filmov
tv
What is Nmap? How to Use Nmap? | Nmap Tutorials for Beginners

Показать описание
Nmap (Network Mapper) is an open-source and highly versatile network scanning tool used for network exploration, security auditing, and vulnerability assessment. It was originally developed by Gordon Lyon (also known as Fyodor) and is actively maintained and updated by a community of developers.
Using Nmap (Network Mapper) effectively can help you discover hosts, open ports, services, and potential vulnerabilities on a network. Here's a guide on how to use Nmap tutorial for beginners in Kali Linux:
Basic Scan:
Open a terminal or command prompt.
Run the following command: nmap "target". Replace "target" with the IP address or hostname of the target system.
Nmap will perform a default scan and display open ports and services on the target system.
Specifying Ports:
By default, Nmap scans the 1,000 most common ports. You can specify ports or port ranges using the -p option. Example: nmap -p 80,443 "target".
Use hyphens to specify a range of ports. Example: nmap -p 1-100 "target".
TCP SYN Scan:
Use the -sS option for a fast and stealthy TCP SYN scan. Example: nmap -sS "target".
This scan sends SYN packets to the target ports, and based on the response, determines whether the port is open, closed, or filtered.
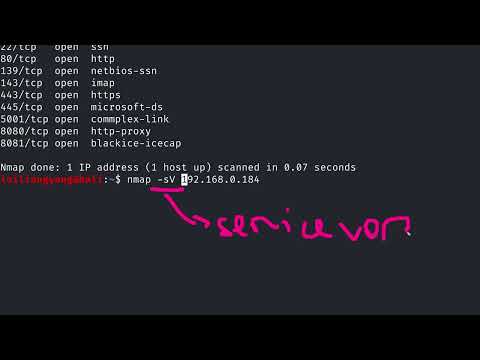
Service and Version Detection:
Use the -sV option to enable service detection. Example: nmap -sV "target".
Nmap will attempt to detect the version and type of services running on open ports.
Operating System Detection:
Use the -O option for OS detection. Example: nmap -O "target".
Nmap will try to identify the operating system running on the target system based on various characteristics and network responses.
Script Scanning:
Nmap has a powerful scripting engine called NSE (Nmap Scripting Engine). Use the --script option to specify scripts. Example: nmap --script script-name "target".
Nmap provides a wide range of scripts for vulnerability scanning, information gathering, and more. Explore the available scripts and their functionalities in the Nmap documentation.
Remember to use Nmap responsibly, with proper authorization, and in compliance with legal and ethical guidelines. Always obtain permission before scanning systems that are not under your control. Happy hacking don't forget to Subscribe!
Disclaimer: All demonstrations in this video are conducted on authorized systems with explicit permission. No support for illegal activities. Ethical hacking means responsible vulnerability discovery. Misusing techniques for unauthorized or malicious purposes is strictly discouraged. Exercise sound judgment and respect others' security and privacy. Seek permission for any hacking-related activities. Subscribe for more ethical hacking content!
#Nmap #NetworkScanning #EthicalHacking #PenetrationTesting #InfoSec #Cybersecurity #NetworkSecurity #VulnerabilityScanning #ITSecurity #NetworkDefense #NetworkDiscovery #PortScanning #NetworkAnalysis #ITAuditing #NetworkMapping #PacketAnalysis #NetworkForensics #NetworkVisualization #NetworkProtocolAnalysis #NetworkProtection
Using Nmap (Network Mapper) effectively can help you discover hosts, open ports, services, and potential vulnerabilities on a network. Here's a guide on how to use Nmap tutorial for beginners in Kali Linux:
Basic Scan:
Open a terminal or command prompt.
Run the following command: nmap "target". Replace "target" with the IP address or hostname of the target system.
Nmap will perform a default scan and display open ports and services on the target system.
Specifying Ports:
By default, Nmap scans the 1,000 most common ports. You can specify ports or port ranges using the -p option. Example: nmap -p 80,443 "target".
Use hyphens to specify a range of ports. Example: nmap -p 1-100 "target".
TCP SYN Scan:
Use the -sS option for a fast and stealthy TCP SYN scan. Example: nmap -sS "target".
This scan sends SYN packets to the target ports, and based on the response, determines whether the port is open, closed, or filtered.
Service and Version Detection:
Use the -sV option to enable service detection. Example: nmap -sV "target".
Nmap will attempt to detect the version and type of services running on open ports.
Operating System Detection:
Use the -O option for OS detection. Example: nmap -O "target".
Nmap will try to identify the operating system running on the target system based on various characteristics and network responses.
Script Scanning:
Nmap has a powerful scripting engine called NSE (Nmap Scripting Engine). Use the --script option to specify scripts. Example: nmap --script script-name "target".
Nmap provides a wide range of scripts for vulnerability scanning, information gathering, and more. Explore the available scripts and their functionalities in the Nmap documentation.
Remember to use Nmap responsibly, with proper authorization, and in compliance with legal and ethical guidelines. Always obtain permission before scanning systems that are not under your control. Happy hacking don't forget to Subscribe!
Disclaimer: All demonstrations in this video are conducted on authorized systems with explicit permission. No support for illegal activities. Ethical hacking means responsible vulnerability discovery. Misusing techniques for unauthorized or malicious purposes is strictly discouraged. Exercise sound judgment and respect others' security and privacy. Seek permission for any hacking-related activities. Subscribe for more ethical hacking content!
#Nmap #NetworkScanning #EthicalHacking #PenetrationTesting #InfoSec #Cybersecurity #NetworkSecurity #VulnerabilityScanning #ITSecurity #NetworkDefense #NetworkDiscovery #PortScanning #NetworkAnalysis #ITAuditing #NetworkMapping #PacketAnalysis #NetworkForensics #NetworkVisualization #NetworkProtocolAnalysis #NetworkProtection
Комментарии
 0:17:09
0:17:09
 0:04:41
0:04:41
 0:13:23
0:13:23
 0:00:12
0:00:12
 0:06:17
0:06:17
 0:07:32
0:07:32
 0:09:43
0:09:43
 0:04:04
0:04:04
 0:00:42
0:00:42
 0:04:21
0:04:21
 0:44:03
0:44:03
 0:05:35
0:05:35
 0:02:06
0:02:06
 1:23:59
1:23:59
 0:15:51
0:15:51
 0:00:49
0:00:49
 0:08:34
0:08:34
 0:24:26
0:24:26
 0:03:33
0:03:33
 0:07:40
0:07:40
 0:00:14
0:00:14
 0:00:37
0:00:37
 0:00:38
0:00:38
 0:00:16
0:00:16