filmov
tv
HACKERLOI.pdf

Показать описание
// Membership //
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
HACKERLOI.pdf
virus.pdf
How hackers hack with an image Trojan?!
how Hackers Remotely Control Any phone!? check if your phone is already hacked now!
watch how Hackers Remotely Control Any phone?! protect your phone from hackers now!
Remotely Control PCs with Reverse Shells!? Easy hacker tool
Remotely Control Any PC in 4 mins 59 seconds
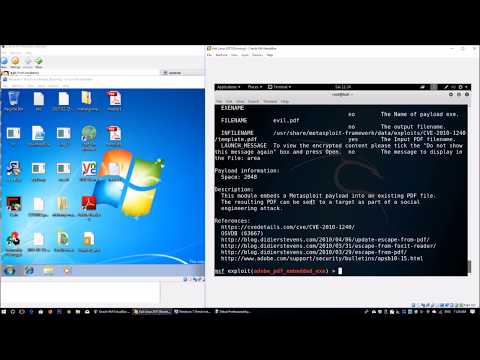
how hackers hack you using a pdf file
How Hackers Remotely Control Any PC?!
remotely control any PC with a shortcut file?!
How hackers Hack Using PDF | Demo Video | Ethical Hacking | 2022
How Hackers Launch PDF Virus File And How We Can Protect Ourselves! (Cybersecurity)
Best Free Windows Remote Access Tool!
🔥COMO los piratas informáticos HACKEAN PC usando PDF☢️HACKERLOI
how hackers bypass file upload restrictions!
how hackers get any device location?! do not click this button on your browser!
Access Android with Metasploit Kali (Cybersecurity)
how hackers hack any websites in minutes?!
Simple Penetration Testing Tutorial for Beginners!
Metasploit For Beginners - How To Scan And Pwn A Computer | Learn From A Pro Hacker
Reverse engineering malware in PDF files
reset any email password for free! (Cybersecurity tutorial)
Remotely Control Any PC With This Simple Tool!
PDF Hack! All Conversions For Free #shorts #shortvideo
Комментарии
 0:06:53
0:06:53
 0:10:20
0:10:20
 0:07:39
0:07:39
 0:07:07
0:07:07
 0:10:11
0:10:11
 0:09:56
0:09:56
 0:04:59
0:04:59
 0:03:28
0:03:28
 0:09:47
0:09:47
 0:08:04
0:08:04
 0:07:37
0:07:37
 0:11:53
0:11:53
 0:09:22
0:09:22
 0:06:35
0:06:35
 0:05:39
0:05:39
 0:07:26
0:07:26
 0:13:05
0:13:05
 0:23:17
0:23:17
 0:15:25
0:15:25
 0:10:03
0:10:03
 0:00:59
0:00:59
 0:06:58
0:06:58
 0:04:44
0:04:44
 0:00:16
0:00:16