filmov
tv
3 Handmade Linux x86 executables: Loops and conditionals

Показать описание
This video series:
The Intel manual:
3 Handmade Linux x86 executables: Loops and conditionals
2 Handmade Linux x86 executables: Hello, world
5 Handmade Linux x86 executables: Functions and strings
1 Handmade Linux x86 executables: ELF header
7 Handmade Linux x86 executables: DMQ compiler
6 Handmade Linux x86 executables: Stack and SIB
8 Handmade Linux x86 executables: Postfix calculator
No really, how does Linux run executables?
4 Handmade Linux x86 executables: ModR/M and numeric output
What are Executables? | bin 0x00
In-depth: ELF - The Extensible & Linkable Format
Linux Executables: From Assembly to C and Rust
Run Binary Elf Executable File on Android
SmithForth workings
Writing a Linux ELF Binary by Hand
x86 Assembly and Shellcoding - 8 Binary to Hexadecimal
Linux Debuginfo Formats - DWARF, ELF, dwo, dwp - What are They All? - Greg Law - CppCon 2022
File Signatures
Linux Executable Symbol Relocation Explained
How to make an operating system!! (boot sector)
Before Main: How Executables Work on Linux
ASSEMBLING x86_64 instructions BY HAND | Compiler from scratch, for fun :P | 054
Gopher2600 (DWARF debugging)
PIC GOT PLT OMG: how does the procedure linkage table work in linux?
Комментарии
 0:09:49
0:09:49
 0:06:40
0:06:40
 0:19:39
0:19:39
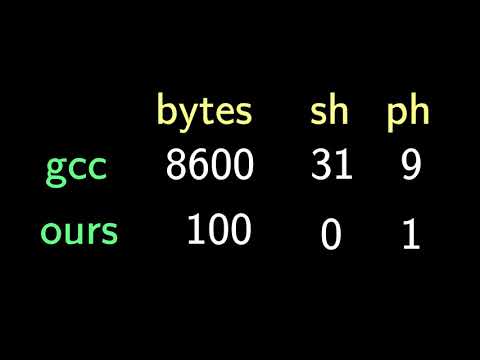 0:11:19
0:11:19
 0:12:15
0:12:15
 0:13:49
0:13:49
 0:17:33
0:17:33
 0:08:37
0:08:37
 0:20:18
0:20:18
 0:08:35
0:08:35
 0:19:02
0:19:02
 1:13:47
1:13:47
 0:01:17
0:01:17
 0:32:55
0:32:55
 0:59:11
0:59:11
 0:01:25
0:01:25
 1:02:34
1:02:34
 0:01:34
0:01:34
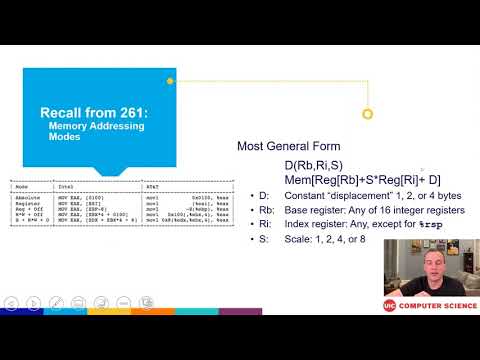 0:27:23
0:27:23
 0:16:31
0:16:31
 1:32:05
1:32:05
 4:44:30
4:44:30
 0:00:23
0:00:23
 0:49:35
0:49:35