filmov
tv
Features for Building a Data Loss Prevention (DLP) System
Показать описание
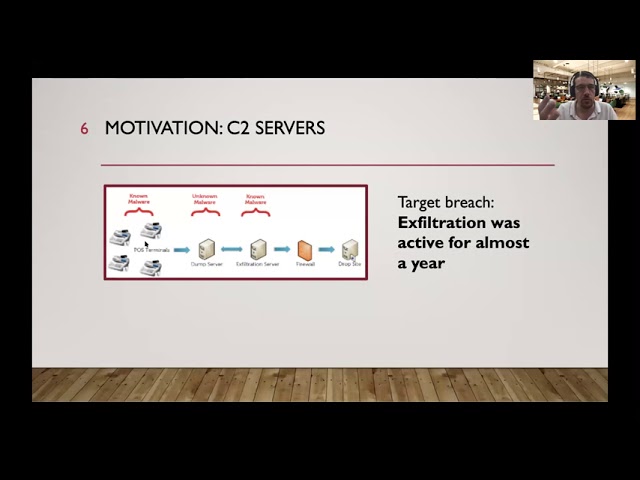
Target’s infamous breach marked one of the most influential cyber attacks of all times when some 40 million credit card numbers were stolen and sold in the darknet (fall 2013). To perform such an attack, a control and command (C&C or C2) server was placed outside the corporate network to control corporate computers.
In this talk, I'll describe details of modern covert communication channels established for malicious intentions, and describe two algorithms for a Data Loss Prevention (DLP) system.
In this talk, I'll describe details of modern covert communication channels established for malicious intentions, and describe two algorithms for a Data Loss Prevention (DLP) system.
 0:05:22
0:05:22
 0:28:14
0:28:14
 0:13:54
0:13:54
 0:35:46
0:35:46
 0:12:28
0:12:28
 0:01:55
0:01:55
 0:39:51
0:39:51
 0:03:41
0:03:41
 1:29:37
1:29:37
 0:07:35
0:07:35
 0:06:41
0:06:41
 0:01:43
0:01:43
 0:00:45
0:00:45
 0:01:50
0:01:50
 0:21:19
0:21:19
 0:04:19
0:04:19
 0:03:54
0:03:54
 1:00:46
1:00:46
 0:42:19
0:42:19
 0:02:00
0:02:00
 1:12:36
1:12:36
 0:17:39
0:17:39
 0:04:58
0:04:58
 11:20:10
11:20:10