filmov
tv
CVE-2023-23397: Microsoft Outlook Elevation of Privilege Vulnerability
Показать описание
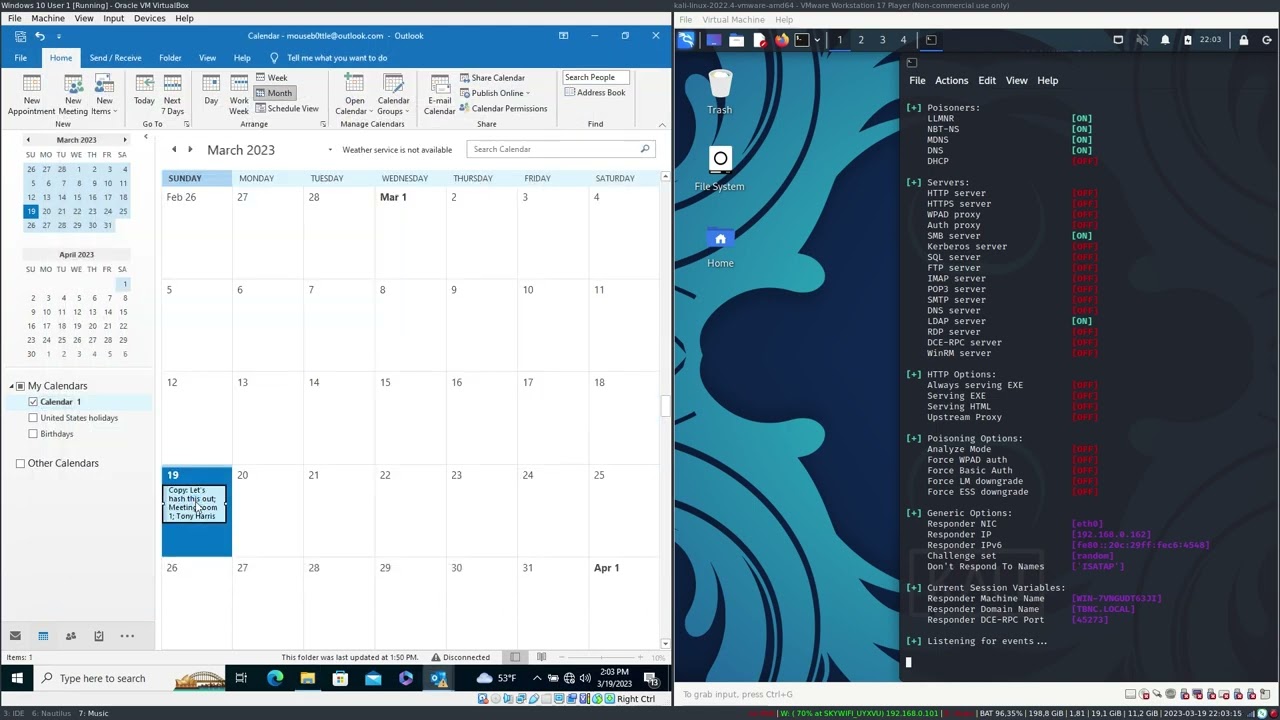
Demo of CVE-2023-23397. On the left is the victim opening a malicious Outlook appointment and on the right, the attacker's malicious SMB server steals their NTLM hash.
CVE-2023-23397: Microsoft Outlook Elevation of Privilege Vulnerability
How to remediate Microsoft Outlook Elevation of Privilege Vulnerability CVE-2023-23397 immediately !
OUTLOOK ELEVATION OF PRIVILEGE VULNERABILITY - CVE 2023 23397
CVE-2023-23397 Outlook Privilege Escalation Walkthrough
Microsoft Outlook Zero-Day Vulnerability- Elevation of Privilege Vulnerability CVE-2023-23397
Everything you need to know about the Outlook Exploit - Critical Vulnerability CVE-2023-23397
Digging into CVE-2023-23397
Microsoft Outlook NTLM Vulnerability | CVE-2023-23397 Demo
DarkRelay's POC and demo on CVE-2023-23397: Critical Microsoft Outlook vulnerability
Outlook PrivEsc Vulnerability CVE 2023 23397
Microsoft Outlook - Critical Vulnerability (CVE-2023-23397)
TryHackMe - Outlook NTLM Leak (CVE-2023-23397)
Microsoft Outlook NTLM Leak | Walkthrough | TryHackMe | CVE-2023-23397 Security Vulnerability
Russian Malicious Outlook Calendar Invites Targeting Ukraine (CVE-2023-23397) | Threat SnapShot
Microsoft Outlook Elevation of Privilege Vulnerability
CVE-2023-23397 Quick & Dirty PoC
Exploiting Outlook CVE-2023-23397 to Relay Credentials
PHISH Any Outlook User [Hands-on]! CVE-2023-23397
#WeeklyCTI - Critical Vulnerability in Microsoft Outlook Client
Live Hacking Outlook Schwachstelle CVE-2023-23397
Passworthashes durch ÖFFNEN einer E-Mail sammeln? (Die neue Outlook-Lücke CVE-2023-23397)
Outlook NTLM Hash leak || CVE-2023-23397
Outlook Elevation of Privilege CVE 2023-23397 | The AppSec Insiders Podcast Ep.12
Critical Outlook NTLM Vulnerability (CVE-2023-23397) | Security Spotlight
Комментарии
 0:00:25
0:00:25
 0:03:54
0:03:54
 0:04:47
0:04:47
 0:11:17
0:11:17
 0:01:01
0:01:01
 0:05:46
0:05:46
 0:09:56
0:09:56
 0:16:15
0:16:15
 0:02:25
0:02:25
 0:05:35
0:05:35
 0:02:22
0:02:22
 0:48:20
0:48:20
 0:06:07
0:06:07
 0:14:13
0:14:13
 0:01:49
0:01:49
 0:00:42
0:00:42
 0:10:17
0:10:17
 0:12:46
0:12:46
 0:34:49
0:34:49
 0:02:30
0:02:30
 0:09:15
0:09:15
 0:08:54
0:08:54
 0:01:00
0:01:00
 0:03:44
0:03:44