filmov
tv
NETWORK SECURITY - DES (DATA ENCRYPTION STANDARD) ALGORITHM

Показать описание
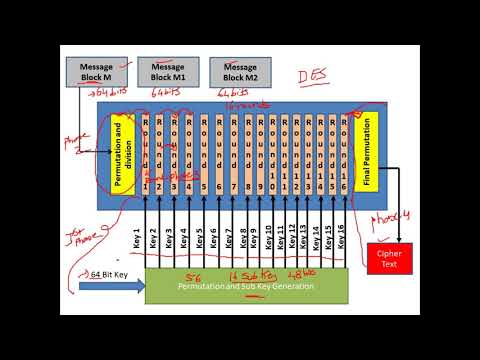
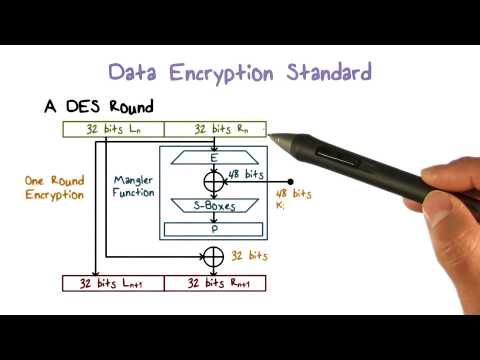
DES algorithm follows the Feistel Structure
Most of the Block cipher algorithms follows Feistel Structure
BLOCK SIZE - 64 bits Plain Text
No. of Rounds - 16 Rounds
Key Size - 64 bits
Sub Key Size - 48 bits
No. of Sub Keys - 16 Sub Keys
Cipher Text - 64 bits
----------------------------------------------------------------------
Hi Friends,
SUPER THANKS is enabled by YouTube and if any viewer want to contribute any financial support (not mandatory) you can use this option (SUPER THANKS) which will be available just below the title of every video.
Thanks for your love and support towards our channel.
----------------------------------------------------------------------
Most of the Block cipher algorithms follows Feistel Structure
BLOCK SIZE - 64 bits Plain Text
No. of Rounds - 16 Rounds
Key Size - 64 bits
Sub Key Size - 48 bits
No. of Sub Keys - 16 Sub Keys
Cipher Text - 64 bits
----------------------------------------------------------------------
Hi Friends,
SUPER THANKS is enabled by YouTube and if any viewer want to contribute any financial support (not mandatory) you can use this option (SUPER THANKS) which will be available just below the title of every video.
Thanks for your love and support towards our channel.
----------------------------------------------------------------------
NETWORK SECURITY - DES (DATA ENCRYPTION STANDARD) ALGORITHM
DES ( Data Encryption Standard ) Algorithm Part -1 Explained in Hindi l Network Security
DES - Data Encryption Standard | Data Encryption Standard In Cryptography |DES Algorithm|Simplilearn
Simplified DES(Data Encryption Standard)(Information Security)
Working of DES with Example
DES Algorithm | Working of DES Algorithm | DES Encryption Process | Data Encryption Standard
Data Encryption Standard (DES) - Explained with an Example - Cryptography - CyberSecurity - CSE4003
Data Encryption Standard ( DES )
Wait ... even my phone charger can steal my data?
DES Encryption Example | DES Example Solution | How to solve DES example? | DES Example
#18 Data Encryption Standard ( DES ) Algorithm |CNS|
Data Encryption Standard
Simplified Data Encryption Standard (DES) Example
S-DES Key Generation || Simplified Data Encryption Standard || Computer Network Security
Simplified data encryption standard(S-DES) || S-DES key generation with figure || Shafiq Refat
Cryptography & Network Security - Data Encryption Standard (DES)
S-DES(Simplified-Data Encryption Standard)Encryption example || Computer Network Security.
DES Algorithm (Data Encryption Standard algorithm) | Complete Working | Types - Double & Triple ...
DES Numerical Illustration | Network Security
AES and DES Algorithm Explained | Difference between AES and DES | Network Security | Simplilearn
Network security: S-DES Algorithm (part 4/4)
Explaination of DES | Data Encryption Standard in Cryptography | Network Security
DES(Data Encryption Standard) encryption explaination || Computer Network Security
S Box
Комментарии
 0:49:38
0:49:38
 0:06:07
0:06:07
 0:16:30
0:16:30
 0:23:10
0:23:10
 0:13:11
0:13:11
 0:18:35
0:18:35
 0:51:39
0:51:39
 0:28:38
0:28:38
 1:08:50
1:08:50
 0:14:26
0:14:26
 0:09:31
0:09:31
 0:02:53
0:02:53
 0:44:01
0:44:01
 0:04:45
0:04:45
 0:04:48
0:04:48
 0:26:53
0:26:53
 0:09:26
0:09:26
 0:27:29
0:27:29
 0:25:40
0:25:40
 0:29:35
0:29:35
 0:21:43
0:21:43
 0:12:26
0:12:26
 0:05:10
0:05:10
 0:00:38
0:00:38