27:21
 0:03:00
0:03:00
 0:00:40
0:00:40
 0:00:27
0:00:27
 0:16:41
0:16:41
 0:08:22
0:08:22
 0:06:40
0:06:40
 0:02:08
0:02:08
 0:09:14
0:09:14
 0:03:28
0:03:28
 0:04:34
0:04:34
 0:01:10
0:01:10
 0:03:13
0:03:13
 0:09:42
0:09:42
 0:02:57
0:02:57
 0:06:30
0:06:30
 0:00:42
0:00:42
 0:01:27
0:01:27
 0:01:25
0:01:25
 0:04:54
0:04:54
 0:02:43
0:02:43
 0:04:45
0:04:45
 0:00:37
0:00:37
 0:03:05
0:03:05